| Category | Microsoft Docs article | Related commit history on GitHub | Change details |
|---|---|---|---|
| admin | What Subscription Do I Have | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/admin/admin-overview/what-subscription-do-i-have.md | f1.keywords: -+ audience: Admin |
| admin | Test And Deploy Microsoft 365 Apps | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/admin/manage/test-and-deploy-microsoft-365-apps.md | You won't be able to deploy a single store app or Microsoft 365 Apps by partner 1. In the admin center, in the left nav, choose **Settings** and then **Integrated apps**. -2. Select **Upload custom apps**. Only a custom line of apps for Word, PowerPoint, Excel and Outlook is supported. +2. Select **Upload custom apps**. Only a custom line of apps for Word, PowerPoint, Excel, and Outlook is supported. 3. Upload the manifest file from your device or add a URL link. Some apps require you to add users before you can select Deploy. Updates for add-ins happen as follows: - **Office Store add-in**: When an admin selected an add-in from the Office Store, if an add-in updates in the Office Store, the next time the relevant Office applications start, the add-in will update. The web application can change at any time. > [!NOTE]-> For Word, Excel and PowerPoint use a [SharePoint App Catalog](https://dev.office.com/docs/add-ins/publish/publish-task-pane-and-content-add-ins-to-an-add-in-catalog) to deploy add-ins to users in an on-premises environment with no connection to Microsoft 365 and/or support for SharePoint add-ins required. For Outlook use Exchange control panel to deploy in an on-premises environment without a connection to Microsoft 365. +> For Word, Excel, and PowerPoint use a [SharePoint App Catalog](/sharepoint/dev/sp-add-ins/publish-sharepoint-add-ins) to deploy add-ins to users in an on-premises environment with no connection to Microsoft 365 and/or support for SharePoint add-ins required. For Outlook use Exchange control panel to deploy in an on-premises environment without a connection to Microsoft 365. ## Add-in states An add-in can be in either the **On** or **Off** state. |
| admin | Apply For A Fapiao | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/admin/services-in-china/apply-for-a-fapiao.md | f1.keywords: -+ audience: Admin If you want to change the Fapiao title, please send the Fapiao back to us and we  -2. If you forgot your login password, you can use your login email address to reset the password. The Fapiao management system will send a new password to your email address. You can use the new password to login. +2. If you forgot your login password, you can use your login email address to reset the password. The Fapiao management system will send a new password to your email address. You can use the new password to log in.  |
| admin | Download Software Licenses Csp | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/admin/setup/download-software-licenses-csp.md | f1.keywords: -+ audience: Admin |
| commerce | Manage Billing Profiles | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/commerce/billing-and-payments/manage-billing-profiles.md | Title: Understand billing profiles -+ audience: Admin f1.keywords: |
| commerce | Manage Payment Methods | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/commerce/billing-and-payments/manage-payment-methods.md | f1.keywords: -+ audience: Admin |
| commerce | Mexico Billing Info | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/commerce/billing-and-payments/mexico-billing-info.md | f1.keywords: -+ audience: Admin |
| commerce | Psd2 | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/commerce/billing-and-payments/psd2.md | f1.keywords: -+ audience: Admin |
| commerce | Tax Information | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/commerce/billing-and-payments/tax-information.md | f1.keywords: -+ audience: Admin |
| commerce | Understand Your Invoice | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/commerce/billing-and-payments/understand-your-invoice.md | Title: Understand your bill or invoice -+ audience: Admin f1.keywords: |
| commerce | Buy Or Edit An Add On | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/commerce/buy-or-edit-an-add-on.md | f1.keywords: -+ audience: Admin |
| commerce | Close Your Account | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/commerce/close-your-account.md | f1.keywords: -+ audience: Admin |
| commerce | Enter Your Product Key | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/commerce/enter-your-product-key.md | f1.keywords: -+ audience: Admin |
| commerce | Product Key Errors And Solutions | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/commerce/product-key-errors-and-solutions.md | f1.keywords: -+ audience: Admin |
| commerce | Purchases From Microsoft Open | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/commerce/purchases-from-microsoft-open.md | f1.keywords: -+ audience: Admin |
| commerce | Back Up Data Before Switching Plans | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/commerce/subscriptions/back-up-data-before-switching-plans.md | f1.keywords: -+ audience: Admin |
| commerce | Change Plans Manually | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/commerce/subscriptions/change-plans-manually.md | f1.keywords: -+ audience: Admin |
| commerce | Manage Self Service Signup Subscriptions | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/commerce/subscriptions/manage-self-service-signup-subscriptions.md | f1.keywords: -+ audience: Admin |
| commerce | Reactivate Your Subscription | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/commerce/subscriptions/reactivate-your-subscription.md | f1.keywords: -+ audience: Admin |
| commerce | Renew Your Subscription | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/commerce/subscriptions/renew-your-subscription.md | f1.keywords: -+ audience: Admin |
| commerce | Upgrade To Different Plan | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/commerce/subscriptions/upgrade-to-different-plan.md | f1.keywords: -+ audience: Admin |
| commerce | What If My Subscription Expires | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/commerce/subscriptions/what-if-my-subscription-expires.md | f1.keywords: -+ audience: Admin When your trial ends, you can't continue using Microsoft 365 for free. You have - **Buy Microsoft 365.** When your trial expires, it moves into the Expired stage, giving you another 30 days (for most trials, in most countries and regions) to purchase Microsoft 365. To learn how to convert your trial into a paid subscription, see [Buy a subscription from your free trial](../try-or-buy-microsoft-365.md#buy-a-subscription-from-your-free-trial). - **Extend your trial.** Need more time to evaluate Microsoft 365? In certain cases, you can [extend your trial](../extend-your-trial.md).-- **Cancel the trial or let it expire.** If you decide not to buy Microsoft 365, you can let your trial expire or [cancel it](cancel-your-subscription.md). Back up any data you want to keep. Soon after the 30-day Expired stage, your trial account information and data is permanently erased.+- **Cancel the trial or let it expire.** If you decide not to buy Microsoft 365, you can let your trial expire or [cancel it](cancel-your-subscription.md). Back up any data you want to keep. Soon after the 30-day Expired stage, your trial account information and data are permanently erased. > [!NOTE] > |
| compliance | Apply Retention Labels Automatically | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/apply-retention-labels-automatically.md | f1.keywords: Previously updated : Last updated : audience: Admin ms.localizationpriority: high-+ - M365-security-compliance - SPO_Content+search.appverid: - MOE150 - MET150 description: Create auto-labeling retention policies so you can automatically apply labels to retain what you need and delete what you don't description: Create auto-labeling retention policies so you can automatically ap > This scenario is not supported for [regulatory records](records-management.md#records) or default labels for an organizing structure such as a document set or library in SharePoint, or a folder in Exchange. These scenarios require a [published retention label policy](create-apply-retention-labels.md). One of the most powerful features of [retention labels](retention.md) is the ability to apply them automatically to content that matches specified conditions. In this case, people in your organization don't need to apply the retention labels. Microsoft 365 does the work for them.- + Auto-applying retention labels are powerful because:- + - You don't need to train your users on all of your classifications.- - You don't need to rely on users to classify all content correctly.- - Users no longer need to know about data governance policies - they can focus on their work.- + You can apply retention labels to content automatically when that content doesn't already have a retention label applied and contains sensitive information, keywords or searchable properties, or a match for [trainable classifiers](classifier-get-started-with.md). Now in preview, you can also automatically apply a retention label to cloud attachments that are stored in SharePoint or OneDrive. > [!TIP] The processes to automatically apply a retention label based on these conditions Use the following instructions for the two admin steps. > [!NOTE]-> Auto-policies use service-side labeling with conditions to automatically apply retention labels to items. You can also automatically apply a retention label with a label policy when you do the following: +> Auto-policies use service-side labeling with conditions to automatically apply retention labels to items. You can also automatically apply a retention label with a label policy when you do the following: > > - Apply a retention label to a document understanding model in SharePoint Syntex > - Apply a default retention label for SharePoint and Outlook Use the following instructions for the two admin steps. ## Before you begin -The global admin for your organization has full permissions to create and edit retention labels and their policies. If you aren't signing in as a global admin, see the permissions information for [records management](get-started-with-records-management.md#permissions) or [data lifeycle management](get-started-with-data-lifecycle-management.md#permissions-for-retention-policies-and-retention-labels), depending on the solution you're using. +The global admin for your organization has full permissions to create and edit retention labels and their policies. If you aren't signing in as a global admin, see the permissions information for [records management](get-started-with-records-management.md#permissions) or [data lifecycle management](get-started-with-data-lifecycle-management.md#permissions-for-retention-policies-and-retention-labels), depending on the solution you're using. Make sure you have [created the retention labels](file-plan-manager.md#create-retention-labels) you want to apply to items. Decide before you create your retention label policy whether it will be **adapti When you create an auto-apply policy, you select a retention label to automatically apply to content, based on the conditions that you specify. 1. In the [Microsoft Purview compliance portal](https://compliance.microsoft.com/), navigate to one of the following locations:- + - If you are using records management:- - **Solutions** > **Records management** > > **Label policies** tab > **Auto-apply a label** - + - **Solutions** \> **Records management** \> **Label policies** tab \> **Auto-apply a label** + - If you are using data lifeycle management:- - **Solutions** > **Data lifeycle management** > **Label policies** tab > **Auto-apply a label** - + - **Solutions** \> **Data lifeycle management** \> **Label policies** tab \> **Auto-apply a label** + Don't immediately see your solution in the navigation pane? First select **Show all**. 2. Enter a name and description for this auto-labeling policy, and then select **Next**. When you create an auto-apply policy, you select a retention label to automatica 4. For the **Choose the type of retention policy to create** page, select **Adaptive** or **Static**, depending on the choice you made from the [Before you begin](#before-you-begin) instructions. If you haven't already created adaptive scopes, you can select **Adaptive** but because there won't be any adaptive scopes to select, you won't be able to finish the wizard with this option. 5. Depending on your selected scope:- - - If you chose **Adaptive**: On the **Choose adaptive policy scopes and locations** page, select **Add scopes** and select one or more adaptive scopes that have been created. Then, select one or more locations. The locations that you can select depend on the [scope types](retention-settings.md#configuration-information-for-adaptive-scopes) added. For example, if you only added a scope type of **User**, you will be able to select **Exchange email** but not **SharePoint sites**. - ++ - If you chose **Adaptive**: On the **Choose adaptive policy scopes and locations** page, select **Add scopes** and select one or more adaptive scopes that have been created. Then, select one or more locations. The locations that you can select depend on the [scope types](retention-settings.md#configuration-information-for-adaptive-scopes) added. For example, if you only added a scope type of **User**, you will be able to select **Exchange email** but not **SharePoint sites**. + - If you chose **Static**: On the **Choose locations** page, toggle on or off any of the locations. For each location, you can leave it at the default to [apply the policy to the entire location](retention-settings.md#a-policy-that-applies-to-entire-locations), or [specify includes and excludes](retention-settings.md#a-policy-with-specific-inclusions-or-exclusions)- + For information about the location choices, see [Locations](retention-settings.md#locations). 6. Follow the prompts in the wizard to select a retention label, and then review and submit your configuration choices. Additionally, SharePoint items that are in draft or that have never been publish > [!IMPORTANT] > For emails that you auto-apply by identifying sensitive information, all mailboxes are automatically included, which includes mailboxes from Microsoft 365 groups.-> +> > Although group mailboxes would usually be included by selecting the **Microsoft 365 Groups** location, for this specific policy configuration, the groups location includes only SharePoint sites connected to a Microsoft 365 group. When you create auto-apply retention label policies for sensitive information, you see the same list of policy templates as when you create a Microsoft Purview Data Loss Prevention (DLP) policy. Each template is preconfigured to look for specific types of sensitive information. In the following example, the sensitive info types are from the **Privacy** category, and **U.S Personally Identifiable Information (PII) Data** template: When you create auto-apply retention label policies for sensitive information, y To learn more about the sensitivity information types, see [Learn about sensitive information types](sensitive-information-type-learn-about.md#learn-about-sensitive-information-types). Currently, [exact data match based sensitive information types](sit-learn-about-exact-data-match-based-sits.md#learn-about-exact-data-match-based-sensitive-information-types) and [document fingerprinting](document-fingerprinting.md) are not supported for this scenario. After you select a policy template, you can add or remove any types of sensitive information, and you can change the confidence level and instance count. In the previous example screenshot, these options have been changed so that a retention label will be auto-applied only when:- + - The type of sensitive information that's detected has a match accuracy (or [confidence level](sensitive-information-type-learn-about.md#more-on-confidence-levels)) of at least **Medium confidence** for two of the sensitive info types, and **High confidence** for one. Many sensitive information types are defined with multiple patterns, where a pattern with a higher match accuracy requires more evidence to be found (such as keywords, dates, or addresses), while a pattern with a lower match accuracy requires less evidence. The lower the confidence level, the easier it is for content to match the condition but with the potential for more false positives. - The content contains between 1 and 9 instances of any of these three sensitive info types. The default for the **to** value is **Any**. To consider when using sensitive information types to auto-apply retention label - If you use custom sensitive information types, these can't auto-label existing items in SharePoint and OneDrive. -- For emails, you can't select specific recipients to include or exclude; only the **All recipients** setting is supported and for this configuration only, it includes mailboxes from Microsoft 365 groups. +- For emails, you can't select specific recipients to include or exclude; only the **All recipients** setting is supported and for this configuration only, it includes mailboxes from Microsoft 365 groups. #### Auto-apply labels to content with keywords or searchable properties Some things to consider when using keywords or searchable properties to auto-app - To search for values that contain spaces or special characters, use double quotation marks (`" "`) to contain the phrase; for example, `subject:"Financial Statements"`. -- Use the *DocumentLink* property instead of *Path* to match an item based on its URL. +- Use the *DocumentLink* property instead of *Path* to match an item based on its URL. - Suffix wildcard searches (such as `*cat`) or substring wildcard searches (such as `*cat*`) aren't supported. However, prefix wildcard searches (such as `cat*`) are supported. - Be aware that partially indexed items can be responsible for not labeling items that you're expecting, or labeling items that you're expecting to be excluded from labeling when you use the NOT operator. For more information, see [Partially indexed items in Content Search](partially-indexed-items-in-content-search.md). +- We recommend that you don't use spaces between words in RefinableStrings values on documents. RefinableString is not a word-break property. Examples queries: More complex examples: The following query for SharePoint identifies Word documents or Excel spreadsheets when those files contain the keywords **password**, **passwords**, or **pw**: -``` +```KQL (password OR passwords OR pw) AND (filetype:doc* OR filetype:xls*) ``` The following query for Exchange identifies any Word document or PDF that contains the word **nda** or the phrase **non disclosure agreement** when those documents are attached to an email: -``` +```KQL (nda OR "non disclosure agreement") AND (attachmentnames:.doc* OR attachmentnames:.pdf) ``` -The following query for SharePoint identifies documents that contain a credit card number: +The following query for SharePoint identifies documents that contain a credit card number: -``` +```KQL sensitivetype:"credit card number" ``` The following query contains some typical keywords to help identify documents or emails that contain legal content: -``` +```KQL ACP OR (Attorney Client Privilege*) OR (AC Privilege) ``` -The following query contains typical keywords to help identify documents or emails for human resources: +The following query contains typical keywords to help identify documents or emails for human resources: -``` +```KQL (resume AND staff AND employee AND salary AND recruitment AND candidate) ``` -Note that this final example uses the best practice of always including operators between keywords. A space between keywords (or two property:value expressions) is the same as using AND. By always adding operators, it's easier to see that this example query will identify only content that contains all these keywords, instead of content that contains any of the keywords. If your intention is to identify content that contains any of the keywords, specify OR instead of AND. As this example shows, when you always specify the operators, it's easier to correctly interpret the query. +Note that this final example uses the best practice of always including operators between keywords. A space between keywords (or two property:value expressions) is the same as using AND. By always adding operators, it's easier to see that this example query will identify only content that contains all these keywords, instead of content that contains any of the keywords. If your intention is to identify content that contains any of the keywords, specify OR instead of AND. As this example shows, when you always specify the operators, it's easier to correctly interpret the query. ##### Microsoft Teams meeting recordings Note that this final example uses the best practice of always including operato To identify Microsoft Teams meeting recordings that are stored in users' OneDrive accounts or in SharePoint, specify the following for the **Keyword query editor**: -``` +```KQL ProgID:Media AND ProgID:Meeting ``` Most of the time, meeting recordings are saved to OneDrive. But for channel meet To identify files in SharePoint or OneDrive and Exchange emails that have a specific [sensitivity label](sensitivity-labels.md) applied, specify the following for the **Keyword query editor**: -``` +```KQL InformationProtectionLabelId:<GUID> ``` The cloud attachments supported for this option are files such as documents, vid Although not required for this option, we recommend that you ensure versioning is enabled for your SharePoint sites and OneDrive accounts so that the version shared can be accurately captured. If versioning isn't enabled, the last available version will be retained. Documents in draft or that have never been published aren't supported. -When you select a label to use for auto-applying retention labels for cloud attachments, make sure the label retention setting **Start the retention period based on** is **When items were labeled**. +When you select a label to use for auto-applying retention labels for cloud attachments, make sure the label retention setting **Start the retention period based on** is **When items were labeled**. When you configure the locations for this option, you can select: -- **SharePoint sites** for shared files stored in SharePoint communication sites, team sites that aren't connected by Microsoft 365 groups, and classic sites. +- **SharePoint sites** for shared files stored in SharePoint communication sites, team sites that aren't connected by Microsoft 365 groups, and classic sites. - **Microsoft 365 Groups** for shared files that are stored in team sites connected by Microsoft 365 groups. - **OneDrive accounts** for shared files stored in users' OneDrive. To consider when auto-applying retention labels to cloud attachments: - Cloud attachments shared outside Teams and Outlook aren't supported. - The following items aren't supported as cloud attachments that can be retained:- - SharePoint sites, pages, lists, forms, folders, document sets, and OneNote pages. - - Files shared by users who don't have access to those files. - - Files that are deleted or moved before the cloud attachment is sent. For example, a user copies and pastes a previously shared attachment from another message, without first confirming that the file is still available. Or, somebody forwards an old message when the file is now deleted. - - Files that are shared by guests or users outside your organization. - - Files in draft emails and messages that aren't sent. - - Empty files. + - SharePoint sites, pages, lists, forms, folders, document sets, and OneNote pages. + - Files shared by users who don't have access to those files. + - Files that are deleted or moved before the cloud attachment is sent. For example, a user copies and pastes a previously shared attachment from another message, without first confirming that the file is still available. Or, somebody forwards an old message when the file is now deleted. + - Files that are shared by guests or users outside your organization. + - Files in draft emails and messages that aren't sent. + - Empty files. ## How long it takes for retention labels to take effect When you auto-apply retention labels based on sensitive information, keywords or searchable properties, or trainable classifiers, it can take up to seven days for the retention labels to be applied:- +  If the expected labels don't appear after seven days, check the **Status** of the auto-apply policy by selecting it from the **Label policies** page in the Microsoft Purview compliance portal. If you see the status of **Off (Error)** and in the details for the locations see a message that it's taking longer than expected to deploy the policy (for SharePoint) or to try redeploying the policy (for OneDrive), try running the [Set-RetentionCompliancePolicy](/powershell/module/exchange/set-retentioncompliancepolicy) PowerShell command to retry the policy distribution: If the expected labels don't appear after seven days, check the **Status** of th 1. [Connect to Security & Compliance PowerShell](/powershell/exchange/connect-to-scc-powershell). 2. Run the following command:- + ```PowerShell Set-RetentionCompliancePolicy -Identity <policy name> -RetryDistribution ``` For auto-apply retention label policies that are configured for sensitive inform For auto-apply retention label policies that are configured for cloud attachments: Because this policy applies to newly shared files rather than existing files, a change in configuration to the selected label and policy will be automatically applied to newly shared content only. Some settings can't be changed after the label or policy is created and saved, which include:+ - Names for retention labels and their policies, the scope type (adaptive or static), and the retention settings except the retention period. However, you can't change the retention period when the retention period is based on when items were labeled. - The option to mark items as a record. |
| compliance | Classifier Learn About | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/classifier-learn-about.md | audience: Admin ms.localizationpriority: medium-+ - M365-security-compliance - m365solution-mip - m365initiative-compliance +search.appverid: - MOE150 - MET150 description: "Trainable classifiers can recognize various types of content for labeling or policy application by giving it positive and negative samples to look at." This classification method is well suited to content that isn't easily identifie ### Where you can use classifiers -Classifiers are available to use as a condition for [Office auto-labeling with sensitivity labels](apply-sensitivity-label-automatically.md), [auto-apply retention label policy based on a condition](apply-retention-labels-automatically.md#configuring-conditions-for-auto-apply-retention-labels) and in [communication compliance](communication-compliance.md). +Classifiers are available to use as a condition for [Office auto-labeling with sensitivity labels](apply-sensitivity-label-automatically.md), [auto-apply retention label policy based on a condition](apply-retention-labels-automatically.md#configuring-conditions-for-auto-apply-retention-labels) and in [communication compliance](communication-compliance.md). Sensitivity labels can use classifiers as conditions, see [Apply a sensitivity label to content automatically](apply-sensitivity-label-automatically.md). Sensitivity labels can use classifiers as conditions, see [Apply a sensitivity l Microsoft 365 comes with multiple pre-trained classifiers: -- **Adult, Racy, and Gory**: Detects images of these types. The images must be between 50 kilobytes (KB) and 4 megabytes (MB) in size and be greater than 50 x 50 pixels in height x width dimensions. Scanning and detection are supported for Exchange Online email messages, and Microsoft Teams channels and chats. Detects content in .jpeg, .png, .gif, and .bmp files.+- **Adult, racy, and gory**: Detects images of these types. The images must be between 50 kilobytes (KB) and 4 megabytes (MB) in size and be greater than 50 x 50 pixels in height x width dimensions. Scanning and detection are supported for Exchange Online email messages, and Microsoft Teams channels and chats. Detects content in .jpeg, .png, .gif, and .bmp files. - **Agreements**: Detects content related to legal agreements such as non-disclosure agreements, statements of work, loan and lease agreements, employment and non-compete agreements. Detects content in .docx, .docm, .doc, .dotx, .dotm, .dot, .pdf, .rtf, .txt, .one, .msg, .eml files. -- **Resumes**: detects docx, .pdf, .rtf, .txt items that are textual accounts of an applicant's personal, educational, professional qualifications, work experience, and other personally identifying information--- **Source Code**: detects items that contain a set of instructions and statements written in the top 25 used computer programming languages on GitHub: ActionScript, C, C#, C++, Clojure, CoffeeScript, Go, Haskell, Java, JavaScript, Lua, MATLAB, Objective-C, Perl, PHP, Python, R, Ruby, Scala, Shell, Swift, TeX, Vim Script. Detects content in .msg, .as, .h, .c, .cs, .cc, .cpp, .hpp, .cxx, .hh, .c++, .clj, .edn, .cljc, .cljs, .coffee, .litcoffee, .go, .hs, .lhs, .java, .jar, .js, .mjs, .lua, .m, .mm, .pl, .pm, .t, .xs, .pod, .php, .phar, .php4, .pyc, .R, .r, .rda, .RData, .rds, .rb, .scala, .sc, .sh, .swift files.--- **Customer Complaints**: The customer complaints classifier detects feedback and complaints made about your organization's products or services. This classifier can help you meet regulatory requirements on the detection and triage of complaints, like the Consumer Financial Protection Bureau and Food and Drug Administration requirements. For Communications Compliance, it detects content in .msg, and .eml files. For the rest of Microsoft Purview Information Protection services, it detects content in .docx, .pdf, .txt, .rtf, .jpg, .jpeg, .png, .gif, .bmp, .svg files.+- **Customer complaints**: The customer complaints classifier detects feedback and complaints made about your organization's products or services. This classifier can help you meet regulatory requirements on the detection and triage of complaints, like the Consumer Financial Protection Bureau and Food and Drug Administration requirements. For Communications Compliance, it detects content in .msg, and .eml files. For the rest of Microsoft Purview Information Protection services, it detects content in .docx, .pdf, .txt, .rtf, .jpg, .jpeg, .png, .gif, .bmp, .svg files. - **Discrimination**: Detects explicit discriminatory language and is sensitive to discriminatory language against the African American/Black communities when compared to other communities. Microsoft 365 comes with multiple pre-trained classifiers: - **IT**: Detects content in Information Technology and Cybersecurity categories such as network settings, information security, hardware, and software. Detects content in .docx, .docm, .doc, .dotx, .dotm, .dot, .pdf, .rtf, .txt, .one, .msg, .eml, .pptx, .pptm, .ppt, .potx, .potm, .pot, .ppsx, .ppsm, .pps, .ppam, .ppa, .xlsx, .xlsm, .xlsb, .xls, .csv, .xltx, .xltm, .xlt, .xlam, .xla files. -- **Legal Affairs**: Detects content in legal affairs-related categories such as litigation, legal process, legal obligation, legal terminology, law, and legislation. Detects content in .docx, .docm, .doc, .dotx, .dotm, .dot, .pdf, .rtf, .txt, .one, .msg, .eml files.+- **Legal affairs**: Detects content in legal affairs-related categories such as litigation, legal process, legal obligation, legal terminology, law, and legislation. Detects content in .docx, .docm, .doc, .dotx, .dotm, .dot, .pdf, .rtf, .txt, .one, .msg, .eml files. - **Procurement**: Detects content in categories of bidding, quoting, purchasing, and paying for supply of goods and services. Detects content in .docx, .docm, .doc, .dotx, .dotm, .dot, .pdf, .rtf, .txt, .one, .msg, .eml, .xlsx, .xlsm, .xlsb, .xls, .csv, .xltx, .xltm, .xlt, .xlam, .xla files. -- **Profanity**: Detects a specific category of offensive language text items that contain expressions that embarrass most people.+- **Profanity**: Detects a specific category of offensive language text items that contain expressions that embarrass most people. Detects content in .msg, .docx, .pdf, .txt, .rtf, .jpeg, .jpg, .png, .gif, .bmp, .svg files. -- **Resumes**: detects docx, .pdf, .rtf, .txt items that are textual accounts of an applicant's personal, educational, professional qualifications, work experience, and other personally identifying information+- **Resume**: detects docx, .pdf, .rtf, .txt items that are textual accounts of an applicant's personal, educational, professional qualifications, work experience, and other personally identifying information -- **Source Code**: detects items that contain a set of instructions and statements written in the top 25 used computer programming languages on GitHub: ActionScript, C, C#, C++, Clojure, CoffeeScript, Go, Haskell, Java, JavaScript, Lua, MATLAB, Objective-C, Perl, PHP, Python, R, Ruby, Scala, Shell, Swift, TeX, Vim Script.+- **Source code**: detects items that contain a set of instructions and statements written computer programming languages on GitHub: ActionScript, C, C#, C++, Clojure, CoffeeScript, Go, Haskell, Java, JavaScript, Lua, MATLAB, Objective-C, Perl, PHP, Python, R, Ruby, Scala, Shell, Swift, TeX, Vim Script. Detects content in .msg, .as, .h, .c, .cs, .cc, .cpp, .hpp, .cxx, .hh, .c++, .clj, .edn, .cljc, .cljs, .coffee, .litcoffee, .go, .hs, .lhs, .java, .jar, .js, .mjs, .lua, .m, .mm, .pl, .pm, .t, .xs, .pod, .php, .phar, .php4, .pyc, .R, .r, .rda, .RData, .rds, .rb, .scala, .sc, .sh, .swift files. - > [!NOTE] - > Source Code is trained to detect when the bulk of the text is source code. It does not detect source code text that is interspersed with plain text. + > [!NOTE] + > Source Code is trained to detect when the bulk of the text is source code. It does not detect source code text that is interspersed with plain text. - **Tax**: Detects Tax relation content such as tax planning, tax forms, tax filing, tax regulations. Detects content in .docx, .docm, .doc, .dotx, .dotm, .dot, .pdf, .rtf, .txt, .one, .msg, .eml, .pptx, .pptm, .ppt, .potx, .potm, .pot, .ppsx, .ppsm, .pps, .ppam, .ppa, .xlsx, .xlsm, .xlsb, .xls, .csv, .xltx, .xltm, .xlt, .xlam, xla files. - **Threat**: Detects a specific category of offensive language text items related to threats to commit violence or do physical harm or damage to a person or property.-- **Profanity**: Detects a specific category of offensive language text items that contain expressions that embarrass most people. Detects content in .msg, .docx, .pdf, .txt, .rtf, .jpeg, .jpg, .png, .gif, .bmp, .svg files.-- **Tax**: Detects Tax relation content such as tax planning, tax forms, tax filing, tax regulations. Detects content in .docx, .docm, .doc, .dotx, .dotm, .dot, .pdf, .rtf, .txt, .one, .msg, .eml, .pptx, .pptm, .ppt, .potx, .potm, .pot, .ppsx, .ppsm, .pps, .ppam, .ppa, .xlsx, .xlsm, .xlsb, .xls, .csv, .xltx, .xltm, .xlt, .xlam, xla files.+ - **Threat**: Detects a specific category of offensive language text items related to threats to commit violence or do physical harm or damage to a person or property. Detects content in .msg, .docx, .pdf, .txt, .rtf, .jpeg, .jpg, .png, .gif, .bmp, .svg files. -These appear in the **Microsoft Purview compliance portal** > **Data classification** > **Trainable classifiers** view with the status of `Ready to use`. +These classifiers appear in the **Microsoft Purview compliance portal** \> **Data classification** \> **Trainable classifiers** view with the status of `Ready to use`.  All others are English only at the moment. When the pre-trained classifiers don't meet your needs, you can create and train your own classifiers. There's more work involved with creating your own, but they'll be much better tailored to your organizations needs. -You start creating a custom trainable classifier by feeding it examples that are definitely in the category. Once it processes those examples, you test it by giving it a mix of both matching and non-matching examples. The classifier then makes predictions as to whether any given item falls into the category you're building. You then confirm its results, sorting out the true positives, true negatives, false positives, and false negatives to help increase the accuracy of its predictions. +You start creating a custom trainable classifier by feeding it examples that are definitely in the category. Once it processes those examples, you test it by giving it a mix of both matching and non-matching examples. The classifier then makes predictions as to whether any given item falls into the category you're building. You then confirm its results, sorting out the true positives, true negatives, false positives, and false negatives to help increase the accuracy of its predictions. When you publish the classifier, it sorts through items in locations like SharePoint Online, Exchange, and OneDrive, and classifies the content. After you publish the classifier, you can continue to train it using a feedback process that is similar to the initial training process. |
| compliance | Compliance Manager Assessments | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/compliance-manager-assessments.md | You can create a group while creating a new assessment. Groups can't be created ## Understand templates before creating assessments -Assessment templates contain the controls and action recommendations for assessments, based on certifications for different privacy regulations and standards. Your organization's available templates may include one or more templates that were included as part of your licensing agreement, along with any additional premium templates that you have purchased. +Assessment templates contain the controls and action recommendations for assessments, based on certifications for different privacy regulations and standards. Your organization starts out with at least one and possibly more **included** templates available to use, depending on your licensing agreement. Your organization may also purchase additional **premium** templates. -Each template, whether included or premium, exists in two versions: one for use with Microsoft 365 (or other Microsoft products as available), and a universal version that can be tailored to assess other products that you use. You can choose the appropriate template type for the product you want to assess. +Each template exists in two versions: one for use with Microsoft 365 (or other Microsoft products as available), and a universal version that can be tailored to assess other products that you use. You can choose the appropriate template type for the product you want to assess. -To learn more about templates, see [Working with assessment templates](compliance-manager-templates.md). +Get more details more about templates at [Learn about assessment templates in Compliance Manager](compliance-manager-templates.md). ## Create assessments |
| compliance | Compliance Manager Templates | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/compliance-manager-templates.md | Title: "Working with assessment templates in Microsoft Purview Compliance Manager" + Title: "Learn about assessment templates in Microsoft Purview Compliance Manager" f1.keywords: - NOCSH description: "Understand how to use and manage templates for building assessment ## Templates overview -A template is a framework of controls for creating an assessment in Compliance Manager. Our comprehensive set of templates can help your organization comply with national, regional, and industry-specific requirements governing the collection and use of data. +A template is a framework of controls for creating an assessment in Compliance Manager. Our comprehensive set of templates can help your organization comply with national, regional, and industry-specific requirements governing the collection and use of data. We refer to templates by the same name as their underlying certification or regulation, such as the EU GDPR template and the ISO/IEC 27701:2019 template. ## Template versions: Microsoft and universal -We refer to templates by the same name as their underlying certification or regulation, such as the EU GDPR template and the ISO/IEC 27701:2019 template. +Compliance Manger can be used to assess different types of products. All templates, except the [Microsoft Data Protection Baseline](compliance-manager-assessments.md#data-protection-baseline-default-assessment) default template, come in two versions: -Compliance Manger can be used to assess different types of products. All templates apart from the baseline come in at least one version that applies to a pre-defined product, such as Microsoft 365, and a universal version that can be tailored to suit other products. Assessments from universal templates are more generalized but offer expanded versatility, since they can help you easily track your organization's compliance across multiple products. +1. A version that applies to a pre-defined product, such as Microsoft 365, and +2. A universal version that can be tailored to suit other products. ++Assessments from universal templates are more generalized but offer expanded versatility, since they can help you easily track your organization's compliance across multiple products. Note that US Government Community (GCC) Moderate, GCC High, and Department of Defense (DoD) customers cannot currently use universal templates. |
| compliance | Get Started Core Ediscovery | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/get-started-core-ediscovery.md | Licensing for eDiscovery (Standard) requires the appropriate organization subscr - **Per-user licensing:** To place an eDiscovery hold on mailboxes and sites, users must be assigned one of the following licenses, depending on your organization subscription: + - Exchange online Plan 2 license ++ OR + - A Microsoft 365 E3 or Office 365 E3 license or higher OR |
| compliance | Purview Compliance | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/purview-compliance.md | Unintentional sharing of sensitive items can cause financial harm to your organi For more information, see [Learn about data lifecycle management](/microsoft-365/compliance/data-lifecycle-management). +### Encrypt your data and control your encryption keys ++[Encryption](/microsoft-365/compliance/encryption) is an important part of your file protection and information protection strategy. The encryption process encodes your data (referred to as plaintext) into ciphertext. Unlike plaintext, ciphertext can't be used by people or computers unless and until the ciphertext is decrypted. Decryption requires an encryption key that only authorized users have. Encryption helps ensure that only authorized recipients can decrypt your content. ++[Microsoft Purview Double Key Encryption](/microsoft-365/compliance/double-key-encryption) helps secure your most sensitive data that is subject to the strictest protection requirements. [Microsoft Purview Customer Key](/microsoft-365/compliance/customer-key-overview) helps you meet regulatory or compliance obligations for controlling root keys. You explicitly authorize Microsoft 365 services to use your encryption keys to provide value added cloud services, such as eDiscovery, anti-malware, anti-spam, search indexing, and so on. + ## Identify data risks and manage regulatory compliance requirements Insider risks are one of the top concerns of security and compliance professionals in the modern workplace. Industry studies have shown that insider risks are often associated with specific user events or activities. Protecting your organization against these risks can be challenging to identify and difficult to mitigate. Insider risks include vulnerabilities in various areas and can cause major problems for your organization, ranging from the loss of intellectual property to workplace harassment, and more. |
| compliance | Recover An Inactive Mailbox | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/recover-an-inactive-mailbox.md | After you recover an inactive mailbox, a new user account is also created. You n Get-Mailbox -InactiveMailboxOnly <identity of inactive mailbox> | Format-List ExternalDirectoryObjectId ``` - - If there's a value for the **ExternalDirectoryObjectId** property, the mailbox retention period has expired, and you can recover the inactive mailbox by running the **New-Mailbox -InactiveMailbox** command. + - If there's no value for the **ExternalDirectoryObjectId** property, the mailbox retention period has expired, and you can recover the inactive mailbox by running the **New-Mailbox -InactiveMailbox** command. - If there's a value for the **ExternalDirectoryObjectId** property, the soft-deleted mailbox retention period hasn't expired and you have to recover the mailbox by [restoring the user account](../admin/add-users/delete-a-user.md). - **Consider enabling the archive mailbox after you recover an inactive mailbox.** This lets the returning user or new employee move old messages to the archive mailbox. And when the retention hold expires, the archive policy that is part of the default Exchange MRM retention policy assigned to Exchange Online mailboxes will move items that are two years or older to the archive mailbox. If you don't enable the archive mailbox, items older than two years will remain in the user's primary mailbox. For more information, see [Enable archive mailboxes](enable-archive-mailboxes.md). |
| enterprise | Additional Office365 Ip Addresses And Urls | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/enterprise/additional-office365-ip-addresses-and-urls.md | Title: Other endpoints not included in the Office 365 IP Address and URL Web ser Previously updated : 05/19/2022 Last updated : 06/15/2022 audience: Admin Apart from DNS, these instances are all optional for most customers unless you n |22|Use **MFA server** for multi-factor authentication requests, both new installations of the server and setting it up with Active Directory Domain Services (AD DS).|See [Getting started with the Azure AD multi-factor authentication Server](/azure/active-directory/authentication/howto-mfaserver-deploy#plan-your-deployment).|Outbound server-only traffic| |23|**Microsoft Graph Change Notifications** <p> Developers can use [change notifications](/graph/webhooks?context=graph%2fapi%2f1.0&view=graph-rest-1.0&preserve-view=true) to subscribe to events in the Microsoft Graph.|Public Cloud: 52.159.23.209, 52.159.17.84, 52.147.213.251, 52.147.213.181, 13.85.192.59, 13.85.192.123, 13.89.108.233, 13.89.104.147, 20.96.21.67, 20.69.245.215, 137.135.11.161, 137.135.11.116, 52.159.107.50, 52.159.107.4, 52.229.38.131, 52.183.67.212, 52.142.114.29, 52.142.115.31, 51.124.75.43, 51.124.73.177, 20.44.210.83, 20.44.210.146, 40.80.232.177, 40.80.232.118, 20.48.12.75, 20.48.11.201, 104.215.13.23, 104.215.6.169, 52.148.24.136, 52.148.27.39, 40.76.162.99, 40.76.162.42, 40.74.203.28, 40.74.203.27, 13.86.37.15, 52.154.246.238, 20.96.21.98, 20.96.21.115, 137.135.11.222, 137.135.11.250, 52.159.109.205, 52.159.102.72, 52.151.30.78, 52.191.173.85, 51.104.159.213, 51.104.159.181, 51.138.90.7, 51.138.90.52, 52.148.115.48, 52.148.114.238, 40.80.233.14, 40.80.239.196, 20.48.14.35, 20.48.15.147, 104.215.18.55, 104.215.12.254, 20.199.102.157, 20.199.102.73, 13.87.81.123, 13.87.81.35, 20.111.9.46, 20.111.9.77, 13.87.81.133, 13.87.81.141 <p> Microsoft Cloud for US Government: 52.244.33.45, 52.244.35.174, 52.243.157.104, 52.243.157.105, 52.182.25.254, 52.182.25.110, 52.181.25.67, 52.181.25.66, 52.244.111.156, 52.244.111.170, 52.243.147.249, 52.243.148.19, 52.182.32.51, 52.182.32.143, 52.181.24.199, 52.181.24.220 <p> Microsoft Cloud China operated by 21Vianet: 42.159.72.35, 42.159.72.47, 42.159.180.55, 42.159.180.56, 40.125.138.23, 40.125.136.69, 40.72.155.199, 40.72.155.216 <br> TCP port 443 <p> Note: Developers can specify different ports when creating the subscriptions.|Inbound server traffic| |24|**Network Connection Status Indicator**<p>Used by Windows 10 and 11 to determine if the computer is connected to the internet (does not apply to non-Windows clients). When this URL cannot be reached, Windows will assume it is not connected to the Internet and M365 Apps for Enterprise will not try to verify activation status, causing connections to Exchange and other services to fail.|www.msftconnecttest.com <br> 13.107.4.52<p>Also see [Manage connection endpoints for Windows 11 Enterprise](/windows/privacy/manage-windows-11-endpoints) and [Manage connection endpoints for Windows 10 Enterprise, version 21H2](/windows/privacy/manage-windows-21h2-endpoints).|Outbound server-only traffic|-| +|25|**Teams Notifications on Mobile Devices**<p>Used by Android and Apple mobile devices to receive push notifications to the Teams client for incoming calls and other Teams services. When these ports are blocked, all push notifications to mobile devices will fail.|For specific ports, see [FCM ports and your firewall in the Google Firebase documentation](https://firebase.google.com/docs/cloud-messaging/concept-options#messaging-ports-and-your-firewall) and [If your Apple devices aren't getting Apple push notifications](https://support.apple.com/en-us/HT203609).|Outbound server-only traffic| ## Related Topics |
| enterprise | Modern Desktop Deployment And Management Lab | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/enterprise/modern-desktop-deployment-and-management-lab.md | There are two versions of the lab available for free download: |Windows 10 Lab|Windows 11 Lab| |||-|[Win 10 lab environment](https://download.microsoft.com/download/3/3/a/33a3c7d7-b393-4f78-9b90-2d5eb7fd98e8/Win10_21H1_lab.zip)|[Win 11 lab environment](https://download.microsoft.com/download/9/d/9/9d9e278e-a1ea-4704-85e1-cb24f3806f45/Win11_Lab_05.09.zip)| -|[Win 10 lab guides](https://download.microsoft.com/download/2/9/9/29952cdb-b98d-4f9b-9d6e-9fb49644b0a0/Win10_21H1_Lab_05.12.zip)|[Win 11 lab guides](https://download.microsoft.com/download/9/d/9/9d9e278e-a1ea-4704-85e1-cb24f3806f45/Win11_Lab_Guides_05.09.zip)| +|[Win 10 lab environment](https://download.microsoft.com/download/8/5/e/85e007b0-1f3e-460c-bd0a-5a8c6ec490b5/Win10_21H2_lab.zip)|[Win 11 lab environment](https://download.microsoft.com/download/9/d/9/9d9e278e-a1ea-4704-85e1-cb24f3806f45/Win11_Lab_05.09.zip)| +|[Win 10 lab guides](https://download.microsoft.com/download/8/5/e/85e007b0-1f3e-460c-bd0a-5a8c6ec490b5/Win10_21H2_guides.zip)|[Win 11 lab guides](https://download.microsoft.com/download/9/d/9/9d9e278e-a1ea-4704-85e1-cb24f3806f45/Win11_Lab_Guides_05.09.zip)| ## A complete lab environment The lab provides you with an automatically provisioned virtual lab environment, |Windows 10 Lab|Windows 11 Lab| |||-|Windows 10 Enterprise, Version 21H1|Windows 11 Enterprise| +|Windows 10 Enterprise, Version 21H2|Windows 11 Enterprise| |Microsoft Endpoint Configuration Manager, Version 2203|Microsoft Endpoint Configuration Manager, Version 2203| |Windows Assessment and Deployment Kit for Windows 10|Windows Assessment and Deployment Kit for Windows 11| |Windows Server 2019|Windows Server 2022| Detailed lab guides take you through multiple deployment and management scenario > [!NOTE]-> Please use a broadband internet connection to download this content and allow approximately 30 minutes for automatic provisioning. The lab environment requires a minimum of 16 GB of available memory and 150 GB of free disk space. For optimal performance, 32 GB of available memory and 300 GB of free space is recommended. The evaluation software in these labs expires 90-120 days after activation. New versions of the labs will be published in August, 2022. +> Please use a broadband internet connection to download this content and allow approximately 30 minutes for automatic provisioning. The lab environment requires a minimum of 16 GB of available memory and 150 GB of free disk space. For optimal performance, 32 GB of available memory and 300 GB of free space is recommended. The virtual clients expire 90 days after activation of the lab. The virtual servers expire on September 11, 2022. New versions of the labs will be published prior to expiration. ## Additional guidance |
| enterprise | Office 365 Network Mac Perf Overview | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/enterprise/office-365-network-mac-perf-overview.md | Title: "Network connectivity in the Microsoft 365 Admin Center" Previously updated : 12/06/2021 Last updated : 06/15/2022 audience: Admin ms.localizationpriority: medium+ search.appverid: - MET150 To get started, turn on your location opt-in setting to automatically collect da ### 1. Enable Windows Location Services -For this option, you must have at least two computers running at each office location that support the pre-requisites. OneDrive for Windows version must be up-to-date and installed on each computer. For more information on OneDrive versions, see the [OneDrive release notes](https://support.office.com/article/onedrive-release-notes-845dcf18-f921-435e-bf28-4e24b95e5fc0). Network measurements are planned to be added to other Office 365 client applications soon. +For this option, you must have at least two computers running at each office location that support the pre-requisites. OneDrive for Windows version must be up-to-date and installed on each computer. Network tests are only run no more than once a day at a random time. Network measurements are planned to be added to other Office 365 client applications soon. Windows Location Service must be consented on the machines. You can test this by running the **Maps** app and locating yourself. It can be enabled on a single machine with **Settings | Privacy | Location** where the setting _Allow apps to access your location_ must be enabled. Windows Location Services consent can be deployed to PCs using MDM or Group Policy with the setting _LetAppsAccessLocation_. -You don't need to add locations in the Admin Center with this method as they're automatically identified at the city resolution. Multiple office locations within the same city won't be shown when using Windows Location Services. Location information is rounded to the nearest 300 meters by 300 meters so that more precise location information isn't accessed. +You don't need to add locations in the Admin Center with this method as they're automatically identified at the city resolution. Multiple office locations within the same city won't be shown when using Windows Location Services. Location information is rounded to the nearest 300 meters by 300 meters so that more precise location information isn't accessed. Use of Windows Location Services for network measurements is off by default for customers. You must enable it in the Network Connectivity Settings Location flyout. ++ > [!div class="mx-imgBorder"] + >  The machines should have Wi-Fi networking rather than an ethernet cable. Machines with an ethernet cable don't have accurate location information. -Measurement samples and office locations should start to appear 24 hours after these pre-requisites have been met. +Measurement samples and office locations should start to appear 24 hours after these pre-requisites have been met. Office locations discovered from Windows Location Services are aggregated per City and are retained in your view for 90 days after samples are no longer received. If you choose to switch to office locations added by the Administrator with LAN subnet information you can disable Windows Location Services and hide all of the discovered locations. They will be removed after the 90 day period. ### 2. Add locations and provide LAN subnet information -For this option, neither Windows Location Services nor Wi-Fi is required. Your OneDrive for Windows version must be up-to-date and installed on at least one computer at the location. +For this option, neither Windows Location Services nor Wi-Fi is required. Your OneDrive for Windows version must be up-to-date and installed on at least one computer at the location and you must know your LAN subnet information for each of your offices. This option allows multiple office locations per city and you can name your office locations. You can also upload them from other sources. Make sure that you also add locations in the **locations page** or import those from a CSV file. The locations added must include your office LAN subnet information. In the dialog for adding or editing a location, you can specify a number of LAN subnets and a number of public egress IP subnets. The LAN subnets are required and one of them must match the LAN subnet attribute on a received network assessment for results to show up. Super nets aren't supported so the LAN subnet must match exactly. All test measurements from client machines include the LAN subnet information, w For this option, you need to identify a person at each location. Ask them to browse to [Microsoft 365 network connectivity test](https://connectivity.office.com) on a Windows machine on which they have administrative permissions. On the web site, they need to sign in to their Office 365 account for the same organization that you want to see the results. Then they should click **Run test**. During the test there's a downloaded Connectivity test EXE. They need to open and execute that. Once the tests are completed, the test result is uploaded to the Admin Center. -Test reports are linked to a location if it was added with LAN subnet information, otherwise they are shown at the city location only. +Test reports are linked to a location if it was added with LAN subnet information, otherwise they are shown at the discovered City location only. Measurement samples and office locations should start to appear 2-3 minutes after a test report is completed. For more information, see [Microsoft 365 network connectivity test](office-365-network-mac-perf-onboarding-tool.md). |
| enterprise | Upgrade From Sharepoint 2010 | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/enterprise/upgrade-from-sharepoint-2010.md | You may decide to move some of your sites to the "evergreen" hardware of SharePo - *Hardware/software requirements for:* - [SharePoint Server 2010](/previous-versions/office/sharepoint-server-2010/cc262485(v=office.14)) | [SharePoint Server 2013](/SharePoint/install/hardware-and-software-requirements-0) | [SharePoint Server 2016](/SharePoint/install/hardware-and-software-requirements) + [SharePoint Server 2010](/previous-versions/office/sharepoint-server-2010/cc262485(v=office.14)) | [SharePoint Server 2013](/sharepoint/install/hardware-software-requirements-2013) | [SharePoint Server 2016](/SharePoint/install/hardware-and-software-requirements) - *Software boundaries and limits for:* - [SharePoint Server 2010](/previous-versions/office/sharepoint-server-2010/cc262787(v=office.14)) | [SharePoint Server 2013](/SharePoint/install/software-boundaries-and-limits) | [SharePoint Server 2016](/SharePoint/install/software-boundaries-and-limits-0) + [SharePoint Server 2010](/previous-versions/office/sharepoint-server-2010/cc262787(v=office.14)) | [SharePoint Server 2013](/SharePoint/install/software-boundaries-and-limits) | [SharePoint Server 2016](/sharepoint/install/software-boundaries-limits-2019) - *The upgrade process overview for:* Begin by knowing that you meet hardware and software requirements, then follow s - *Hardware/software requirements for*: - [SharePoint Server 2010](/previous-versions/office/sharepoint-server-2010/cc262485(v=office.14)) | [SharePoint Server 2010](/previous-versions/office/sharepoint-server-2010/cc262485(v=office.14)) | [SharePoint Server 2013](/SharePoint/install/hardware-and-software-requirements-0) | [SharePoint Server 2016](/SharePoint/install/hardware-and-software-requirements) + [SharePoint Server 2010](/previous-versions/office/sharepoint-server-2010/cc262485(v=office.14)) | [SharePoint Server 2010](/previous-versions/office/sharepoint-server-2010/cc262485(v=office.14)) | [SharePoint Server 2013](/sharepoint/install/hardware-software-requirements-2013) | [SharePoint Server 2016](/SharePoint/install/hardware-and-software-requirements) - *Software boundaries and limits for*: - [SharePoint Server 2007](/previous-versions/office/sharepoint-2007-products-and-technologies/cc262787(v=office.12)) | [SharePoint Server 2010](/previous-versions/office/sharepoint-server-2010/cc262787(v=office.14)) | [SharePoint Server 2013](/SharePoint/install/software-boundaries-and-limits) | [SharePoint Server 2016](/SharePoint/install/software-boundaries-and-limits-0) + [SharePoint Server 2007](/previous-versions/office/sharepoint-2007-products-and-technologies/cc262787(v=office.12)) | [SharePoint Server 2010](/previous-versions/office/sharepoint-server-2010/cc262787(v=office.14)) | [SharePoint Server 2013](/SharePoint/install/software-boundaries-and-limits) | [SharePoint Server 2016](/sharepoint/install/software-boundaries-limits-2019) - *The upgrade process overview for*: |
| includes | Security Config Mgt Prerequisites | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/includes/security-config-mgt-prerequisites.md | When a device that is domain joined creates a trust with Azure Active Directory, - Azure Active Directory Connect (AAD Connect) must be synchronized to the tenant that is used from Microsoft Defender for Endpoint - Hybrid Azure Active Directory Join must be configured in your environment (either through Federation or AAD Connect Sync) - AAD Connect Sync must include the device objects *in scope* for synchronization with Azure Active Directory (when needed for join)-- AAD Connect rules for sync must be modified for Server 2012 R2 (when support for Server 2012 R2 is needed)+- AAD Connect rules for sync [must be modified for Server 2012 R2](/microsoft-365/security/defender-endpoint/troubleshoot-security-config-mgt?view=o365-worldwide#instructions-for-applying-computer-join-rule-in-aad-connect) (when support for Server 2012 R2 is needed) - All devices must register in the Azure Active Directory of the tenant that hosts Microsoft Defender for Endpoint. Cross-tenant scenarios are not supported. ### Connectivity Requirements |
| security | Configure Microsoft Defender Antivirus Features | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/configure-microsoft-defender-antivirus-features.md | The following broad categories of features can be configured: > [!TIP] > Review [Reference topics for management and configuration tools](configuration-management-reference-microsoft-defender-antivirus.md).--> [!TIP] > If you're looking for Antivirus related information for other platforms, see: > - [Set preferences for Microsoft Defender for Endpoint on macOS](mac-preferences.md) > - [Microsoft Defender for Endpoint on Mac](microsoft-defender-endpoint-mac.md) The following broad categories of features can be configured: > - [Set preferences for Microsoft Defender for Endpoint on Linux](linux-preferences.md) > - [Microsoft Defender for Endpoint on Linux](microsoft-defender-endpoint-linux.md) > - [Configure Defender for Endpoint on Android features](android-configure.md)-> - [Configure Microsoft Defender for Endpoint on iOS features](ios-configure-features.md) +> - [Configure Microsoft Defender for Endpoint on iOS features](ios-configure-features.md) |
| security | Defender Endpoint Plan 1 2 | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/defender-endpoint-plan-1-2.md | Last updated 05/16/2022 ms.prod: m365-security ms.technology: mdep1 ms.localizationpriority: medium-+ f1.keywords: NOCSH - M365-security-compliance Microsoft Defender for Endpoint is an enterprise endpoint security platform desi - [Microsoft Defender Vulnerability Management](../defender-vulnerability-management/index.yml) - [Microsoft 365 Defender](https://go.microsoft.com/fwlink/?linkid=2118804) -You can use this article to help clarify what protection is provided by the different features available in Defender for Endpoint Plan 1, Defender for Endpoint Plan 2 and the Defender Vulnerability Management add-on. +You can use this article to help clarify what protection is provided by the different features available in Defender for Endpoint Plan 1, Defender for Endpoint Plan 2, and the new Defender Vulnerability Management add-on. -| [Defender for Endpoint Plan 1](defender-endpoint-plan-1.md) | [Defender for Endpoint Plan 2](microsoft-defender-endpoint.md) | [Defender Vulnerability Management add-on](../defender-vulnerability-management/defender-vulnerability-management-capabilities.md)| -|:|:|:| -| [Next-generation protection](defender-endpoint-plan-1.md#next-generation-protection) <br/>(includes antimalware and antivirus) <p> [Attack surface reduction](defender-endpoint-plan-1.md#attack-surface-reduction) <p> [Manual response actions](defender-endpoint-plan-1.md#manual-response-actions) <p> [Centralized management](defender-endpoint-plan-1.md#centralized-management) <p>[Security reports](defender-endpoint-plan-1.md#reporting) <p>[APIs](defender-endpoint-plan-1.md#apis) | Defender for Endpoint Plan 1 capabilities, plus: <p> <p> [Device discovery](device-discovery.md) <p> [Device inventory](machines-view-overview.md) <p> [Core Defender Vulnerability Management capabilities](../defender-vulnerability-management/defender-vulnerability-management-capabilities.md) <p> [Threat Analytics](threat-analytics.md) <p> [Automated investigation and response](automated-investigations.md) <p> [Advanced hunting](advanced-hunting-overview.md) <p> [Endpoint detection and response](overview-endpoint-detection-response.md) <p> [Microsoft Threat Experts](microsoft-threat-experts.md) | Additional Defender Vulnerability Management for Defender for Endpoint Plan 2: <p> [Security baselines assessment](../defender-vulnerability-management/tvm-security-baselines.md) <p> [Block vulnerable applications](../defender-vulnerability-management/tvm-block-vuln-apps.md) <p> [Browser extensions](../defender-vulnerability-management/tvm-browser-extensions.md) <p> [Digital certificate assessment](../defender-vulnerability-management/tvm-certificate-inventory.md) <p> [Network share analysis](../defender-vulnerability-management/tvm-network-share-assessment.md)| -| [Support for Windows 10, iOS, Android OS, and macOS devices](defender-endpoint-plan-1.md#cross-platform-support) | Support for Windows (client and server) and non-Windows platforms<br/> (macOS, iOS, Android, and Linux) | Support for Windows (client and server) and non-Windows platforms<br/> (macOS, iOS, Android, and Linux) | -| To try Defender for Endpoint Plan 1, visit [https://aka.ms/mdep1trial](https://aka.ms/mdep1trial) | To try Defender for Endpoint Plan 2, visit [https://aka.ms/MDEp2OpenTrial](https://aka.ms/MDEp2OpenTrial) | To try Microsoft Defender Vulnerability Management add-on, visit [https://aka.ms/AddonPreviewTrial](https://aka.ms/AddonPreviewTrial). For more information, see [Get Defender Vulnerability Management](../defender-vulnerability-management/get-defender-vulnerability-management.md). +## Compare Defender for Endpoint plans -## Next steps +| Subscription | What's included | +|:|:| +| [Defender for Endpoint Plan 1](defender-endpoint-plan-1.md) | [Next-generation protection](defender-endpoint-plan-1.md#next-generation-protection) <br/>(includes antimalware and antivirus) <p> [Attack surface reduction](defender-endpoint-plan-1.md#attack-surface-reduction) <p> [Manual response actions](defender-endpoint-plan-1.md#manual-response-actions) <p> [Centralized management](defender-endpoint-plan-1.md#centralized-management) <p>[Security reports](defender-endpoint-plan-1.md#reporting) <p>[APIs](defender-endpoint-plan-1.md#apis) <p> [Support for Windows 10, iOS, Android OS, and macOS devices](defender-endpoint-plan-1.md#cross-platform-support)| +| [Defender for Endpoint Plan 2](microsoft-defender-endpoint.md) | Defender for Endpoint Plan 1 capabilities, plus: <p> <p> [Device discovery](device-discovery.md) <p> [Device inventory](machines-view-overview.md) <p> [Core Defender Vulnerability Management capabilities](../defender-vulnerability-management/defender-vulnerability-management-capabilities.md) <p> [Threat Analytics](threat-analytics.md) <p> [Automated investigation and response](automated-investigations.md) <p> [Advanced hunting](advanced-hunting-overview.md) <p> [Endpoint detection and response](overview-endpoint-detection-response.md) <p> [Microsoft Threat Experts](microsoft-threat-experts.md) <p>Support for [Windows](configure-endpoints.md) (client and server) and [non-Windows platforms](configure-endpoints-non-windows.md)<br/> (macOS, iOS, Android, and Linux) | +| [Defender Vulnerability Management add-on](../defender-vulnerability-management/defender-vulnerability-management-capabilities.md) | Additional Defender Vulnerability Management for Defender for Endpoint Plan 2: <p><p> [Security baselines assessment](../defender-vulnerability-management/tvm-security-baselines.md) <p> [Block vulnerable applications](../defender-vulnerability-management/tvm-block-vuln-apps.md) <p> [Browser extensions](../defender-vulnerability-management/tvm-browser-extensions.md) <p> [Digital certificate assessment](../defender-vulnerability-management/tvm-certificate-inventory.md) <p> [Network share analysis](../defender-vulnerability-management/tvm-network-share-assessment.md) <p> Support for [Windows](configure-endpoints.md) (client and server) and [non-Windows platforms](configure-endpoints-non-windows.md)<br/> (macOS, iOS, Android, and Linux) | -- [Get an overview of Microsoft Defender for Endpoint Plan 1](defender-endpoint-plan-1.md)-- [Set up and configure Defender for Endpoint Plan 1](mde-p1-setup-configuration.md)-- [Get started using Defender for Endpoint Plan 1](mde-plan1-getting-started.md)+## Start a trial ++- To try Defender for Endpoint Plan 1, visit [https://aka.ms/mdep1trial](https://aka.ms/mdep1trial). +- To try Defender for Endpoint Plan 2, visit [https://aka.ms/MDEp2OpenTrial](https://aka.ms/MDEp2OpenTrial). +- To try the Microsoft Defender Vulnerability Management add-on, visit [https://aka.ms/AddonPreviewTrial](https://aka.ms/AddonPreviewTrial). ## See also -- [Microsoft Defender for Business](../defender-business/mdb-overview.md) (for small and medium-sized businesses)+- [Microsoft Defender for Business](../defender-business/mdb-overview.md) (endpoint protection for small and medium-sized businesses) |
| security | Device Control Report | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/device-control-report.md | -Microsoft Defender for Endpoint device control protects against data loss, by monitoring and controlling media use by devices in your organization, such as the use of removable storage devices and USB drives. +Microsoft Defender for Endpoint device control protects against data loss by monitoring and controlling media use by devices in your organization, such as using removable storage devices and USB drives. -With the device control report, you can view events that relate to media usage, such as: +With the device control report, you can view events that relate to media usage. Such events include: - **Audit events:** Shows the number of audit events that occur when external media is connected. - **Policy events:** Shows the number of policy events that occur when a device control policy is triggered. The audit events include: ## Monitor device control security -Device control in Microsoft Defender for Endpoint empowers security administrators with tools that enable them to track their organization's device control security through reports. You can find the device control report in the Microsoft 365 Defender portal by going to **Reports > Device protection**. +Device control in Defender for Endpoint empowers security administrators with tools that enable them to track their organization's device control security through reports. You can find the device control report in the Microsoft 365 Defender portal ([https://security.microsoft.com](https://security.microsoft.com)). Go to **Reports** > **General** > **Security report**. Find **Device control** card, and select the link to open the report. The Device protection card on the **Reports** dashboard shows the number of audit events generated by media type, over the last 180 days. -> [!div class="mx-imgBorder"] -> 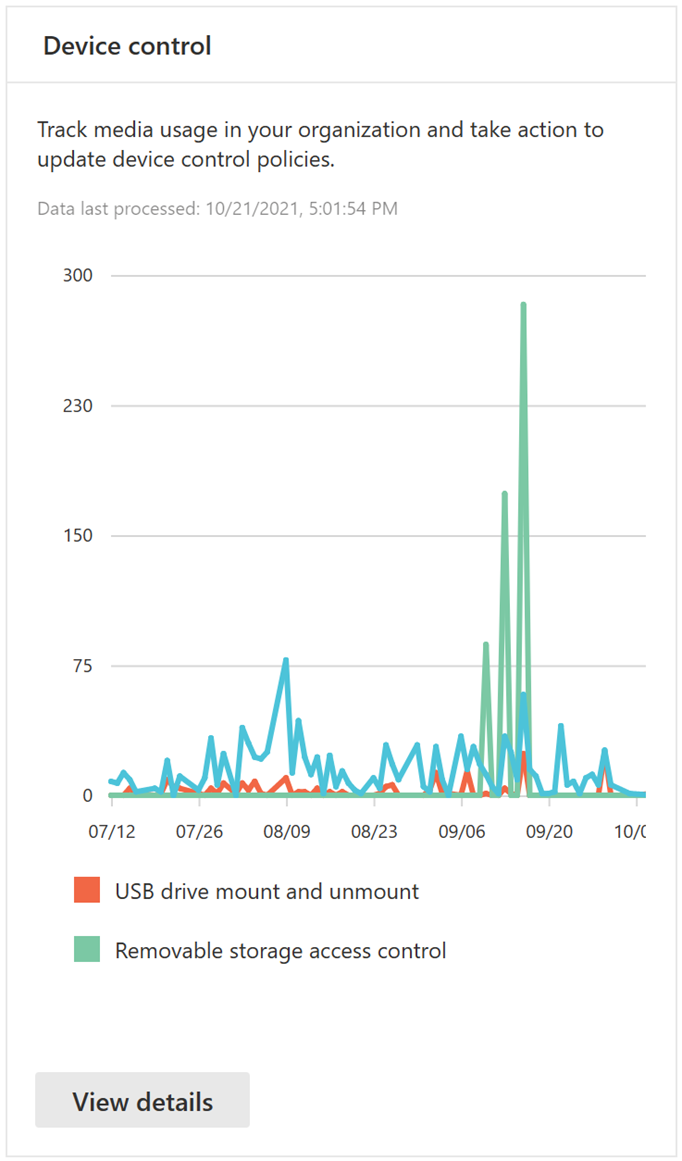 - The **View details** button shows more media usage data in the **device control report** page. -The page provides a dashboard with aggregated number of events per type and a list of events. Administrators can filter on time range, media class name, and device ID. +The page provides a dashboard with aggregated number of events per type and a list of events and shows 500 events per page, but Administrators can scroll down to see more events and can filter on time range, media class name, and device ID. > [!div class="mx-imgBorder"] > :::image type="content" source="images/Detaileddevicecontrolreport.png" alt-text="The Device Control Report Details page in the Microsoft 365 Defender portal" lightbox="images/Detaileddevicecontrolreport.png"::: To see the security of the device, select the **Open device page** button on the ## Reporting delays -The device control report can have a 12-hour delay from the time a media connection occurs to the time the event is reflected in the card or in the domain list. +There might be a delay of up to 12 hours from the time a media connection occurs to the time the event is reflected in the card or in the domain list. |
| security | Exposed Apis Create App Partners | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/exposed-apis-create-app-partners.md | Title: Create an Application to access Microsoft Defender for Endpoint without a user + Title: Partner access through Microsoft Defender for Endpoint APIs -description: Learn how to design a web app to get programmatic access to Microsoft Defender for Endpoint without a user. +description: Learn how to design a web app to get programmatic access to Microsoft Defender for Endpoint on behalf of your users. keywords: apis, graph api, supported apis, actor, alerts, device, user, domain, ip, file, advanced hunting, query ms.prod: m365-security ms.mktglfcycl: deploy return $token ### Using C# -> The below code was tested with Nuget Microsoft.IdentityModel.Clients.ActiveDirectory +> The below code was tested with Nuget Microsoft.Identity.Client > [!IMPORTANT]-> The [Microsoft.IdentityModel.Clients.ActiveDirectory](https://www.nuget.org/packages/Microsoft.IdentityModel.Clients.ActiveDirectory) NuGet package and Azure AD Authentication Library (ADAL) have been deprecated. No new features have been added since June 30, 2020. We strongly encourage you to upgrade, see the [migration guide](/azure/active-directory/develop/msal-migration) for more details. +> The [Microsoft.IdentityModel.Clients.ActiveDirectory](https://www.nuget.org/packages/Microsoft.IdentityModel.Clients.ActiveDirectory) NuGet package and Azure AD Authentication Library (ADAL) have been deprecated. No new features have been added since June 30, 2020. We strongly encourage you to upgrade, see the [migration guide](/azure/active-directory/develop/msal-migration) for more details. - Create a new Console Application-- Install NuGet [Microsoft.IdentityModel.Clients.ActiveDirectory](https://www.nuget.org/packages/Microsoft.IdentityModel.Clients.ActiveDirectory/)+- Install NuGet [Microsoft.Identity.Client](https://www.nuget.org/packages/Microsoft.Identity.Client/) - Add the below using ```console- using Microsoft.IdentityModel.Clients.ActiveDirectory; + using Microsoft.Identity.Client; ``` - Copy/Paste the below code in your application (do not forget to update the three variables: `tenantId`, `appId`, and `appSecret`) - ```console + ```csharp string tenantId = "00000000-0000-0000-0000-000000000000"; // Paste your own tenant ID here string appId = "11111111-1111-1111-1111-111111111111"; // Paste your own app ID here- string appSecret = "22222222-2222-2222-2222-222222222222"; // Paste your own app secret here for a test, and then store it in a safe place! + string appSecret = "22222222-2222-2222-2222-222222222222"; // Paste your own app secret here for a test, and then store it in a safe place! + const string authority = https://login.microsoftonline.com; + const string audience = https://api.securitycenter.microsoft.com; ++ IConfidentialClientApplication myApp = ConfidentialClientApplicationBuilder.Create(appId).WithClientSecret(appSecret).WithAuthority($"{authority}/{tenantId}").Build(); ++ List<string> scopes = new List<string>() { $"{audience}/.default" }; - const string authority = "https://login.microsoftonline.com"; - const string wdatpResourceId = "https://api.securitycenter.microsoft.com"; + AuthenticationResult authResult = myApp.AcquireTokenForClient(scopes).ExecuteAsync().GetAwaiter().GetResult(); - AuthenticationContext auth = new AuthenticationContext($"{authority}/{tenantId}/"); - ClientCredential clientCredential = new ClientCredential(appId, appSecret); - AuthenticationResult authenticationResult = auth.AcquireTokenAsync(wdatpResourceId, clientCredential).GetAwaiter().GetResult(); - string token = authenticationResult.AccessToken; + string token = authResult.AccessToken; ``` ### Using Python |
| security | Exposed Apis Create App Webapp | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/exposed-apis-create-app-webapp.md | $token ### Use C#: -The following code was tested with NuGet Microsoft.IdentityModel.Clients.ActiveDirectory 3.19.8. +The following code was tested with NuGet Microsoft.Identity.Client 3.19.8. > [!IMPORTANT] > The [Microsoft.IdentityModel.Clients.ActiveDirectory](https://www.nuget.org/packages/Microsoft.IdentityModel.Clients.ActiveDirectory) NuGet package and Azure AD Authentication Library (ADAL) have been deprecated. No new features have been added since June 30, 2020. We strongly encourage you to upgrade, see the [migration guide](/azure/active-directory/develop/msal-migration) for more details. 1. Create a new console application.-1. Install NuGet [Microsoft.IdentityModel.Clients.ActiveDirectory](https://www.nuget.org/packages/Microsoft.IdentityModel.Clients.ActiveDirectory/). +1. Install NuGet [Microsoft.Identity.Client](https://www.nuget.org/packages/Microsoft.Identity.Client/). 1. Add the following: ```csharp- using Microsoft.IdentityModel.Clients.ActiveDirectory; + using Microsoft.Identity.Client; ``` 1. Copy and paste the following code in your app (don't forget to update the three variables: ```tenantId, appId, appSecret```): The following code was tested with NuGet Microsoft.IdentityModel.Clients.ActiveD string tenantId = "00000000-0000-0000-0000-000000000000"; // Paste your own tenant ID here string appId = "11111111-1111-1111-1111-111111111111"; // Paste your own app ID here string appSecret = "22222222-2222-2222-2222-222222222222"; // Paste your own app secret here for a test, and then store it in a safe place! + const string authority = https://login.microsoftonline.com; + const string audience = https://api.securitycenter.microsoft.com; - const string authority = "https://login.microsoftonline.com"; - const string wdatpResourceId = "https://api.securitycenter.microsoft.com"; + IConfidentialClientApplication myApp = ConfidentialClientApplicationBuilder.Create(appId).WithClientSecret(appSecret).WithAuthority($"{authority}/{tenantId}").Build(); - AuthenticationContext auth = new AuthenticationContext($"{authority}/{tenantId}/"); - ClientCredential clientCredential = new ClientCredential(appId, appSecret); - AuthenticationResult authenticationResult = auth.AcquireTokenAsync(wdatpResourceId, clientCredential).GetAwaiter().GetResult(); - string token = authenticationResult.AccessToken; - console.write(token) - ``` + List<string> scopes = new List<string>() { $"{audience}/.default" }; + AuthenticationResult authResult = myApp.AcquireTokenForClient(scopes).ExecuteAsync().GetAwaiter().GetResult(); + string token = authResult.AccessToken; + ``` ### Use Python See [Get token using Python](run-advanced-query-sample-python.md#get-token). |
| security | Api Create App User Context | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender/api-create-app-user-context.md | This article explains how to: For more information on Azure Active Directory tokens, see the [Azure AD tutorial](/azure/active-directory/develop/active-directory-v2-protocols-oauth-client-creds). -### Get an access token using PowerShell +### Get an access token on behalf of a user using PowerShell -```PowerShell -if(!(Get-Package adal.ps)) { Install-Package -Name adal.ps } # Install the ADAL.PS package in case it's not already present +Use the MSAL.PS library to acquire access tokens with Delegated permissions. Run the following commands to get access token on behalf of a user: -$tenantId = '' # Paste your directory (tenant) ID here. -$clientId = '' # Paste your application (client) ID here. -$redirectUri = '' # Paste your app's redirection URI +```PowerShell +Install-Module -Name MSAL.PS # Install the MSAL.PS module from PowerShell Gallery -$authority = "https://login.windows.net/$tenantId" -$resourceUrl = 'https://api.security.microsoft.com' +$TenantId = " " # Paste your directory (tenant) ID here. +$AppClientId="xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx" # Paste your application (client) ID here. -$response = Get-ADALToken -Resource $resourceUrl -ClientId $clientId -RedirectUri $redirectUri -Authority $authority -PromptBehavior:Always -$response.AccessToken | clip +$MsalParams = @{ + ClientId = $AppClientId + TenantId = $TenantId + Scopes = 'https://graph.microsoft.com/User.Read.All','https://graph.microsoft.com/Files.ReadWrite' +} -$response.AccessToken +$MsalResponse = Get-MsalToken @MsalParams +$AccessToken = $MsalResponse.AccessToken + +$AccessToken # Display the token in PS console ```- ## Validate the token 1. Copy and paste the token into [JWT](https://jwt.ms) to decode it.-1. Make sure that the *roles* claim within the decoded token contains the desired permissions. +2. Make sure that the *roles* claim within the decoded token contains the desired permissions. In the following image, you can see a decoded token acquired from an app, with ```Incidents.Read.All```, ```Incidents.ReadWrite.All```, and ```AdvancedHunting.Read.All``` permissions: |
| security | Api Create App Web | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender/api-create-app-web.md | return $token ### Get an access token using C\# > [!NOTE]-> The following code was tested with Nuget Microsoft.IdentityModel.Clients.ActiveDirectory 3.19.8. +> The following code was tested with Nuget Microsoft.Identity.Client 3.19.8. > [!IMPORTANT] > The [Microsoft.IdentityModel.Clients.ActiveDirectory](https://www.nuget.org/packages/Microsoft.IdentityModel.Clients.ActiveDirectory) NuGet package and Azure AD Authentication Library (ADAL) have been deprecated. No new features have been added since June 30, 2020. We strongly encourage you to upgrade, see the [migration guide](/azure/active-directory/develop/msal-migration) for more details. 1. Create a new console application. -1. Install NuGet [Microsoft.IdentityModel.Clients.ActiveDirectory](https://www.nuget.org/packages/Microsoft.IdentityModel.Clients.ActiveDirectory/). +1. Install NuGet [Microsoft.Identity.Client](https://www.nuget.org/packages/Microsoft.Identity.Client/). 1. Add the following line: ```C#- using Microsoft.IdentityModel.Clients.ActiveDirectory; + using Microsoft.Identity.Client; ``` 1. Copy and paste the following code into your app (don't forget to update the three variables: `tenantId`, `clientId`, `appSecret`): ```C#- string tenantId = ""; // Paste your directory (tenant) ID here - string clientId = ""; // Paste your application (client) ID here - string appSecret = ""; // Paste your own app secret here to test, then store it in a safe place, such as the Azure Key Vault! + csharp + string tenantId = "00000000-0000-0000-0000-000000000000"; // Paste your own tenant ID here + string appId = "11111111-1111-1111-1111-111111111111"; // Paste your own app ID here + string appSecret = "22222222-2222-2222-2222-222222222222"; // Paste your own app secret here for a test, and then store it in a safe place! + const string authority = https://login.microsoftonline.com; + const string audience = https://api.securitycenter.microsoft.com; - const string authority = "https://login.windows.net"; - const string wdatpResourceId = "https://api.security.microsoft.com"; + IConfidentialClientApplication myApp = ConfidentialClientApplicationBuilder.Create(appId).WithClientSecret(appSecret).WithAuthority($"{authority}/{tenantId}").Build(); - AuthenticationContext auth = new AuthenticationContext($"{authority}/{tenantId}/"); - ClientCredential clientCredential = new ClientCredential(clientId, appSecret); - AuthenticationResult authenticationResult = auth.AcquireTokenAsync(wdatpResourceId, clientCredential).GetAwaiter().GetResult(); - string token = authenticationResult.AccessToken; + List<string> scopes = new List<string>() { $"{audience}/.default" }; ++ AuthenticationResult authResult = myApp.AcquireTokenForClient(scopes).ExecuteAsync().GetAwaiter().GetResult(); ++ string token = authResult.AccessToken; ``` ### Get an access token using Python |
| security | Api Partner Access | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender/api-partner-access.md | return $token ### Get an access token using C\# > [!NOTE]-> The following code was tested with Nuget Microsoft.IdentityModel.Clients.ActiveDirectory 3.19.8. +> The following code was tested with Nuget Microsoft.Identity.Client 3.19.8. > [!IMPORTANT] > The [Microsoft.IdentityModel.Clients.ActiveDirectory](https://www.nuget.org/packages/Microsoft.IdentityModel.Clients.ActiveDirectory) NuGet package and Azure AD Authentication Library (ADAL) have been deprecated. No new features have been added since June 30, 2020. We strongly encourage you to upgrade, see the [migration guide](/azure/active-directory/develop/msal-migration) for more details. 1. Create a new console application.-1. Install NuGet [Microsoft.IdentityModel.Clients.ActiveDirectory](https://www.nuget.org/packages/Microsoft.IdentityModel.Clients.ActiveDirectory/). +1. Install NuGet [Microsoft.Identity.Client](https://www.nuget.org/packages/Microsoft.Identity.Client/). 1. Add the following line: ```C#- using Microsoft.IdentityModel.Clients.ActiveDirectory; + using Microsoft.Identity.Client; ``` 1. Copy and paste the following code into your app (don't forget to update the three variables: `tenantId`, `clientId`, `appSecret`): ```C#- string tenantId = ""; // Paste your directory (tenant) ID here - string clientId = ""; // Paste your application (client) ID here - string appSecret = ""; // Paste your own app secret here to test, then store it in a safe place, such as the Azure Key Vault! + string tenantId = "00000000-0000-0000-0000-000000000000"; // Paste your own tenant ID here + string appId = "11111111-1111-1111-1111-111111111111"; // Paste your own app ID here + string appSecret = "22222222-2222-2222-2222-222222222222"; // Paste your own app secret here for a test, and then store it in a safe place! + const string authority = https://login.microsoftonline.com; + const string audience = https://api.securitycenter.microsoft.com; - const string authority = "https://login.windows.net"; - const string wdatpResourceId = "https://api.security.microsoft.com"; + IConfidentialClientApplication myApp = ConfidentialClientApplicationBuilder.Create(appId).WithClientSecret(appSecret).WithAuthority($"{authority}/{tenantId}").Build(); - AuthenticationContext auth = new AuthenticationContext($"{authority}/{tenantId}/"); - ClientCredential clientCredential = new ClientCredential(clientId, appSecret); - AuthenticationResult authenticationResult = auth.AcquireTokenAsync(wdatpResourceId, clientCredential).GetAwaiter().GetResult(); - string token = authenticationResult.AccessToken; + List<string> scopes = new List<string>() { $"{audience}/.default" }; ++ AuthenticationResult authResult = myApp.AcquireTokenForClient(scopes).ExecuteAsync().GetAwaiter().GetResult(); ++ string token = authResult.AccessToken; ``` ### Get an access token using Python |
| security | Mssp Access | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender/mssp-access.md | To implement a multi-tenant delegated access solution, take the following steps: At this point, analyst access has been provisioned, and each analyst should be able to access the customer's Microsoft 365 Defender portal: `https://security.microsoft.com/?tid=<CustomerTenantId>` with the permissions and roles they were assigned.--> [!IMPORTANT] -> Delegated access to Microsoft Defender for Endpoint in the Microsoft 365 Defender portal currently allows access to a single tenant per browser window. |
| security | Admin Submission | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/office-365-security/admin-submission.md | On the **User reported messages** tab, select a message in the list, click **Sub > [!div class="mx-imgBorder"] > :::image type="content" source="../../media/admin-submission-main-action-button.png" alt-text="The New options on the Action button" lightbox="../../media/admin-submission-main-action-button.png":::++If the message is reported to Microsoft, the **Converted to admin submission** value turns from **no** to **yes**. You can directly access the admin submission by clicking **View the converted admin submission** from the overflow menu inside the submission flyout of the respective user reported message. + |
| security | Anti Malware Protection | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/office-365-security/anti-malware-protection.md | Anti-malware policies control the settings and notification options for malware You can only use a condition or exception once, but the condition or exception can contain multiple values. Multiple values of the same condition or exception use OR logic (for example, _\<recipient1\>_ or _\<recipient2\>_). Different conditions or exceptions use AND logic (for example, _\<recipient1\>_ and _\<member of group 1\>_). + > [!IMPORTANT] + > Multiple different conditions or exceptions are not additive; they're inclusive. The policy is applied _only_ to those recipients that match _all_ of the specified recipient filters. For example, you configure a recipient filter condition in the policy with the following values: + > + > - The recipient is: romain@contoso.com + > - The recipient is a member of: Executives + > + > The policy is applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy is not applied to him. + > + > Likewise, if you use the same recipient filter as an exception to the policy, the policy is not applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy still applies to him. + - **Priority**: If you create multiple custom anti-malware policies, you can specify the order that they're applied. No two policies can have the same priority, and policy processing stops after the first policy is applied. For more information about the order of precedence and how multiple policies are evaluated and applied, see [Order and precedence of email protection](how-policies-and-protections-are-combined.md). |
| security | Configure Anti Malware Policies | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/office-365-security/configure-anti-malware-policies.md | Creating a custom anti-malware policy in the Microsoft 365 Defender portal creat - **Exclude these users, groups, and domains**: To add exceptions for the internal recipients that the policy applies to (recipient exceptions), select this option and configure the exceptions. The settings and behavior are exactly like the conditions. + > [!IMPORTANT] + > Multiple different conditions or exceptions are not additive; they're inclusive. The policy is applied _only_ to those recipients that match _all_ of the specified recipient filters. For example, you configure a recipient filter condition in the policy with the following values: + > + > - The recipient is: romain@contoso.com + > - The recipient is a member of: Executives + > + > The policy is applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy is not applied to him. + > + > Likewise, if you use the same recipient filter as an exception to the policy, the policy is not applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy still applies to him. + When you're finished, click **Next**. 5. On the **Protection settings** page that appears, configure the following settings: |
| security | Configure Anti Phishing Policies Eop | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/office-365-security/configure-anti-phishing-policies-eop.md | Creating a custom anti-phishing policy in the Microsoft 365 Defender portal crea - **Exclude these users, groups, and domains**: To add exceptions for the internal recipients that the policy applies to (recipient exceptions), select this option and configure the exceptions. The settings and behavior are exactly like the conditions. + > [!IMPORTANT] + > Multiple different conditions or exceptions are not additive; they're inclusive. The policy is applied _only_ to those recipients that match _all_ of the specified recipient filters. For example, you configure a recipient filter condition in the policy with the following values: + > + > - The recipient is: romain@contoso.com + > - The recipient is a member of: Executives + > + > The policy is applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy is not applied to him. + > + > Likewise, if you use the same recipient filter as an exception to the policy, the policy is not applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy still applies to him. + When you're finished, click **Next**. 5. On the **Phishing threshold & protection** page that appears, use the **Enable spoof intelligence** check box to turn spoof intelligence on or off. The default value is on (selected), and we recommend that you leave it on. You configure the action to take on blocked spoofed messages on the next page. |
| security | Configure Mdo Anti Phishing Policies | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/office-365-security/configure-mdo-anti-phishing-policies.md | Creating a custom anti-phishing policy in the Microsoft 365 Defender portal crea Multiple values in the same condition use OR logic (for example, _\<recipient1\>_ or _\<recipient2\>_). Different conditions use AND logic (for example, _\<recipient1\>_ and _\<member of group 1\>_). - - **Exclude these users, groups, and domains**: To add exceptions for the internal recipients that the policy applies to (recpient exceptions), select this option and configure the exceptions. The settings and behavior are exactly like the conditions. + - **Exclude these users, groups, and domains**: To add exceptions for the internal recipients that the policy applies to (recipient exceptions), select this option and configure the exceptions. The settings and behavior are exactly like the conditions. ++ > [!IMPORTANT] + > Multiple different conditions or exceptions are not additive; they're inclusive. The policy is applied _only_ to those recipients that match _all_ of the specified recipient filters. For example, you configure a recipient filter condition in the policy with the following values: + > + > - The recipient is: romain@contoso.com + > - The recipient is a member of: Executives + > + > The policy is applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy is not applied to him. + > + > Likewise, if you use the same recipient filter as an exception to the policy, the policy is not applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy still applies to him. When you're finished, click **Next**. |
| security | Configure The Outbound Spam Policy | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/office-365-security/configure-the-outbound-spam-policy.md | Creating a custom outbound spam policy in the Microsoft 365 Defender portal crea - **Exclude these users, groups, and domains**: To add exceptions for the internal senders that the policy applies to (recipient exceptions), select this option and configure the exceptions. The settings and behavior are exactly like the conditions. + > [!IMPORTANT] + > Multiple different conditions or exceptions are not additive; they're inclusive. The policy is applied _only_ to those recipients that match _all_ of the specified recipient filters. For example, you configure a recipient filter condition in the policy with the following values: + > + > - The recipient is: romain@contoso.com + > - The recipient is a member of: Executives + > + > The policy is applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy is not applied to him. + > + > Likewise, if you use the same recipient filter as an exception to the policy, the policy is not applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy still applies to him. + When you're finished, click **Next**. 5. On the **Protection settings** page that opens, configure the following settings: |
| security | Configure Your Spam Filter Policies | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/office-365-security/configure-your-spam-filter-policies.md | Creating a custom anti-spam policy in the Microsoft 365 Defender portal creates - **Exclude these users, groups, and domains**: To add exceptions for the internal recipients that the policy applies to (recipient exceptions), select this option and configure the exceptions. The settings and behavior are exactly like the conditions. + > [!IMPORTANT] + > Multiple different conditions or exceptions are not additive; they're inclusive. The policy is applied _only_ to those recipients that match _all_ of the specified recipient filters. For example, you configure a recipient filter condition in the policy with the following values: + > + > - The recipient is: romain@contoso.com + > - The recipient is a member of: Executives + > + > The policy is applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy is not applied to him. + > + > Likewise, if you use the same recipient filter as an exception to the policy, the policy is not applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy still applies to him. + When you're finished, click **Next**. 5. On the **Bulk email threshold & spam properties** page that appears, configure the following settings: |
| security | Preset Security Policies | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/office-365-security/preset-security-policies.md | A profile determines the level of protection. The following profiles are availab You can only use a condition or exception once, but you can specify multiple values for the condition or exception. Multiple values of the same condition or exception use OR logic (for example, _\<recipient1\>_ or _\<recipient2\>_). Different conditions or exceptions use AND logic (for example, _\<recipient1\>_ and _\<member of group 1\>_). + > [!IMPORTANT] + > Multiple different conditions or exceptions are not additive; they're inclusive. The policy is applied _only_ to those recipients that match _all_ of the specified recipient filters. For example, you configure a recipient filter condition in the policy with the following values: + > + > - The recipient is: romain@contoso.com + > - The recipient is a member of: Executives + > + > The policy is applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy is not applied to him. + > + > Likewise, if you use the same recipient filter as an exception to the policy, the policy is not applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy still applies to him. + - **Built-in protection** (Defender for Office 365 only): A profile that enables Safe Links and Safe Attachments protection only. This profile effectively provides default policies for Safe Links and Safe Attachments, which never had default policies. For **Built-in protection**, the preset security policy is on by default for all Defender for Office 365 customers. Although we don't recommend it, you can also configure exceptions based on **Users**, **Groups**, and **Domains** so the protection isn't applied to specific users. |
| security | Quarantine Policies | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/office-365-security/quarantine-policies.md | The global settings for quarantine policies allow you to customize the quarantin :::image type="content" source="../../media/quarantine-tags-esn-customization-disclaimer.png" alt-text="A custom disclaimer at the bottom of a quarantine notification." lightbox="../../media/quarantine-tags-esn-customization-disclaimer.png"::: - - The language identifier for the the **Display name** and **Disclaimer** values. Quarantine notifications are already localized based on the recipient's language settings. The **Display name** and **Disclaimer** values are used in quarantine notifications that apply to the recipient's language. + - The language identifier for the **Display name** and **Disclaimer** values. Quarantine notifications are already localized based on the recipient's language settings. The **Display name** and **Disclaimer** values are used in quarantine notifications that apply to the recipient's language. Select the language in the **Choose language** box _before_ you enter values in the **Display name** and **Disclaimer** boxes. When you change the value in the **Choose language** box, the values in the **Display name** and **Disclaimer** boxes are emptied. If the quarantine policy assigns the **Full access** permissions (all available :::image type="content" source="../../media/quarantine-tags-esn-full-access.png" alt-text="The available buttons in the quarantine notification if the quarantine policy gives the user full access permissions" lightbox="../../media/quarantine-tags-esn-full-access.png"::: +> [!NOTE] +> As explained earlier, quarantine notifications are disabled in the default quarantine policy named DefaultFullAccessPolicy, even though that quarantine policy has the **Full access** permission group assigned. Quarantine notifications are available only in custom quarantine policies that you create or in the default quarantine access policy named NotificationEnabledPolicy ([if that policy is available in your organization](#full-access-permissions-and-quarantine-notifications)). + ### Individual permissions #### Block sender permission |
| security | Remediate Malicious Email Delivered Office 365 | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/office-365-security/remediate-malicious-email-delivered-office-365.md | Remediation means taking a prescribed action against a threat. Malicious email s Admins can take required action on emails, but to get those actions approved, they must have the *Search and Purge* role assigned to them in the **Email & collaboration** permissions in the Microsoft 365 Defender portal. Without the *Search and purge"*role added to one of the role-groups, they won't be able to execute the action. +Because email actions create automated investigations in the backend, you need to enable *Automated Investigation*. Go to **Settings** \> **Endpoints** \> **Advanced features** and turn on **Automated Investigation**. + ## Manual and automated remediation *Manual hunting* occurs when security teams identify threats manually by using the search and filtering capabilities in Explorer. Manual email remediation can be triggered through any email view (*Malware*, *Phish*, or *All email*) after you identify a set of emails that need to be remediated. |
| security | Safe Attachments | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/office-365-security/safe-attachments.md | This section describes the settings in Safe Attachments policies: You can only use a condition or exception once, but the condition or exception can contain multiple values. Multiple values of the same condition or exception use OR logic (for example, _\<recipient1\>_ or _\<recipient2\>_). Different conditions or exceptions use AND logic (for example, _\<recipient1\>_ and _\<member of group 1\>_). + > [!IMPORTANT] + > Multiple different conditions or exceptions are not additive; they're inclusive. The policy is applied _only_ to those recipients that match _all_ of the specified recipient filters. For example, you configure a recipient filter condition in the policy with the following values: + > + > - The recipient is: romain@contoso.com + > - The recipient is a member of: Executives + > + > The policy is applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy is not applied to him. + > + > Likewise, if you use the same recipient filter as an exception to the policy, the policy is not applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy still applies to him. + - **Priority**: If you create multiple policies, you can specify the order that they're applied. No two policies can have the same priority, and policy processing stops after the first policy is applied. For more information about the order of precedence and how multiple policies are evaluated and applied, see [Order and precedence of email protection](how-policies-and-protections-are-combined.md). |
| security | Safe Links | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/office-365-security/safe-links.md | The settings in Safe Links policies that apply to email messages are described i You can only use a condition or exception once, but the condition or exception can contain multiple values. Multiple values of the same condition or exception use OR logic (for example, _\<recipient1\>_ or _\<recipient2\>_). Different conditions or exceptions use AND logic (for example, _\<recipient1\>_ and _\<member of group 1\>_). + > [!IMPORTANT] + > Multiple different conditions or exceptions are not additive; they're inclusive. The policy is applied _only_ to those recipients that match _all_ of the specified recipient filters. For example, you configure a recipient filter condition in the policy with the following values: + > + > - The recipient is: romain@contoso.com + > - The recipient is a member of: Executives + > + > The policy is applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy is not applied to him. + > + > Likewise, if you use the same recipient filter as an exception to the policy, the policy is not applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy still applies to him. + - **Priority**: If you create multiple policies, you can specify the order that they're applied. No two policies can have the same priority, and policy processing stops after the first policy is applied. For more information about the order of precedence and how multiple policies are evaluated and applied, see [Order and precedence of email protection](how-policies-and-protections-are-combined.md). |
| security | Set Up Anti Phishing Policies | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/office-365-security/set-up-anti-phishing-policies.md | The following policy settings are available in anti-phishing policies in EOP and > [!NOTE] > At least one selection in the **Users, groups, and domains** settings is required in custom anti-phishing policies to identify the message **recipients** <u>that the policy applies to</u>. Anti-phishing policies in Defender for Office 365 also have [impersonation settings](#impersonation-settings-in-anti-phishing-policies-in-microsoft-defender-for-office-365) where you can specify individual sender email addresses or sender domains <u>that will receive impersonation protection</u> as described later in this article.+ > + > Multiple different conditions or exceptions are not additive; they're inclusive. The policy is applied _only_ to those recipients that match _all_ of the specified recipient filters. For example, you configure a recipient filter condition in the policy with the following values: + > + > - The recipient is: romain@contoso.com + > - The recipient is a member of: Executives + > + > The policy is applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy is not applied to him. + > + > Likewise, if you use the same recipient filter as an exception to the policy, the policy is not applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy still applies to him. ## Spoof settings |
| security | Set Up Safe Attachments Policies | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/office-365-security/set-up-safe-attachments-policies.md | Creating a custom Safe Attachments policy in the Microsoft 365 Defender portal c Multiple values in the same condition use OR logic (for example, _\<recipient1\>_ or _\<recipient2\>_). Different conditions use AND logic (for example, _\<recipient1\>_ and _\<member of group 1\>_). - - **Exclude these users, groups, and domains**: To add exceptions for the internal recipients that the policy applies to (recpient exceptions), select this option and configure the exceptions. The settings and behavior are exactly like the conditions. + - **Exclude these users, groups, and domains**: To add exceptions for the internal recipients that the policy applies to (recipient exceptions), select this option and configure the exceptions. The settings and behavior are exactly like the conditions. ++ > [!IMPORTANT] + > Multiple different conditions or exceptions are not additive; they're inclusive. The policy is applied _only_ to those recipients that match _all_ of the specified recipient filters. For example, you configure a recipient filter condition in the policy with the following values: + > + > - The recipient is: romain@contoso.com + > - The recipient is a member of: Executives + > + > The policy is applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy is not applied to him. + > + > Likewise, if you use the same recipient filter as an exception to the policy, the policy is not applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy still applies to him. When you're finished, click **Next**. |
| security | Set Up Safe Links Policies | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/office-365-security/set-up-safe-links-policies.md | Creating a custom Safe Links policy in the Microsoft 365 Defender portal creates - **Exclude these users, groups, and domains**: To add exceptions for the internal recipients that the policy applies to (recipient exceptions), select this option and configure the exceptions. The settings and behavior are exactly like the conditions. + > [!IMPORTANT] + > Multiple different conditions or exceptions are not additive; they're inclusive. The policy is applied _only_ to those recipients that match _all_ of the specified recipient filters. For example, you configure a recipient filter condition in the policy with the following values: + > + > - The recipient is: romain@contoso.com + > - The recipient is a member of: Executives + > + > The policy is applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy is not applied to him. + > + > Likewise, if you use the same recipient filter as an exception to the policy, the policy is not applied to romain@contoso.com _only_ if he's also a member of the Executives groups. If he's not a member of the group, then the policy still applies to him. + When you're finished, click **Next**. 5. On the **Protection settings** page that appears, configure the following settings: |
| security | View Reports For Mdo | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/office-365-security/view-reports-for-mdo.md | Microsoft Defender for Office 365 organizations (for example, Microsoft 365 E5 s ### Download reports -1. In the Microsoft 365 Defender portal at <https://security.microsoft.com>, go to **Reports** > **Email & collaboration** \> **Reports for download**. To go directly to the **Reports for download** page, use <https://security.microsoft.com/ReportsForDownload?viewid=custom>. +In the Microsoft 365 Defender portal at <https://security.microsoft.com>, go to **Reports** > **Email & collaboration** \> **Reports for download**. To go directly to the **Reports for download** page, use <https://security.microsoft.com/ReportsForDownload?viewid=custom>. :::image type="content" source="../../media/email-collaboration-download-reports.png" alt-text="The Email & collaboration reports page in the Microsoft 365 Defender portal" lightbox="../../media/email-collaboration-download-reports.png"::: |