| Category | Microsoft Docs article | Related commit history on GitHub | Change details |
|---|---|---|---|
| business-premium | M365bp Mdb Whats New | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/business-premium/m365bp-mdb-whats-new.md | This article lists new features in the latest release of [Microsoft 365 Business ## November 2022 -- **[Microsoft Defender for Business servers](../security/defender-business/get-defender-business-servers.md)**, a new add-on for Defender for Business, is now generally available. See [How to get Microsoft Defender for Business servers](../security/defender-business/get-defender-business-servers.md).+- **[Microsoft Defender for Business servers](../security/defender-business/get-defender-business-servers.md)**, a new add-on for Defender for Business, is now generally available. To learn more, see the following articles: + - [How to get Microsoft Defender for Business servers](../security/defender-business/get-defender-business-servers.md) + - [Tech Community Blog: Server security made simple for small businesses](https://techcommunity.microsoft.com/t5/small-and-medium-business-blog/server-security-made-simple-for-small-businesses/ba-p/3648928) ++- **License reporting (preview) in Defender for Business**. A new report (rolling out in preview) enables you to view your Defender for Business license usage. To learn more, see [Reports in Microsoft Defender for Business](../security/defender-business/mdb-reports.md). ## July 2022 This article lists new features in the latest release of [Microsoft 365 Business ## May 2022 -- **Defender for Business** (standalone) is now generally available. See the following resources to learn more:+- **Defender for Business** (standalone) is now generally available. To learn more, see the following resources: - [Tech Community blog: Introducing Microsoft Defender for Business](https://techcommunity.microsoft.com/t5/small-and-medium-business-blog/introducing-microsoft-defender-for-business/ba-p/2898701) - [What is Microsoft Defender for Business?](../security/defender-business/mdb-overview.md) This article lists new features in the latest release of [Microsoft 365 Business ## March 2022 -- **Microsoft 365 Business Premium now includes Defender for Business**. See [Tech Community blog: New security solutions to help secure small and medium businesses](https://techcommunity.microsoft.com/t5/small-and-medium-business-blog/new-security-solutions-to-help-secure-small-and-medium/ba-p/3207043).+- **Microsoft 365 Business Premium now includes Defender for Business**. To learn more, see [Tech Community blog: New security solutions to help secure small and medium businesses](https://techcommunity.microsoft.com/t5/small-and-medium-business-blog/new-security-solutions-to-help-secure-small-and-medium/ba-p/3207043). ## See also |
| compliance | Insider Risk Management Configure | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/insider-risk-management-configure.md | There are six role groups used to configure insider risk management features. To - Microsoft Purview compliance portal [*Organization Management*](/microsoft-365/security/office-365-security/permissions-in-the-security-and-compliance-center) role group - Microsoft Purview compliance portal [*Compliance Administrator*](/microsoft-365/security/office-365-security/permissions-in-the-security-and-compliance-center) role group - *Insider Risk Management* role group-- *Insider Risk Management Admin* role group+- *Insider Risk Management Admins* role group Depending on how you wish to manage insider risk management policies and alerts, you'll need to assign users to specific role groups to manage different sets of insider risk management features. You have the option to assign users with different compliance responsibilities to specific role groups to manage different areas of insider risk management features. Or you may decide to assign all user accounts for designated administrators, analysts, investigators, and viewers to the Insider Risk Management role group. Use a single role group or multiple role groups to best fit your compliance management requirements. You'll choose from these role group options and solution actions when working with insider risk management: -|**Actions**|**Insider Risk Management**|**Insider Risk Management Admin**|**Insider Risk Management Analysts**|**Insider Risk Management Investigators**|**Insider Risk Management Auditors**|**Insider Risk Management Approvers**| +|**Actions**|**Insider Risk Management**|**Insider Risk Management Admins**|**Insider Risk Management Analysts**|**Insider Risk Management Investigators**|**Insider Risk Management Auditors**|**Insider Risk Management Approvers**| |||||||| |Configure policies and settings|Yes|Yes|No|No|No|No| |Access analytics insights|Yes|Yes|Yes|No|No|No| You'll choose from these role group options and solution actions when working wi |View device health report|Yes|Yes|No|No|No|No| > [!IMPORTANT]-> Make sure you always have at least one user in the built-in *Insider Risk Management* or *Insider Risk Management Admin* role groups (depending on the option you choose) so that your insider risk management configuration doesn't get into a 'zero administrator' scenario if specific users leave your organization. +> Make sure you always have at least one user in the built-in *Insider Risk Management* or *Insider Risk Management Admins* role groups (depending on the option you choose) so that your insider risk management configuration doesn't get into a 'zero administrator' scenario if specific users leave your organization. -Members of the following roles can assign users to insider risk management role groups and have the same solution permissions included with the *Insider Risk Management Admin* role group: +Members of the following roles can assign users to insider risk management role groups and have the same solution permissions included with the *Insider Risk Management Admins* role group: - Azure Active Directory *Global Administrator* - Azure Active Directory *Compliance Administrator* For step-by-step instructions to turn on auditing, see [Turn audit log search on Insider risk management analytics enables you to conduct an evaluation of potential insider risks in your organization without configuring any insider risk policies. This evaluation can help your organization identify potential areas of higher user risk and help determine the type and scope of insider risk management policies you may consider configuring. This evaluation may also help you determine needs for additional licensing or future optimization of existing policies. Analytics scan results may take up to 48 hours before insights are available as reports for review. To learn more about analytics insights, see [Insider risk management settings: Analytics](insider-risk-management-settings.md#analytics) and check out the [Insider Risk Management Analytics video](https://www.youtube.com/watch?v=5c0P5MCXNXk) to help understand how analytics can help accelerate the identification of potential insider risks and help you to quickly take action. -To enable insider risk analytics, you must be a member of the *Insider Risk Management*, *Insider Risk Management Admin*, or Microsoft 365 *Global admin* role group. +To enable insider risk analytics, you must be a member of the *Insider Risk Management*, *Insider Risk Management Admins*, or Microsoft 365 *Global admin* role group. Complete the following steps to enable insider risk analytics: |
| compliance | Insider Risk Management Content Explorer | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/insider-risk-management-content-explorer.md | The insider risk management **Content explorer** allows users assigned the *Insi To examine the emails and files captured by the policies included in a specific case, navigate to the Insider risk management **Cases** page and select the row of the *Case name* in the list for the case you want to view details for. Then in the case details page, select the **Content explorer** tab to open the Content explorer. > [!IMPORTANT]-> After an alert is confirmed to a case, Content explorer won't display any details for that case if the organization has not assigned a user to either the *Insider Risk Management Investigator* or *Insider Risk Management* role group. +> After an alert is confirmed to a case, Content explorer won't display any details for that case if the organization has not assigned a user to either the *Insider Risk Management Investigators* or *Insider Risk Management* role group. For new cases, it usually takes about an hour for content to populate in Content explorer. For cases with large amounts of content, it may take longer to create a snapshot. If content is still loading in Content explorer, you will see a progress indicator that displays the completion percentage. |
| compliance | Insider Risk Management Plan | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/insider-risk-management-plan.md | Depending on how you want to manage insider risk management policies and alerts, Choose from the following role group options and solution actions when working with insider risk management: -|**Actions**|**Insider Risk Management**|**Insider Risk Management Admin**|**Insider Risk Management Analysts**|**Insider Risk Management Investigators**|**Insider Risk Management Auditors**|**Insider Risk Management Approvers**| +|**Actions**|**Insider Risk Management**|**Insider Risk Management Admins**|**Insider Risk Management Analysts**|**Insider Risk Management Investigators**|**Insider Risk Management Auditors**|**Insider Risk Management Approvers**| |||||||| |Configure policies and settings|Yes|Yes|No|No|No|No| |Access analytics insights|Yes|Yes|Yes|No|No|No| Choose from the following role group options and solution actions when working w |View device health report|Yes|Yes|No|No|No|No| > [!IMPORTANT]-> Make sure you always have at least one user in the *Insider Risk Management* or *Insider Risk Management Admin* role groups (depending on the option you choose) so that your insider risk management configuration doesn't get in to a 'zero administrator' scenario if specific users leave your organization. +> Make sure you always have at least one user in the *Insider Risk Management* or *Insider Risk Management Admins* role groups (depending on the option you choose) so that your insider risk management configuration doesn't get in to a 'zero administrator' scenario if specific users leave your organization. -Members of the following roles can assign users to insider risk management role groups and have the same solution permissions included with the *Insider Risk Management Admin* role group: +Members of the following roles can assign users to insider risk management role groups and have the same solution permissions included with the *Insider Risk Management Admins* role group: - Azure Active Directory *Global Administrator* - Azure Active Directory *Compliance Administrator* |
| compliance | Insider Risk Management Settings | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/insider-risk-management-settings.md | For example, you need to protect against data leaks for a highly confidential pr ### Create a priority user group -To create a new priority user group, use the setting controls in the **Insider risk management** solution in the Microsoft Purview compliance portal. To create a priority user group, you must be a member of the *Insider Risk Management* or *Insider Risk Management Admin* role group. +To create a new priority user group, use the setting controls in the **Insider risk management** solution in the Microsoft Purview compliance portal. To create a priority user group, you must be a member of the *Insider Risk Management* or *Insider Risk Management Admins* role group. Complete the following steps to create a priority user group: Complete the following steps to create a priority user group: ### Update a priority user group -To update an existing priority user group, you'll use setting controls in the **Insider risk management** solution in the Microsoft Purview compliance portal. To update a priority user group, you must be a member of the *Insider Risk Management* or *Insider Risk Management Admin* role group. +To update an existing priority user group, you'll use setting controls in the **Insider risk management** solution in the Microsoft Purview compliance portal. To update a priority user group, you must be a member of the *Insider Risk Management* or *Insider Risk Management Admins* role group. Complete the following steps to edit a priority user group: Complete the following steps to edit a priority user group: ### Delete a priority user group -To delete an existing priority user group, use setting controls in the **Insider risk management** solution in the Microsoft Purview compliance portal. To delete a priority user group, you must be a member of the *Insider Risk Management* or *Insider Risk Management Admin* role group. +To delete an existing priority user group, use setting controls in the **Insider risk management** solution in the Microsoft Purview compliance portal. To delete a priority user group, you must be a member of the *Insider Risk Management* or *Insider Risk Management Admins* role group. > [!IMPORTANT] > Deleting a priority user group will remove it from any active policy to which it is assigned. If you delete a priority user group that is assigned to an active policy, the policy will not contain any in-scope users and will effectively be idle and will not create alerts. The following Power Automate templates are provided to customers to support proc To create a Power Automate flow from a recommended insider risk management template, you'll use the settings controls in the **Insider risk management** solution in the Microsoft Purview compliance portal or the **Manage Power Automate flows** option from the **Automate** control when working directly in the **Cases** or **Users dashboards**. -To create a Power Automate flow in the settings area, you must be a member of the *Insider Risk Management* or *Insider Risk Management Admin* role group. To create a Power Automate flow with the **Manage Power Automate flows** option, you must be a member of at least one insider risk management role group. +To create a Power Automate flow in the settings area, you must be a member of the *Insider Risk Management* or *Insider Risk Management Admins* role group. To create a Power Automate flow with the **Manage Power Automate flows** option, you must be a member of at least one insider risk management role group. Complete the following steps to create a Power Automate flow from a recommended insider risk management template: Complete the following steps to create a custom Power Automate template for insi By default, Power Automate flows created by a user are only available to that user. For other insider risk management users to have access and use a flow, the flow must be shared by the flow creator. To share a flow, you'll use the settings controls in the **Insider risk management solution** in the Microsoft Purview compliance portal or the **Manage Power Automate flows** option from the Automate control when working directly in the **Cases** or **Users dashboard** pages. Once you've shared a flow, everyone who it has been shared with can access the flow in the **Automate** control dropdown in the **Case** and **User dashboards**. -To share a Power Automate flow in the settings area, you must be a member of the *Insider Risk Management* or *Insider Risk Management Admin* role group. To share a Power Automate flow with the **Manage Power Automate flows** option, you must be a member of at least one insider risk management role group. +To share a Power Automate flow in the settings area, you must be a member of the *Insider Risk Management* or *Insider Risk Management Admins* role group. To share a Power Automate flow with the **Manage Power Automate flows** option, you must be a member of at least one insider risk management role group. Complete the following steps to share a Power Automate flow: Complete the following steps to share a Power Automate flow: To edit a flow, you'll use the settings controls in the **Insider risk management** solution in the Microsoft Purview compliance portal or the **Manage Power Automate flows** option from the **Automate** control when working directly in the **Cases** or **Users dashboards**. -To edit a Power Automate flow in the settings area, you must be a member of the *Insider Risk Management* or *Insider Risk Management Admin* role group. To edit a Power Automate flow with the **Manage Power Automate flows** option, you must be a member of at least one insider risk management role group. +To edit a Power Automate flow in the settings area, you must be a member of the *Insider Risk Management* or *Insider Risk Management Admins* role group. To edit a Power Automate flow with the **Manage Power Automate flows** option, you must be a member of at least one insider risk management role group. Complete the following steps to edit a Power Automate flow: Complete the following steps to edit a Power Automate flow: To delete a flow, you'll use the settings controls in the **Insider risk management** solution in the Microsoft Purview compliance portal or the **Manage Power Automate flows** option from the **Automate** control when working directly in the **Cases** or **Users dashboards**. When a flow is deleted, it's removed as an option for all users. -To delete a Power Automate flow in the settings area, you must be a member of the *Insider Risk Management* or *Insider Risk Management Admin* role group. To delete a Power Automate flow with the **Manage Power Automate flows** option, you must be a member of at least one insider risk management role group. +To delete a Power Automate flow in the settings area, you must be a member of the *Insider Risk Management* or *Insider Risk Management Admins* role group. To delete a Power Automate flow with the **Manage Power Automate flows** option, you must be a member of at least one insider risk management role group. Complete the following steps to delete a Power Automate flow: Analytics insights from scans are based on the same risk management activity sig ### Enable analytics and start your scan -To enable insider risk analytics, you must be a member of the *Insider Risk Management*, *Insider Risk Management Admin*, or *Microsoft 365 Global admin* role group. +To enable insider risk analytics, you must be a member of the *Insider Risk Management*, *Insider Risk Management Admins*, or *Microsoft 365 Global admin* role group. Complete the following steps to enable insider risk analytics: 1. In the [Microsoft Purview compliance portal](https://compliance.microsoft.com), go to **Insider risk management**. Complete the following steps to enable insider risk analytics: ### Viewing analytics insights and creating new policies -After the first analytics scan is complete for your organization, members of the *Insider Risk Management Admin* role group will automatically receive an email notification and can view the initial insights and recommendations for potentially risky activities by your users. Daily scans continue unless you turn off analytics for your organization. Email notifications to admins are provided for each of the three in-scope categories for analytics (data leaks, theft, and exfiltration) after the first instance of potentially risky activity in your organization. Email notifications aren't sent to admins for follow-up risk management activity detection resulting from the daily scans. If analytics in **Insider risk management** > **Settings** > **Analytics** are disabled and then re-enabled in your organization, automatic email notifications are reset and emails are sent to members of the *Insider Risk Management Admin* role group for new scanning insights. +After the first analytics scan is complete for your organization, members of the *Insider Risk Management Admins* role group will automatically receive an email notification and can view the initial insights and recommendations for potentially risky activities by your users. Daily scans continue unless you turn off analytics for your organization. Email notifications to admins are provided for each of the three in-scope categories for analytics (data leaks, theft, and exfiltration) after the first instance of potentially risky activity in your organization. Email notifications aren't sent to admins for follow-up risk management activity detection resulting from the daily scans. If analytics in **Insider risk management** > **Settings** > **Analytics** are disabled and then re-enabled in your organization, automatic email notifications are reset and emails are sent to members of the *Insider Risk Management Admins* role group for new scanning insights. To view potential risks for your organization, go to the **Overview** tab and select **View results** on the **Insider risk analytics** card. If the scan for your organization isn't complete, you'll see a message that the scan is still active. To display more information for an insight, select **View details** to display t ### Turn off analytics -To turn off insider risk analytics, you must be a member of the *Insider Risk Management*, *Insider Risk Management Admin*, or Microsoft 365 *Global admin* role group. After you disable analytics, analytics insight reports will remain static and not be updated for new risks. +To turn off insider risk analytics, you must be a member of the *Insider Risk Management*, *Insider Risk Management Admins*, or Microsoft 365 *Global admin* role group. After you disable analytics, analytics insight reports will remain static and not be updated for new risks. Complete the following steps to turn off insider risk analytics: Admin notifications automatically send an email notification to selectable insid - Send a daily email when new high severity alerts are generated. Policies are checked every 24 hours for high severity alerts. - Send a weekly email summarizing policies that have unresolved warnings -If you've enabled insider risk management analytics for your organization, members of the *Insider Risk Management Admin* role group automatically receive an email notification for initial analytics insights for data leaks, theft, and exfiltration activities. +If you've enabled insider risk management analytics for your organization, members of the *Insider Risk Management Admins* role group automatically receive an email notification for initial analytics insights for data leaks, theft, and exfiltration activities. If you prefer to disable admin and analytics notifications, complete the following steps: If you prefer to disable admin and analytics notifications, complete the followi Inline alert customization allows you to quickly tune an insider risk management policy directly from the **Alert dashboard** while reviewing the alert. Alerts are generated when a risk management activity meets the thresholds configured in the related policy. To reduce the number of alerts you get from this type of activity, you can change the thresholds or remove the risk management activity from the policy altogether. -You can enable inline alert customization to allow users assigned to the *Insider Risk Management Analysts* and *Insider Risk Management Investigators* role groups to edit policy thresholds and to disable specific indicators. If inline alert customization isn't enabled, only users assigned to the *Insider Risk Management Admin* or *Insider Risk Management* role groups can edit these policy conditions. Inline alert customization is supported for alerts regardless of the current alert status, allowing analysts and investigators to update policies for *Dismissed* and *Resolved* alerts if needed. +You can enable inline alert customization to allow users assigned to the *Insider Risk Management Analysts* and *Insider Risk Management Investigators* role groups to edit policy thresholds and to disable specific indicators. If inline alert customization isn't enabled, only users assigned to the *Insider Risk Management Admins* or *Insider Risk Management* role groups can edit these policy conditions. Inline alert customization is supported for alerts regardless of the current alert status, allowing analysts and investigators to update policies for *Dismissed* and *Resolved* alerts if needed. Complete the following steps to enable inline alert customization: |
| compliance | Sensitivity Labels Aip | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/sensitivity-labels-aip.md | Independently from labeling, you can continue to use the [AIPService](/powershel ## Benefits of using built-in labeling for Office apps vs. the AIP add-in -The AIP client is in [maintenance mode](https://techcommunity.microsoft.com/t5/security-compliance-and-identity/announcing-aip-unified-labeling-client-maintenance-mode-and/ba-p/3043613) and we don't recommend you use the AIP add-in for Office apps for the following reasons: +The AIP add-in component from the AIP client is in [maintenance mode](https://techcommunity.microsoft.com/t5/security-compliance-and-identity/azure-information-protection-and-the-information-protection/ba-p/3671070) and we don't recommend you use this add-in for Office apps for the following reasons: - No new labeling features will be supported. - Add-ins are less stable because they can conflict with other add-ins that can result in Office apps hanging, crashing, or automatically disabling the add-in. To keep informed when new labeling capabilities become available for built-in la For the latest Office apps, the AIP add-in is disabled by default, so there's nothing for you to configure: - Currently rolling out to [Current Channel (Preview)](https://office.com/insider)-- **Current Channel** and **Monthly Enterprise Channel**: Version 2211+ (not yet released)-- **Semi-Annual Channel**: Version 2301+ (not yet released)+- **Current Channel** and **Monthly Enterprise Channel**: Not before version 2211+ (not yet released) +- **Semi-Annual Channel**: Not before version 2301+ (not yet released) -If you have one of these versions, and need to use the AIP add-in rather than built-in labeling, you have to [configure a new setting to override the default](#how-to-configure-newer-versions-of-office-to-enable-the-aip-add-in). +If you have a version that disabled the AIP add-in by default, and you need to use the AIP add-in rather than built-in labeling, you must [configure a new setting to override the default](#how-to-configure-newer-versions-of-office-to-enable-the-aip-add-in). > [!IMPORTANT]-> If youΓÇÖve previously used the AIP add-in as the default labeling client in Office apps and use Office versions listed in this section, the AIP add-in is automatically disabled and replaced by built-in labeling. +> If youΓÇÖve previously used the AIP add-in as the default labeling client in Office apps and use Office versions identified in this section, the AIP add-in could be automatically disabled and replaced by built-in labeling. To disable the AIP add-in for older versions, see the next section. |
| compliance | Sensitivity Labels Office Apps | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/sensitivity-labels-office-apps.md | Use the information in this article to help you successfully manage sensitivity To use sensitivity labels that are built into Office desktop apps for Windows and Mac, you must use a subscription edition of Office. This labeling client doesn't support standalone editions of Office, sometimes called "Office Perpetual". -The [Azure Information Protection (AIP) unified labeling client](/azure/information-protection/rms-client/aip-clientv2) is now in [maintenance mode](https://techcommunity.microsoft.com/t5/security-compliance-and-identity/announcing-aip-unified-labeling-client-maintenance-mode-and/ba-p/3043613). If you currently use this client for labeling in Office apps, we recommend you move to built-in labeling. For more information, see [Migrate the Azure Information Protection (AIP) add-in to built-in labeling for Office apps](sensitivity-labels-aip.md). +The Azure Information Protection (AIP) add-in component from the [Azure Information Protection unified labeling client](/azure/information-protection/rms-client/aip-clientv2) is now in [maintenance mode](https://techcommunity.microsoft.com/t5/security-compliance-and-identity/azure-information-protection-and-the-information-protection/ba-p/3671070). If you currently use this add-in for labeling in Office apps, we recommend you move to built-in labeling. For more information, see [Migrate the Azure Information Protection (AIP) add-in to built-in labeling for Office apps](sensitivity-labels-aip.md). ## Support for sensitivity label capabilities in apps The numbers listed are the minimum Office application versions required for each |[Apply a sensitivity label to content automatically](apply-sensitivity-label-automatically.md) <br /> - Using sensitive info types | Current Channel: 2009+ <br /><br> Monthly Enterprise Channel: 2009+ <br /><br> Semi-Annual Enterprise Channel: 2102+ | 16.44+ <sup>\*</sup> | Under review | Under review | Yes | |[Apply a sensitivity label to content automatically](apply-sensitivity-label-automatically.md) <br /> - Using trainable classifiers | Current Channel: 2105+ <br /><br> Monthly Enterprise Channel: 2105+ <br /><br> Semi-Annual Enterprise Channel: 2108+ | 16.49+ | Under review | Under review | Yes | |[Different settings for default label and mandatory labeling](#outlook-specific-options-for-default-label-and-mandatory-labeling) | Current Channel: 2105+ <br /><br> Monthly Enterprise Channel: 2105+ <br /><br> Semi-Annual Enterprise Channel: 2108+ | 16.43+ <sup>\*</sup> | 4.2111+ | 4.2111+ | Yes |-|[PDF support](#pdf-support) | Preview: Rolling out to [Beta Channel](https://office.com/insider)| Under review | Under review | Under review | Under review | +|[PDF support](#pdf-support) | Current Channel: 2205+ <br /><br> Monthly Enterprise Channel: 2205+ <br /><br> Semi-Annual Enterprise Channel: Under review| Under review | Under review | Under review | Under review | |[Apply S/MIME protection](#configure-a-label-to-apply-smime-protection-in-outlook) | Preview: [Beta Channel](https://office.com/insider) | 16.61+ <sup>\*</sup> | 4.2226+ | 4.2203+ | Under review | |[Sensitivity bar](#sensitivity-bar) and [display label color](#label-colors) | Under review | Under review | Under review | Under review | Under review | This action is logged with the **Renamed file** audit event from the [File and p When the PDF is created, it inherits the label with any content markings and encryption. Encrypted PDFs can be opened with Microsoft Edge on Windows or Mac. For more information, and alternative readers, see [Which PDF readers are supported for protected PDFs?](/azure/information-protection/rms-client/protected-pdf-readers#viewing-protected-pdfs-in-microsoft-edge-on-windows-or-mac) -Outlook doesn't currently support PDF attachments inheriting encryption from a labeled message. However, Outlook now does support warning or blocking users from printing to PDF, as described next. +Outlook doesn't currently support PDF attachments inheriting encryption from a labeled message. However, Outlook does support warning or blocking users from printing to PDF, as described next. PDF scenarios not supported: |
| compliance | Sensitivity Labels Sharepoint Onedrive Files | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/sensitivity-labels-sharepoint-onedrive-files.md | Uploading a labeled document, and then extracting and displaying that sensitivit - If an admin changes settings for a published label that's already applied to files downloaded to users' sync client, users might be unable to save changes they make to the file in their OneDrive Sync folder. This scenario applies to files that are labeled with encryption, and also when the label change is from a label that didn't apply encryption to a label that does apply encryption. Users see a [red circle with a white cross icon error](https://support.office.com/article/what-do-the-onedrive-icons-mean-11143026-8000-44f8-aaa9-67c985aa49b3), and they are asked to save new changes as a separate copy. Instead, they can close and reopen the file, or use Office for the web. +- Sensitivity labels that are configured for [automatic labeling](apply-sensitivity-label-automatically.md#how-to-configure-auto-labeling-for-office-apps) are supported for Office on the web when the label settings for conditions are for sensitive information types only. Automatic labeling isn't supported for Office on the web when the conditions include trainable classifiers. + - Users can experience save problems after going offline or into a sleep mode when instead of using Office for the web, they use the desktop and mobile apps for Word, Excel, or PowerPoint. For these users, when they resume their Office app session and try to save changes, they see an upload failure message with an option to save a copy instead of saving the original file. - Documents that have been encrypted in the following ways can't be opened in Office for the web: |
| compliance | Sensitivity Labels | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/sensitivity-labels.md | Similarly for users in the legal department, who are assigned the third policy w ## Sensitivity labels and Azure Information Protection -The sensitivity labels that are built into Microsoft 365 Apps on Windows, macOS, iOS, and Android look and behave very similarly across these devices to provide users with a consistent labeling experience. However, on Windows computers, you can also use the [Azure Information Protection (AIP) client](/azure/information-protection/rms-client/aip-clientv2). This client is now in [maintenance mode](https://techcommunity.microsoft.com/t5/security-compliance-and-identity/announcing-aip-unified-labeling-client-maintenance-mode-and/ba-p/3043613) and when installed, is no longer the default labeling client for the latest Office apps. +The sensitivity labels that are built into Microsoft 365 Apps on Windows, macOS, iOS, and Android look and behave very similarly across these devices to provide users with a consistent labeling experience. However, on Windows computers, you can also use the [Azure Information Protection (AIP) client](/azure/information-protection/rms-client/aip-clientv2). The AIP Office add-in component from this client is now in [maintenance mode](https://techcommunity.microsoft.com/t5/security-compliance-and-identity/azure-information-protection-and-the-information-protection/ba-p/3671070) and when installed, is no longer the default labeling client for the latest Office apps. -If you're using the AIP client for labeling in Office apps, we recommend you move to built-in labeling. For more information, see [Migrate the Azure Information Protection (AIP) add-in to built-in labeling for Office apps](sensitivity-labels-aip.md). +If you're using the AIP add-in for labeling in Office apps, we recommend you move to built-in labeling. For more information, see [Migrate the Azure Information Protection (AIP) add-in to built-in labeling for Office apps](sensitivity-labels-aip.md). ### Azure Information Protection labels |
| frontline | Bookings Virtual Visits | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/bookings-virtual-visits.md | description: Learn how to schedule, manage, and conduct virtual appointments usi appliesto: - Microsoft Teams - Microsoft 365 for frontline workers Last updated : 10/28/2022 # Virtual appointments with Microsoft Teams and the Bookings app |
| frontline | Browser Join | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/browser-join.md | description: Learn about the join experience for Teams virtual appointments on b appliesto: - Microsoft Teams - Microsoft 365 for frontline workers Last updated : 10/28/2022 # Manage the join experience for Teams virtual appointments on browsers |
| frontline | Collab Features Apps Toolkit | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/collab-features-apps-toolkit.md | description: Resources to help you train your frontline workers on communication appliesto: - Microsoft Teams - Microsoft 365 for frontline workers Last updated : 10/28/2022 # Help your frontline workers use collaboration apps and features |
| frontline | Deploy Teams At Scale | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/deploy-teams-at-scale.md | |
| frontline | Ehr Admin Cerner | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/ehr-admin-cerner.md | appliesto: - Microsoft Teams - Microsoft 365 for frontline workers -description: Learn how to integrate the Teams EHR connector to enable healthcare providers in your organization to conduct virtual appointments with patients or other providers in Teams directly from the Cerner EHR system. +description: Learn how to integrate the Teams EHR connector to enable healthcare providers in your organization to conduct virtual appointments with patients or other providers in Teams directly from the Cerner EHR system. Last updated : 09/27/2022 # Virtual appointments with Teams - Integration into Cerner EHR |
| frontline | Ehr Admin Epic | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/ehr-admin-epic.md | appliesto: - Microsoft 365 for frontline workers description: Learn how to integrate the Teams EHR connector to enable healthcare providers in your organization to conduct virtual appointments with patients or other providers in Teams directly from the Epic EHR system. Last updated : 09/27/2022 # Virtual appointments with Teams - Integration into Epic EHR |
| frontline | Ehr Connector Report | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/ehr-connector-report.md | appliesto: - Microsoft 365 for frontline workers description: Learn how to use the Teams EHR connector Virtual Appointments report in the Microsoft Teams admin center to get an overview of EHR-integrated virtual appointment usage in your organization. Last updated : 09/27/2022 # Microsoft Teams EHR connector Virtual Appointments report |
| frontline | Flw Choose Scenarios | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/flw-choose-scenarios.md | |
| frontline | Flw Corp Comms | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/flw-corp-comms.md | searchScope: appliesto: - Microsoft Teams - Microsoft 365 for frontline workers Last updated : 09/27/2022 # Corporate communications with frontline workers |
| frontline | Flw Deploy Overview | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/flw-deploy-overview.md | |
| frontline | Flw Devices | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/flw-devices.md | |
| frontline | Flw Licensing Options | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/flw-licensing-options.md | |
| frontline | Flw Onboarding Training | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/flw-onboarding-training.md | searchScope: appliesto: - Microsoft Teams - Microsoft 365 for frontline workers Last updated : 09/27/2022 # Provide initial and ongoing training to help onboard your frontline workers |
| frontline | Flw Onboarding Wizard | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/flw-onboarding-wizard.md | |
| frontline | Flw Overview | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/flw-overview.md | |
| frontline | Flw Pilot | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/flw-pilot.md | |
| frontline | Flw Scenario Posters | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/flw-scenario-posters.md | |
| frontline | Flw Setup Microsoft 365 | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/flw-setup-microsoft-365.md | |
| frontline | Flw Team Collaboration | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/flw-team-collaboration.md | searchScope: appliesto: - Microsoft Teams - Microsoft 365 for frontline workers Last updated : 09/27/2022 # Frontline team collaboration |
| frontline | Flw Technical Planning Guide Deployment | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/flw-technical-planning-guide-deployment.md | |
| frontline | Flw Trial | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/flw-trial.md | |
| frontline | Flw Wellbeing Engagement | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/flw-wellbeing-engagement.md | searchScope: appliesto: - Microsoft Teams - Microsoft 365 for frontline workers Last updated : 09/27/2022 # Engage your frontline workers and focus on wellbeing |
| frontline | Get Up And Running | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/get-up-and-running.md | |
| frontline | Hc Delegates | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/hc-delegates.md | appliesto: description: Learn how a user with Away status or Do Not Disturb status can explicitly set another user as a delegate in their Microsoft Teams status message. Last updated : 11/03/2022 # Use a Teams status message to assign a delegate |
| frontline | Manage Shift Based Access Flw | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/manage-shift-based-access-flw.md | |
| frontline | Messaging Policies Hc | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/messaging-policies-hc.md | appliesto: description: Learn how to customize a Secure Messaging policy for Microsoft Teams that can include read receipts and priority notifications. Last updated : 10/28/2022 # Secure Messaging for healthcare organizations |
| frontline | Pin Teams Apps Based On License | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/pin-teams-apps-based-on-license.md | -Teams pins apps based on license to give your frontline workers an out-of-the-box experience in Teams that's tailored to their needs. +Teams pins apps based on license to give your frontline workers an out-of-the-box experience in Teams that's tailored to their needs. With the tailored frontline app experience, your frontline workers get the most relevant apps in Teams without any action needed from the admin. |
| frontline | Schedule Owner For Shift Management | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/schedule-owner-for-shift-management.md | appliesto: - Microsoft Teams - Microsoft 365 for frontline workers Last updated : 10/28/2022 # Schedule Owner for shift management |
| frontline | Shifts Connector Blue Yonder Admin Center Manage | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/shifts-connector-blue-yonder-admin-center-manage.md | |
| frontline | Shifts Connector Blue Yonder Known Issues | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/shifts-connector-blue-yonder-known-issues.md | |
| frontline | Shifts Connector Blue Yonder Powershell Setup | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/shifts-connector-blue-yonder-powershell-setup.md | |
| frontline | Shifts Connector Powershell Manage | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/shifts-connector-powershell-manage.md | |
| frontline | Shifts Connector Ukg Admin Center Manage | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/shifts-connector-ukg-admin-center-manage.md | |
| frontline | Shifts Connector Ukg Known Issues | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/shifts-connector-ukg-known-issues.md | |
| frontline | Shifts Connector Ukg Powershell Manage | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/shifts-connector-ukg-powershell-manage.md | |
| frontline | Shifts Connector Ukg Powershell Setup | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/shifts-connector-ukg-powershell-setup.md | |
| frontline | Shifts Connector Wizard Ukg | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/shifts-connector-wizard-ukg.md | |
| frontline | Shifts Connector Wizard | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/shifts-connector-wizard.md | |
| frontline | Shifts Connectors | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/shifts-connectors.md | |
| frontline | Shifts For Teams Landing Page | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/shifts-for-teams-landing-page.md | appliesto: - Microsoft Teams - Microsoft 365 for frontline workers Last updated : 09/29/2022 # Shifts for frontline workers |
| frontline | Shifts Toolkit | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/shifts-toolkit.md | description: Resources to help train your frontline team in using Shifts to acce appliesto: - Microsoft Teams - Microsoft 365 for frontline workers Last updated : 10/28/2022 # Help your frontline workers track time and attendance |
| frontline | Simplify Business Processes | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/simplify-business-processes.md | searchScope: appliesto: - Microsoft Teams - Microsoft 365 for frontline workers Last updated : 09/29/2022 # Simplify business processes for frontline teams You can use Teams apps, Power Apps, and Power BI to simplify business processes > [!VIDEO https://www.microsoft.com/videoplayer/embed/RWRzfc] - > [!NOTE] > Additional capabilities for [financial services](/industry/financial-services), [healthcare](/industry/healthcare), [nonprofit](/industry/nonprofit), and [retail](/industry/retail) environments are available with the Microsoft industry clouds, which include capabilities from Dynamics 365 and Microsoft Azure as well as the Microsoft 365 features. |
| frontline | Switch From Enterprise To Frontline | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/switch-from-enterprise-to-frontline.md | |
| frontline | Teams For Financial Services | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/teams-for-financial-services.md | searchScope: appliesto: - Microsoft Teams - Microsoft 365 for frontline workers Last updated : 09/27/2022 # Get started with Microsoft 365 for Financial Services |
| frontline | Teams For Manufacturing | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/teams-for-manufacturing.md | searchScope: appliesto: - Microsoft Teams - Microsoft 365 for frontline workers Last updated : 09/27/2022 # Get started with Microsoft 365 for Manufacturing |
| frontline | Teams For Retail Landing Page | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/teams-for-retail-landing-page.md | searchScope: appliesto: - Microsoft Teams - Microsoft 365 for frontline workers Last updated : 09/27/2022 # Get started with Microsoft 365 for retail organizations |
| frontline | Teams In Hc | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/teams-in-hc.md | description: Learn about the telemedicine features in Microsoft 365 and Microsof - seo-marvel-apr2020 - seo-marvel-jun2020 Last updated : 10/28/2022 # Get started with Microsoft 365 for healthcare organizations |
| frontline | Virtual Appointments Toolkit | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/virtual-appointments-toolkit.md | description: Customizable resources and infographics you can add to your website appliesto: - Microsoft Teams - Microsoft 365 for frontline workers Last updated : 11/02/2022 # Help your clients and customers use virtual appointments scheduled with Bookings |
| frontline | Virtual Appointments | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/virtual-appointments.md | f1.keywords: appliesto: - Microsoft Teams - Microsoft 365 for frontline workers Last updated : 10/28/2022 # Virtual appointments with Microsoft Teams |
| frontline | Virtual Visits Usage Report | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/frontline/virtual-visits-usage-report.md | appliesto: - Microsoft Teams - Microsoft 365 for frontline workers Last updated : 10/28/2022 # Microsoft Teams Virtual Visits usage report |
| lighthouse | M365 Lighthouse Known Issues | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/lighthouse/m365-lighthouse-known-issues.md | +- M365-Lighthouse search.appverid: MET150 description: "For Managed Service Providers (MSPs) using Microsoft 365 Lighthouse, see a list of known issues for Lighthouse by feature area." |
| lighthouse | M365 Lighthouse Requirements | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/lighthouse/m365-lighthouse-requirements.md | In addition, each MSP customer tenant must qualify for Lighthouse by meeting the - Must have delegated access set up for the Managed Service Provider (MSP) to be able to manage the customer tenant* - Must have at least one Microsoft 365 Business Premium, Microsoft 365 E3, Microsoft 365 E5, Windows 365 Business, or Microsoft Defender for Business license - Must have no more than 2500 licensed users+- Must reside in the same geographic region as the partner organization that manages them \* Either Granular Delegated Admin Privileges (GDAP or a Delegated Admin Privileges (DAP) relationship is required to onboard customers to Lighthouse. An indirect reseller relationship is no longer required to onboard to Lighthouse. If DAP and GDAP coexist in a customer tenant, GDAP permissions take precedence for MSP technicians in GDAP-enabled security groups. |
| security | TOC | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/TOC.md | ### [Device discovery]() #### [Device discovery overview](device-discovery.md) #### [Configure device discovery](configure-device-discovery.md) -#### [Microsoft Defender for IoT integration](enable-microsoft-defender-for-iot-integration.md) #### [Enable Corelight data integration](corelight-integration.md) #### [Device discovery FAQ](device-discovery-faq.md) ### [Experts on Demand](experts-on-demand.md) +## [Enterprise IoT security]() ++### [Securing IoT devices in the enterprise]() +### [Onboard an Enterprise IoT plan on your Azure subscription]() +### [Onboard Enterprise IoT sensors]() +### [Manage Enterprise IoT plans]() + ## Reference ### [Understand threat intelligence concepts](threat-indicator-concepts.md) ### [Configure integration with other Microsoft solutions]() |
| security | Android Configure | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/android-configure.md | Network protection in Microsoft Defender for endpoint is disabled by default. Ad 1. Provide a name and description to uniquely identify the policy. Select **'Android Enterprise'** as the platform and **'Personally-owned work profile only'** as the profile type and **'Microsoft Defender'** as the Targeted app. > [!div class="mx-imgBorder"] > -1. In Settings page, select **'Use configuration designer'** and add **'Enable Network Protection in Microsoft Defender'** as the key and value as **'1'** to enable Network Protection. (Network protection is enabled by default) +1. In Settings page, select **'Use configuration designer'** and add **'Enable Network Protection in Microsoft Defender'** as the key and value as **'1'** to enable Network Protection. (Network protection is disabled by default) > [!div class="mx-imgBorder"] >  |
| security | Configure Server Endpoints | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/configure-server-endpoints.md | ms.pagetype: security ms.localizationpriority: medium Previously updated : 09/22/2022 Last updated : 11/10/2022 audience: ITPro Data collected by Defender for Endpoint is stored in the geo-location of the ten > - If you use Defender for Endpoint before using Microsoft Defender for Cloud, your data will be stored in the location you specified when you created your tenant even if you integrate with Microsoft Defender for Cloud at a later time. > - Once configured, you cannot change the location where your data is stored. If you need to move your data to another location, you need to contact Microsoft Support to reset the tenant. > - Server endpoint monitoring utilizing this integration has been disabled for Office 365 GCC customers.+> - Previously, the use of the Microsoft Monitoring Agent (MMA) on Windows Server 2016 and previous versions of Windows Server allowed for the OMS / Log Analytics gateway to provide connectivity to Defender cloud services. The new solution, like Microsoft Defender for Endpoint on Windows Server 2019, Windows Server 2022, and Windows 10, doesn't support this gateway. > - Linux servers onboarded through Microsoft Defender for Cloud will have their initial configuration set to run Defender Antivirus in [passive mode](/defender-endpoint/microsoft-defender-antivirus-compatibility#microsoft-defender-antivirus-and-non-microsoft-antivirusantimalware-solutions). **Windows Server 2012 R2 and Windows Server 2016**: Data collected by Defender for Endpoint is stored in the geo-location of the ten - Download the onboarding package - Follow the onboarding steps for the corresponding tool ->[!IMPORTANT] ->To be eligible to purchase Microsoft Defender for Endpoint Server SKU, you already must have purchased a combined minimum of any of the following: Windows E5/A5, Microsoft 365 E5/A5, or Microsoft 365 E5 Security subscription licenses. +> [!IMPORTANT] +> To be eligible to purchase Microsoft Defender for Endpoint Server SKU, you already must have purchased a combined minimum of any of the following: Windows E5/A5, Microsoft 365 E5/A5, or Microsoft 365 E5 Security subscription licenses. ## Windows Server 2012 R2 and Windows Server 2016 The installer package will check if the following components have already been i #### Prerequisites for Windows Server 2016 +It's recommended to install the latest available SSU and LCU on the server. + - The Servicing Stack Update (SSU) from September 14, 2021 or later must be installed.-- The Latest Cumulative Update (LCU) from September 20, 2018 or later must be installed. It's recommended to install the latest available SSU and LCU on the server.+- The Latest Cumulative Update (LCU) from September 20, 2018 or later must be installed. - Enable the Microsoft Defender Antivirus feature and ensure it's up to date. For more information on enabling Defender Antivirus on Windows Server, see [Re-enable Defender Antivirus on Windows Server if it was disabled](enable-update-mdav-to-latest-ws.md#re-enable-microsoft-defender-antivirus-on-windows-server-if-it-was-disabled) and [Re-enable Defender Antivirus on Windows Server if it was uninstalled](enable-update-mdav-to-latest-ws.md#re-enable-microsoft-defender-antivirus-on-windows-server-if-it-was-uninstalled). - Download and install the latest platform version using Windows Update. Alternatively, download the update package manually from the [Microsoft Update Catalog](https://www.catalog.update.microsoft.com/Search.aspx?q=KB4052623) or from [MMPC](https://go.microsoft.com/fwlink/?linkid=870379&arch=x64). Follow these steps to download the packages: 5. Install the installation package using any of the options to install Microsoft Defender Antivirus. The installation requires administrative permissions. +> [!IMPORTANT] +> +> - A local onboarding script is suitable for a proof of concept but should not be used for production deployment. For a production deployment, we recommend using Group Policy, or Microsoft Endpoint Configuration Manager. + ### STEP 2: Apply the installation and onboarding package In this step, you'll install the prevention and detection components required before onboarding your device to the Microsoft Defender for Endpoint cloud environment, to prepare the machine for onboarding. Ensure all [prerequisites](#prerequisites) have been met. The following steps are only applicable if you're using a third-party anti-malwa :::image type="content" source="images/atp-verify-passive-mode.png" alt-text="The passive mode verification result" lightbox="images/atp-verify-passive-mode.png"::: -> [!IMPORTANT] -> -> - A local script is suitable for a proof of concept but should not be used for production deployment. For a production deployment, we recommend using Group Policy, or Microsoft Endpoint Configuration Manager. - #### Known issues and limitations in the new, unified solution package for Windows Server 2012 R2 and 2016 -Always download the latest installer package before performing a new installation. After installation, ensure to regularly update using component updates described in the section [Update packages for Microsoft Defender for Endpoint on Windows Server 2012 R2 and 2016](#update-packages-for-microsoft-defender-for-endpoint-on-windows-server-2012-r2-and-2016). The following specifics apply to the new unified solution package for Windows Server 2012 R2 and 2016: +> [!IMPORTANT] +> +> - Always download the latest installer package from the Microsoft 365 Defender portal ([https://security.microsoft.com](https://security.microsoft.com)) before performing a new installation and ensure prerequisites have been met. After installation, ensure to regularly update using component updates described in the section [Update packages for Microsoft Defender for Endpoint on Windows Server 2012 R2 and 2016](#update-packages-for-microsoft-defender-for-endpoint-on-windows-server-2012-r2-and-2016). - An operating system update can introduce an installation issue on machines with slower disks due to a timeout with service installation. Installation fails with the message "Could not find c:\program files\windows defender\mpasdesc.dll, - 310 WinDefend". Use the latest installation package, and the latest [install.ps1](https://github.com/microsoft/mdefordownlevelserver) script to help clear the failed installation if necessary.-- Ensure connectivity requirements as specified in [Enable access to Microsoft Defender for Endpoint service URLs in the proxy server](/microsoft-365/security/defender-endpoint/configure-proxy-internet?enable-access-to-microsoft-defender-for-endpoint-service-urls-in-the-proxy-server) are met. They're equivalent to those requirements for Windows Server 2019.-- We've identified an issue with Windows Server 2012 R2 connectivity to cloud when static TelemetryProxyServer is used **and** the certificate revocation list (CRL) URLs aren't reachable from the SYSTEM account context. The immediate mitigation is to either use an alternative proxy option ("system-wide") that provides such connectivity, or configure the same proxy via the WinInet setting on the SYSTEM account context.-Alternatively, use the instructions provided at [Workaround for a known issue with TelemetryProxyServer on disconnected machines](#workaround-for-a-known-issue-with-telemetryproxyserver-on-disconnected-machines) to install a certificate as a workaround. -- Previously, the use of the Microsoft Monitoring Agent (MMA) on Windows Server 2016 and below allowed for the OMS / Log Analytics gateway to provide connectivity to Defender cloud services. The new solution, like Microsoft Defender for Endpoint on Windows Server 2019, Windows Server 2022, and Windows 10, doesn't support this gateway.-- On Windows Server 2016, verify that Microsoft Defender Antivirus is installed, is active and up to date. You can download and install the latest platform version using Windows Update. Alternatively, download the update package manually from the [Microsoft Update Catalog](https://www.catalog.update.microsoft.com/Search.aspx?q=KB4052623) or from [MMPC](https://go.microsoft.com/fwlink/?linkid=870379&arch=x64).+- We've identified an issue with Windows Server 2012 R2 connectivity to cloud when static TelemetryProxyServer is used **and** the certificate revocation list (CRL) URLs aren't reachable from the SYSTEM account context. Ensure the EDR sensor is updated to version 10.8210.* or later (using [KB5005292](https://support.microsoft.com/en-us/topic/microsoft-defender-for-endpoint-update-for-edr-sensor-f8f69773-f17f-420f-91f4-a8e5167284ac)) to resolve the issue. Alternatively, use an different proxy option ("system-wide") that provides such connectivity, or configure the same proxy via the WinInet setting on the SYSTEM account context. - On Windows Server 2012 R2, there's no user interface for Microsoft Defender Antivirus. In addition, the user interface on Windows Server 2016 only allows for basic operations. To perform operations on a device locally, refer to [Manage Microsoft Defender for Endpoint with PowerShell, WMI, and MPCmdRun.exe](/microsoft-365/security/defender-endpoint/manage-mde-post-migration-other-tools). As a result, features that specifically rely on user interaction, such as where the user is prompted to make a decision or perform a specific task, may not work as expected. It's recommended to disable or not enable the user interface nor require user interaction on any managed server as it may impact protection capability.-- Not all Attack Surface Reduction rules are available on all operating systems. See [Attack Surface Reduction (ASR) rules](/microsoft-365/security/defender-endpoint/attack-surface-reduction-rules).-- To enable [Network Protection](/microsoft-365/security/defender-endpoint/network-protection), more configurations are required:- - `Set-MpPreference -EnableNetworkProtection Enabled` - - `Set-MpPreference -AllowNetworkProtectionOnWinServer 1` - - `Set-MpPreference -AllowNetworkProtectionDownLevel 1` - - `Set-MpPreference -AllowDatagramProcessingOnWinServer 1` -- In addition, on machines with a high volume of network traffic, performance testing in your environment is highly recommended before enabling this capability broadly. You may need to account for extra resource consumption. -- Operating system upgrades aren't supported. Offboard then uninstall before upgrading.+- Not all Attack Surface Reduction rules are applicable to all operating systems. See [Attack Surface Reduction (ASR) rules](/microsoft-365/security/defender-endpoint/attack-surface-reduction-rules). +- Operating system upgrades aren't supported. Offboard then uninstall before upgrading. The installer package can only be used to upgrade installations that have not yet been updated with new antimalware platform or EDR sensor update packages. - Automatic exclusions for **server roles** aren't supported on Windows Server 2012 R2; however, built-in exclusions for operating system files are. For more information about adding exclusions, see [Virus scanning recommendations for Enterprise computers that are running currently supported versions of Windows](https://support.microsoft.com/topic/virus-scanning-recommendations-for-enterprise-computers-that-are-running-currently-supported-versions-of-windows-kb822158-c067a732-f24a-9079-d240-3733e39b40bc).-- On machines that have been upgraded from the previous, MMA-based solution and the EDR sensor is a (preview) version older than 10.8047.22439.1056, uninstalling and reverting back to the MMA-based solution may lead to crashes. If you are on such a preview version, update using KB5005292.-- To deploy and onboard the new solution using Microsoft Endpoint Configuration Manager (MECM) on versions 2107 and 2203, this requires creating a package. For more information on how to deploy programs and scripts in Configuration Manager, see [Packages and programs in Configuration Manager](/configmgr/apps/deploy-use/packages-and-programs). You can also use MECM 2107, 2203 to migrate from the MMA-based version. For more information, see [Migrating servers from Microsoft Monitoring Agent to the unified solution](application-deployment-via-mecm.md).-- MECM 2107 with the hotfix rollup or later is required to support policy configuration management using the Endpoint Protection node. -- Microsoft Endpoint Configuration Manager 2207 or later supports [automated installation and onboarding](/mem/configmgr/protect/deploy-use/defender-advanced-threat-protection#bkmk_2207)--#### Workaround for a known issue with TelemetryProxyServer on disconnected machines --Problem description: -When using the TelemetryProxyServer setting to specify a proxy to be used by the EDR component of Microsoft Defender for Endpoint, on machines that have no other way to access the Certificate Revocation List (CRL) URL, a missing intermediate certificate will cause the EDR sensor to not successfully connect to the cloud service. --Affected scenario: --Microsoft Defender for Endpoint with Sense version number 10.8048.22439.1065 or earlier preview versions running on Windows Server 2012 R2--Using the TelemetryProxyServer proxy configuration; other methods aren't affected--Workaround: -1. Ensure the machine is running Sense version 10.8048.22439.1065 or higher by either installing using the latest package available from the onboarding page, or by applying KB5005292. -2. Download and unzip the certificate from https://github.com/microsoft/mdefordownlevelserver/blob/main/InterCA.zip -3. Import the certificate to the Local Computer trusted "Intermediate Certification Authorities" store. -You can use the PowerShell command: -Import-Certificate -FilePath .\InterCA.cer -CertStoreLocation Cert:\LocalMachine\Ca +- To automatically deploy and onboard the new solution using Microsoft Endpoint Configuration Manager (MECM) you need to be on [version 2207 or later](/mem/configmgr/core/plan-design/changes/whats-new-in-version-2207#improved-microsoft-defender-for-endpoint-mde-onboarding-for-windows-server-2012-r2-and-windows-server-2016). You can still configure and deploy using version 2107 with the hotfix rollup, but this requires additional deployment steps. See [Microsoft Endpoint Configuration Manager migration scenarios](/microsoft-365/security/defender-endpoint/server-migration#microsoft-endpoint-configuration-manager-migration-scenarios) for more information. + ## Windows Server Semi-Annual Enterprise Channel (SAC), Windows Server 2019 and Windows Server 2022 |
| security | Configure Vulnerability Email Notifications | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/configure-vulnerability-email-notifications.md | The email notification includes basic information about the vulnerability event. Create a notification rule to send an email when there are certain exploit or vulnerability events, such as a new public exploit. For each rule, multiple event types can be selected. -1. In the navigation pane, go to **Settings** \> **Endpoints** \> **Email notifications** \> **Vulnerabilities**. +1. Go to [Microsoft 365 Defender](https://go.microsoft.com/fwlink/p/?linkid=2077139) and sign in using an account with the Security administrator or Global administrator role assigned. ++2. In the navigation pane, go to **Settings** \> **Endpoints** \> **Email notifications** \> **Vulnerabilities**. 2. Select **Add notification rule**. |
| security | Deploy Manage Removable Storage Group Policy | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/deploy-manage-removable-storage-group-policy.md | Before you get started with Removable Storage Access Control, you must confirm y - In the **Define device control policy groups** window, specify the network share file path containing the XML groups data. + Take a look at the **Overview** > **Removable storage group**. You can create different group types. Here's one group example XML file for any removable storage and CDROM and Windows portable devices and approved USBs group: [XML file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Group%20Policy/Demo_Groups.xml) + > [!NOTE] > Comments using XML comment notation `<!-- COMMENT -->` can be used in the Rule and Group XML files, but they must be inside the first XML tag, not the first line of the XML file. 4. Create one XML file for access policy rule(s): - Use the properties in removable storage access policy rule(s) to create a XML for each group's removable storage access policy rule, save the XML file to network share, and devlier the setting setting as follows: + Use the properties in removable storage access policy rule(s) to create an XML for each group's removable storage access policy rule, save the XML file to network share, and deliver the setting as follows: - Go to **Computer Configuration** > **Administrative Templates** > **Windows Components** > **Microsoft Defender Antivirus** > **Device Control** > **Define device control policy rules**. Before you get started with Removable Storage Access Control, you must confirm y - In the **Define device control policy rules** window, select **Enabled**, and enter the network share file path containing the XML rules data. + Take a look at the **Overview** -> **Access policy rule**, you can use **Parameters** to set condition for specific Entry. Here's one [example XML file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Group%20Policy/Demo_Policies.xml). + > [!NOTE] > Comments using XML comment notation `<!-- COMMENT -->` can be used in the Rule and Group XML files, but they must be inside the first XML tag, not the first line of the XML file. Before you get started with Removable Storage Access Control, you must confirm y ## Scenarios -Here are some common scenarios to help you familiarize with Microsoft Defender for Endpoint Removable Storage Access Control. Note that in the following samples, 'Default Enforcement' hasn't been used because the 'Default Enforcement' will apply to both the removable storage and the printer. +Here are some common scenarios to help you familiarize with Microsoft Defender for Endpoint Removable Storage Access Control. In the following samples, 'Default Enforcement' hasn't been used because the 'Default Enforcement' will apply to both the removable storage and the printer. ### Scenario 1: Prevent Write and Execute access to all but allow specific approved USBs For this scenario, you need to create two groups - one group for any removable s Combine these two policy rules into [one XML file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Group%20Policy/Scenario%202%20GPO%20Policy%20-%20Audit%20Write%20and%20Execute%20access%20to%20all%20but%20block%20specific%20unapproved%20USBs.xml). See step 4 from the [Deploy using group policy](deploy-manage-removable-storage-group-policy.md#deploy-using-group-policy) section to deploy this configuration. +### Scenario 3: Block read and execute access to specific file extension ++For this scenario, you need to create two groups: one removable storage group for any removable storage and another group for unallowed file extensions. You also need to create one policy - deny read and execute access to any file under the allowed file extension group for defined removable storage group. ++1. Create groups ++ 1. Group 1: Any removable storage, CD/DVD, and Windows portable devices. ++ 2. Group 2: Unallowed file extensions. + + Combine these two groups into [one XML file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Group%20Policy/Block%20Read%20and%20Write%20access%20to%20specific%20file%20_Groups.xml). See step 3 from the [Deploy using group policy](deploy-manage-removable-storage-group-policy.md#deploy-using-group-policy) section to deploy this configuration. +++ > [!TIP] + > Explicily mark the Type attribute on the group as **File** ++ 2. Policy 2: Deny read and execute access to any file under the allowed file extension group for defined removable storage group. ++  + + What does '40' mean in the policy? It's 8 + 32 = 40: ++ - only need to restrict file system level access ++ Although this case only has one policy, make sure put it under PolicyRules [one XML file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Group%20Policy/Block%20Read%20and%20Write%20access%20to%20specific%20file%20_Policy.xml). See step 4 from the [Deploy using group policy](deploy-manage-removable-storage-group-policy.md#deploy-using-group-policy) section to deploy this configuration. |
| security | Deploy Manage Removable Storage Intune | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/deploy-manage-removable-storage-intune.md | Go to Microsoft Endpoint Manager admin center (<https://endpoint.microsoft.com/> You can set the default access (Deny or Allow) for all Device Control features (`RemovableMediaDevices`, `CdRomDevices`, `WpdDevices`, `PrinterDevices`). - To block a specific removable storage class but allow specific media, you can use '`IncludedIdList` a group through `PrimaryId` and `ExcludedIDList` a group through `DeviceId`/`HardwareId`/etc.' For additional details, see [Microsoft Defender for Endpoint Device Control Removable Storage Access Control](device-control-removable-storage-access-control.md). + To block a specific removable storage class but allow specific media, you can use '`IncludedIdList` a group through `PrimaryId` and `ExcludedIDList` a group through `DeviceId`/`HardwareId`/etc.' For more information, see [Microsoft Defender for Endpoint Device Control Removable Storage Access Control](device-control-removable-storage-access-control.md). For example, you can have either a **Deny** or an **Allow** policy for `RemovableMediaDevices`, but not for `CdRomDevices` or `WpdDevices`. You can set **Default Deny** through this policy, then Read/Write/Execute access to `CdRomDevices` or `WpdDevices` will be blocked. If you only want to manage storage, make sure to create an **Allow** policy for your printer; otherwise, this default enforcement will be applied to printers as well. Go to Microsoft Endpoint Manager admin center (<https://endpoint.microsoft.com/> - **Data Type** as **String (XML file)** - **Custom XML** as selected XML file - Here is one group example XML file for any removable storage and CDROM and Windows portable devices: <https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Any%20Removable%20Storage%20and%20CD-DVD%20and%20WPD%20Group.xml> + Take a look at the **Overview** -> **Removable storage group**, you can create different group types. Here's a [group example XML file for any removable storage and CD-ROM and Windows portable devices](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Any%20Removable%20Storage%20and%20CD-DVD%20and%20WPD%20Group.xml). :::image type="content" source="images/any-removable-storage-group.png" alt-text="Screenshot of creating any Removable Storage Group." lightbox="images/any-removable-storage-group.png"::: Go to Microsoft Endpoint Manager admin center (<https://endpoint.microsoft.com/> - **Name** as **Allow Read Activity** - **OMA-URI** as `./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyRules/%7b**[PolicyRule Id]**%7d/RuleData` - **Data Type** as **String (XML file)**- - **Custom XML** as **Allow Read.xml** file + - **Custom XML** as selected XML file - Here is one group example XML file for Allow Read access for each removable storage: <https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Allow%20Read.xml> + Take a look at the **Overview** -> **Access policy rule**, you can use **Parameters** to set condition for specific Entry. Here's a [group example XML file for Allow Read access for each removable storage](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Allow%20Read.xml). :::image type="content" source="images/allow-read-activity.png" alt-text="Screenshot of Allow Read Activity policy" lightbox= "images/allow-read-activity.png"::: For this scenario, you need to create two groups - one group for any removable s :::image type="content" source="media/188234308-4db09787-b14e-446a-b9e0-93c99b08748f.png" alt-text="A screenshot showing removable storage" lightbox= "media/188234308-4db09787-b14e-446a-b9e0-93c99b08748f.png"::: - Here is the [sample file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Any%20Removable%20Storage%20and%20CD-DVD%20and%20WPD%20Group.xml). See step 3 from the [Deploy Removable Storage Access Control](deploy-manage-removable-storage-intune.md#deploy-removable-storage-access-control-by-using-intune-oma-uri) section to deploy the configuration. + Here's the [sample file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Any%20Removable%20Storage%20and%20CD-DVD%20and%20WPD%20Group.xml). See step 3 from the [Deploy Removable Storage Access Control](deploy-manage-removable-storage-intune.md#deploy-removable-storage-access-control-by-using-intune-oma-uri) section to deploy the configuration. 2. Group 2: Approved USBs based on device properties. :::image type="content" source="media/188234372-526d20b3-cfea-4f1d-8d63-b513497ada52.png" alt-text="A screenshot of approved USBs" lightbox= "media/188234372-526d20b3-cfea-4f1d-8d63-b513497ada52.png"::: - Here is the [sample file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Approved%20USBs%20Group.xml). See step 3 from the [Deploy Removable Storage Access Control](deploy-manage-removable-storage-intune.md#deploy-removable-storage-access-control-by-using-intune-oma-uri) section to deploy the configuration. + Here's the [sample file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Approved%20USBs%20Group.xml). See step 3 from the [Deploy Removable Storage Access Control](deploy-manage-removable-storage-intune.md#deploy-removable-storage-access-control-by-using-intune-oma-uri) section to deploy the configuration. > [!TIP] > Replace `&` with `&` in the value in the XML file. For this scenario, you need to create two groups - one group for any removable s :::image type="content" source="media/188243425-c0772ed4-6537-4c6a-9a1d-1dbb48018578.png" alt-text="A screenshot of policy 1" lightbox= "media/188243425-c0772ed4-6537-4c6a-9a1d-1dbb48018578.png"::: - Here is the [sample file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Scenario%201%20Block%20Write%20and%20Execute%20Access%20but%20allow%20approved%20USBs.xml). See step 4 from the [Deploy Removable Storage Access Control](deploy-manage-removable-storage-intune.md#deploy-removable-storage-access-control-by-using-intune-oma-uri) section to deploy the configuration. + Here's the [sample file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Scenario%201%20Block%20Write%20and%20Execute%20Access%20but%20allow%20approved%20USBs.xml). See step 4 from the [Deploy Removable Storage Access Control](deploy-manage-removable-storage-intune.md#deploy-removable-storage-access-control-by-using-intune-oma-uri) section to deploy the configuration. 2. Policy 2: Audit Write and Execute access for allowed USBs. For this scenario, you need to create two groups - one group for any removable s - Write access: disk level 2 + file system level 16 = 18. - Execute: disk level 4 + file system level 32 = 36. - Here is the [sample file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Scenario%201%20Audit%20Write%20and%20Execute%20access%20to%20aproved%20USBs.xml). See step 4 from the [Deploy Removable Storage Access Control](deploy-manage-removable-storage-intune.md#deploy-removable-storage-access-control-by-using-intune-oma-uri) section to deploy the configuration. + Here's the [sample file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Scenario%201%20Audit%20Write%20and%20Execute%20access%20to%20aproved%20USBs.xml). See step 4 from the [Deploy Removable Storage Access Control](deploy-manage-removable-storage-intune.md#deploy-removable-storage-access-control-by-using-intune-oma-uri) section to deploy the configuration. ### Scenario 2: Audit Write and Execute access for all but block specific blocked USBs For this scenario, you need to create two groups - one group for any removable s :::image type="content" source="media/188234308-4db09787-b14e-446a-b9e0-93c99b08748f.png" alt-text="A screenshot of group 1" lightbox="media/188234308-4db09787-b14e-446a-b9e0-93c99b08748f.png"::: - Here is the [sample file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Any%20Removable%20Storage%20and%20CD-DVD%20and%20WPD%20Group.xml). See step 3 from the [Deploy Removable Storage Access Control](deploy-manage-removable-storage-intune.md#deploy-removable-storage-access-control-by-using-intune-oma-uri) section to deploy the configuration. + Here's the [sample file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Any%20Removable%20Storage%20and%20CD-DVD%20and%20WPD%20Group.xml). See step 3 from the [Deploy Removable Storage Access Control](deploy-manage-removable-storage-intune.md#deploy-removable-storage-access-control-by-using-intune-oma-uri) section to deploy the configuration. 2. Group 2: Unapproved USBs based on device properties. :::image type="content" source="media/188243875-0693ebcf-00c3-45bd-afd3-57a79df9dce6.png" alt-text="A screenshot of group 2" lightbox= "media/188243875-0693ebcf-00c3-45bd-afd3-57a79df9dce6.png"::: - Here is the [sample file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Unapproved%20USBs%20Group.xml). See step 3 from the [Deploy Removable Storage Access Control](deploy-manage-removable-storage-intune.md#deploy-removable-storage-access-control-by-using-intune-oma-uri) section to deploy the configuration. + Here's the [sample file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Unapproved%20USBs%20Group.xml). See step 3 from the [Deploy Removable Storage Access Control](deploy-manage-removable-storage-intune.md#deploy-removable-storage-access-control-by-using-intune-oma-uri) section to deploy the configuration. > [!TIP] > Replace `&` with `&` in the value in the XML file. For this scenario, you need to create two groups - one group for any removable s :::image type="content" source="media/188244024-62355ded-353c-4d3a-ba61-4520d48f5a18.png" alt-text="A screenshot of policy for blocking unapproved USBs" lightbox= "media/188244024-62355ded-353c-4d3a-ba61-4520d48f5a18.png"::: - Here is the [sample file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Scenario%202%20Audit%20Write%20and%20Execute%20access%20to%20all%20but%20block%20specific%20unapproved%20USBs.xml). See step 4 from the [Deploy Removable Storage Access Control](deploy-manage-removable-storage-intune.md#deploy-removable-storage-access-control-by-using-intune-oma-uri) section to deploy the configuration. + Here's the [sample file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Scenario%202%20Audit%20Write%20and%20Execute%20access%20to%20all%20but%20block%20specific%20unapproved%20USBs.xml). See step 4 from the [Deploy Removable Storage Access Control](deploy-manage-removable-storage-intune.md#deploy-removable-storage-access-control-by-using-intune-oma-uri) section to deploy the configuration. 2. Policy 2: Audit Write and Execute access for others. For this scenario, you need to create two groups - one group for any removable s - Write access: disk level 2 + file system level 16 = 18. - Execute: disk level 4 + file system level 32 = 36. - Here is the [sample file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Scenario%202%20Audit%20Write%20and%20Execute%20access%20to%20others.xml). See step 4 from the [Deploy Removable Storage Access Control](deploy-manage-removable-storage-intune.md#deploy-removable-storage-access-control-by-using-intune-oma-uri) section to deploy the configuration. + Here's the [sample file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Scenario%202%20Audit%20Write%20and%20Execute%20access%20to%20others.xml). See step 4 from the [Deploy Removable Storage Access Control](deploy-manage-removable-storage-intune.md#deploy-removable-storage-access-control-by-using-intune-oma-uri) section to deploy the configuration. ++### Scenario 3: Block read and execute access to specific file extension ++For this scenario, you need to create two groups - one removable storage group for any removable storage and another group for unallowed file extensions. You also need to create one policy - deny read and execute access to any file under the allowed file extension group for defined removable storage group. ++1. Create groups ++ 1. Group 1: Any removable storage, CD/DVD, and Windows portable devices. ++ :::image type="content" source="media/188234308-4db09787-b14e-446a-b9e0-93c99b08748f.png" alt-text="A screenshot of group 1" lightbox="media/188234308-4db09787-b14e-446a-b9e0-93c99b08748f.png"::: + + Here's the [sample file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Any%20Removable%20Storage%20and%20CD-DVD%20and%20WPD%20Group.xml). See step 3 from the [Deploy Removable Storage Access Control](deploy-manage-removable-storage-intune.md#deploy-removable-storage-access-control-by-using-intune-oma-uri) section to deploy the configuration. ++ 2. Group 2: Unallowed file extensions. + + Here's the [sample file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Unauthorized%20File%20Group.xml). See step 3 from the [Deploy Removable Storage Access Control](deploy-manage-removable-storage-intune.md#deploy-removable-storage-access-control-by-using-intune-oma-uri) section to deploy the configuration. +++ > [!TIP] + > Explicily mark the Type attribute on the group as **File** ++ 2. Policy 2: Deny read and execute access to any file under the allowed file extension group for defined removable storage group. + + What does '40' mean in the policy? It's 8 + 32 = 40: ++ - only need to restrict file system level access + + Here's the [sample file](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/Intune%20OMA-URI/Deny%20Read%20and%20Write%20access%20to%20specific%20files.xml). See step 4 from the [Deploy Removable Storage Access Control](deploy-manage-removable-storage-intune.md#deploy-removable-storage-access-control-by-using-intune-oma-uri) section to deploy the configuration. + ## Use Intune user interface |
| security | Device Control Removable Storage Access Control | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/device-control-removable-storage-access-control.md | DeviceEvents | project Timestamp, DeviceId, DeviceName, InitiatingProcessAccountName, ActionType, Policy, PolicyRuleId, FileInformationOperation, MediaClassName, MediaInstanceId, MediaName, MediaProductId, MediaVendorId, MediaSerialNumber, FileName, FolderPath, FileSize, FileEvidenceLocation, AdditionalFields | order by Timestamp desc ```--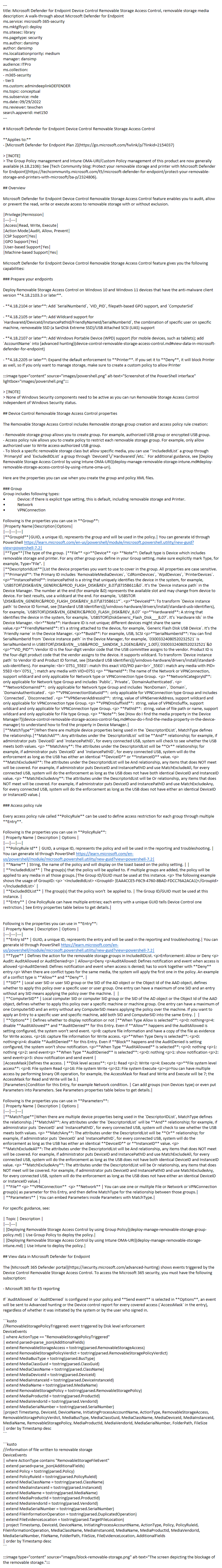 |
| security | Ios Configure Features | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/ios-configure-features.md | Network protection in Microsoft Defender for endpoint is disabled by default. Ad 2. Provide a name and description to uniquely identify the policy. Then click on 'Select Public apps' and choose 'Microsoft Defender' for Platform iOS/IPadOS :::image type="content" source="images/nameiosconfig.png" alt-text="Name the configuration." lightbox="images/nameiosconfig.png"::: -3. In Settings page, add 'DefenderNetworkProtectionEnable' as the key and value as 'true' to disable Network Protection. (Network protection is disabled by default) +3. In Settings page, add 'DefenderNetworkProtectionEnable' as the key and value as 'true' to enable Network Protection. (Network protection is disabled by default). + :::image type="content" source="images/addiosconfigvalue.png" alt-text="Add configuration value." lightbox="images/addiosconfigvalue.png"::: 4. For other configurations related to Network protection, add the following keys and appropriate corresponding value. |
| security | Run Analyzer Macos Linux | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/run-analyzer-macos-linux.md | search.appverid: met150 1. Download the [XMDE Client Analyzer](https://aka.ms/XMDEClientAnalyzer) tool to the macOS or Linux machine you need to investigate. > [!NOTE]- > The current SHA256 hash of 'XMDEClientAnalyzer.zip' that is downloaded from the above link is: 'D54FEAEB444127E486CE2B2646BCD3A076F58C44214490F60E35EDD55F763219' + > The current SHA256 hash of 'XMDEClientAnalyzer.zip' that is downloaded from the above link is: 'AD8D9D90F9C953E206E57971E9BA399471CA6E61F7034099A686E7DD6757D7C6' 2. Extract the contents of XMDEClientAnalyzer.zip on the machine. Open a terminal or SSH into the relevant machine and run the following commands: > - In addition, the tool currently requires Python version 3 or later to be installed. > > - If you are running on a machine that cannot use Python 3 or fetch the lxml component, then you can download a binary based version of the analyzer that does not have any of the requirements: [XMDE Client Analyzer Binary](https://aka.ms/XMDEClientAnalyzerBinary). <br> Note that the binary is currently unsigned. To allow the package run on MacOS, you will need to use the syntax: "spctl --add /Path/To/Application.app".-> - The current SHA256 hash of 'XMDEClientAnalyzerBinary.zip' that is downloaded from the above link is: '44099C0AA544B6A2E8676D5BB64BA79494E615E17329CE5ACC26C9F48E7F226B' +> - The current SHA256 hash of 'XMDEClientAnalyzerBinary.zip' that is downloaded from the above link is: '678866D7F14318BD7FEFCDC0259147C34366BCE84A547B5E18BCD07957A21C72' > > - If your device is behind a proxy, then you can simply pass the proxy server as an environment variable to the mde_support_tool.sh script. For example: > `https_proxy=https://myproxy.contoso.com:8080 ./mde_support_tool.sh"` |
| security | Server Migration | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/server-migration.md | These instructions apply to the new unified solution and installer (MSI) package > [!NOTE] > Operating system upgrades with Microsoft Defender for Endpoint installed are not supported. Please offboard and uninstall, upgrade the operating system, then proceed with installation. -> [!NOTE] -> Full Microsoft Endpoint Configuration Manager automation and integration to perform an automated upgrade will be available in a later release of MECM. From the 2107 release with the latest hotfix rollup, you CAN use the Endpoint Protection node for configuration as well as Group Policy, PowerShell, Microsoft Endpoint Manager tenant attach or local configuration. In addition, you can leverage existing functionality in Microsoft Endpoint Configuration Manager to automate manual upgrade steps; methods for which are described below. - ## Installer script >[!NOTE] To facilitate upgrades when Microsoft Endpoint Configuration Manager is not yet 1. Remove the OMS workspace for Microsoft Defender for Endpoint (OPTIONAL). 2. Remove System Center Endpoint Protection (SCEP) client if installed.-3. Download and install (Windows Server 2012 R2) [prerequisites](configure-server-endpoints.md#prerequisites) if required. -4. Install Microsoft Defender for Endpoint. -5. Apply the onboarding script **for use with Group Policy** downloaded from [Microsoft 365 Defender](https://security.microsoft.com). +3. Download and install [prerequisites](configure-server-endpoints.md#prerequisites) if required. +4. Enable and update the Defender Antivirus feature on Windows Server 2016 +5. Install Microsoft Defender for Endpoint. +6. Apply the onboarding script **for use with Group Policy** downloaded from [Microsoft 365 Defender](https://security.microsoft.com). To use the script, download it to an installation directory where you have also placed the installation and onboarding packages (see [Configure server endpoints](configure-server-endpoints.md)). For more information on how to use the script, use the PowerShell command "get-h ## Microsoft Endpoint Configuration Manager migration scenarios >[!NOTE]->You'll need Microsoft Endpoint Configuration Manager, version 2107 or later to perfom Endpoint Protection policy configuration. +>You'll need Microsoft Endpoint Configuration Manager, version 2107 or later to perform Endpoint Protection policy configuration. From [version 2207 or later](/mem/configmgr/core/plan-design/changes/whats-new-in-version-2207#improved-microsoft-defender-for-endpoint-mde-onboarding-for-windows-server-2012-r2-and-windows-server-2016) deployment and upgrades can be fully automated. For instructions on how to migrate using Microsoft Endpoint Configuration Manager older than version 2207 please see [Migrating servers from Microsoft Monitoring Agent to the unified solution.](/microsoft-365/security/defender-endpoint/application-deployment-via-mecm) For instructions on how to migrate using Microsoft Endpoint Configuration Manage 1. Fully update the machine including Microsoft Defender Antivirus (Windows Server 2016) ensuring [prerequisites](configure-server-endpoints.md#prerequisites) have been met. For more information on the prerequisites that have to be met, see [Prerequisites for Windows Server 2016](configure-server-endpoints.md#prerequisites-for-windows-server-2016). 2. Ensure third-party antivirus management no longer pushes antivirus agents to these machines.*-3. Author your policies for the protection capabilities in Microsoft Defender for Endpoint and target those to the machine in the tool of your choice.* +3. Author your policies for the protection capabilities in Microsoft Defender for Endpoint and target those to the machine in the tool of your choice. 4. Install the Microsoft Defender for Endpoint for Windows Server 2012 R2 and 2016 package and **enable passive mode**. See [Install Microsoft Defender Antivirus using command line](configure-server-endpoints.md#install-microsoft-defender-for-endpoint-using-the-command-line). a. Apply the onboarding script **for use with Group Policy** downloaded from [Microsoft 365 Defender](https://security.microsoft.com). 5. Apply updates. |
| security | Custom Detection Rules | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender/custom-detection-rules.md | These actions are applied to devices in the `DeviceId` column of the query resul #### Actions on files -When selected, you can choose to **Allow/Block** the file. Blocking files are only allowed if you have *Remediate* permissions for files and if the query results have identified a file ID, such as a SHA1. Once a file is blocked, other instances of the same file in all devices are also blocked. You can control which device group the blocking is applied to, but not specific devices. +- When selected, the **Allow/Block** action can be applied to the file. Blocking files are only allowed if you have *Remediate* permissions for files and if the query results have identified a file ID, such as a SHA1. Once a file is blocked, other instances of the same file in all devices are also blocked. You can control which device group the blocking is applied to, but not specific devices. -When selected, you can choose to apply the **Quarantine file** action on files in the `SHA1`, `InitiatingProcessSHA1`, `SHA256`, or `InitiatingProcessSHA256` column of the query results. This action deletes the file from its current location and places a copy in quarantine. +- When selected, the **Quarantine file** action can be applied to files in the `SHA1`, `InitiatingProcessSHA1`, `SHA256`, or `InitiatingProcessSHA256` column of the query results. This action deletes the file from its current location and places a copy in quarantine. #### Actions on users-When selected, the **Mark user as compromised** action is taken on users in the `AccountObjectId`, `InitiatingProcessAccountObjectId`, or `RecipientObjectId` column of the query results. This action sets the users risk level to "high" in Azure Active Directory, triggering corresponding [identity protection policies](/azure/active-directory/identity-protection/overview-identity-protection). -Select **Disable user** to temporarily prevent a user from logging in, or **Force password reset** to prompt the user to change their password on the next sign in session. Both **Disable user** and **Force password reset** require the user SID, which are in the columns `AccountSid`, `InitiatingProcessAccountSid`, `RequestAccountSid`, and `OnPremSid`. +- When selected, the **Mark user as compromised** action is taken on users in the `AccountObjectId`, `InitiatingProcessAccountObjectId`, or `RecipientObjectId` column of the query results. This action sets the users risk level to "high" in Azure Active Directory, triggering corresponding [identity protection policies](/azure/active-directory/identity-protection/overview-identity-protection). ++- Select **Disable user** to temporarily prevent a user from logging in. +- Select **Force password reset** to prompt the user to change their password on the next sign in session. ++Both the Disable user and Force password reset options require the user SID, which are in the columns `AccountSid`, `InitiatingProcessAccountSid`, `RequestAccountSid`, and `OnPremSid`. ++For more details on user actions, read [Remediation actions in Microsoft Defender for Identity](/defender-for-identity/remediation-actions). #### Actions on emails-If the custom detection yields email messages, you can select **Move to mailbox folder** to move the email to a selected folder (any of **Junk**, **Inbox**, or **Deleted items** folders). +- If the custom detection yields email messages, you can select **Move to mailbox folder** to move the email to a selected folder (any of **Junk**, **Inbox**, or **Deleted items** folders). ++- Alternatively, you can select **Delete email** and then choose to either move the emails to Deleted Items (**Soft delete**) or delete the selected emails permanently (**Hard delete**). -Alternatively, you can select **Delete email** and then choose to either move the emails to Deleted Items (**Soft delete**) or delete the selected emails permanently (**Hard delete**). +The columns `NetworkMessageId` and `RecipientEmailAddress` must be present to apply actions to email messages. ### 5. Set the rule scope. |
| security | Microsoft 365 Security Center Mde | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender/microsoft-365-security-center-mde.md | f1.keywords: Previously updated : 04/21/2021 Last updated : 11/14/2022 audience: ITPro search.appverid: Microsoft Defender for Endpoint in Microsoft 365 Defender supports [granting acc > What you see in Microsoft 365 Defender depends on your current subscriptions. For example, if you don't have a license for Microsoft Defender for Office 365, then the Email & Collaboration section will not be shown. > [!Note]-> Microsoft 365 Defender is not available for: +> Microsoft 365 Defender is not fully available for: >- US Government Community Cloud (GCC) >- US Government Community Cloud High (GCC High) >- US Department of Defense >- All US government institutions with commercial licenses+>- See availability for the above enviroments here: [Microsoft Defender for Endpoint for US Government customers](/microsoft-365/security/defender-endpoint/gov?view=o365-worldwide&preserve-view=true) Take a look in Microsoft 365 Defender at <a href="https://go.microsoft.com/fwlink/p/?linkid=2077139" target="_blank">https://security.microsoft.com</a>. |
| security | Top Scoring Industry Tests | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender/top-scoring-industry-tests.md | Microsoft 365 Defender combines the capabilities of [Microsoft Defender for Endp Core to MITRE's testing approach is emulating real-world attacks to understand whether solutions can adequately detect and respond to them. While the test focused on endpoint detection and response, MITRE's simulated APT29 attack spans multiple attack domains, creating opportunities to empower defenders beyond just endpoint protection. Microsoft expanded visibility beyond the endpoint with Microsoft 365 Defender. +- ATT&CK-based evaluation of Microsoft 365 Defender - April 2022: [Microsoft 365 Defender demonstrates industry-leading protection in the 2022 MITRE Engenuity ATT&CK® Evaluations]([Microsoft Security Blog: Microsoft 365 Defender demonstrates industry-leading protection in the 2022 MITRE Engenuity ATT&CK® Evaluations](https://www.microsoft.com/en-us/security/blog/2022/04/05/microsoft-365-defender-demonstrates-industry-leading-protection-in-the-2022-mitre-engenuity-attck-evaluations/)) + - ATT&CK-based evaluation of Microsoft 365 Defender - April 2021: [Evaluation proves Microsoft Defender for Endpoint stops advanced attacks across platforms](https://www.microsoft.com/security/blog/2021/04/21/) Microsoft 365 Defender provided nearly 100 percent coverage across the attack chain stages. It delivered leading out-of-box visibility into attacker activities. The visibility dramatically reduces manual work for the security operations center and vendor solutions that relied on specific configuration changes. Microsoft 365 Defender also had the fewest gaps in visibility, diminishing attacker ability to operate undetected. |
| security | Configure Your Spam Filter Policies | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/office-365-security/configure-your-spam-filter-policies.md | Creating a custom anti-spam policy in the Microsoft 365 Defender portal creates |Action|Spam|High<br>confidence<br>spam|Phishing|High<br>confidence<br>phishing|Bulk| ||::|::|::|::|::|- |**Move message to Junk Email folder**: The message is delivered to the mailbox and moved to the Junk Email folder.<sup>1</sup>|Γ£ö<sup>\*</sup>|Γ£ö<sup>\*</sup>|Γ£ö||Γ£ö<sup>\*</sup>| + |**Move message to Junk Email folder**: The message is delivered to the mailbox and moved to the Junk Email folder.<sup>1,4</sup>|Γ£ö<sup>\*</sup>|Γ£ö<sup>\*</sup>|Γ£ö||Γ£ö<sup>\*</sup>| |**Add X-header**: Adds an X-header to the message header and delivers the message to the mailbox. <p> You enter the X-header field name (not the value) later in the **Add this X-header text** box. <p> For **Spam** and **High confidence spam** verdicts, the message is moved to the Junk Email folder.<sup>1,2</sup>|Γ£ö|Γ£ö|Γ£ö||Γ£ö| |**Prepend subject line with text**: Adds text to the beginning of the message's subject line. The message is delivered to the mailbox and moved to the Junk email folder.<sup>1,2</sup> <p> You enter the text later in the **Prefix subject line with this text** box.|Γ£ö|Γ£ö|Γ£ö||Γ£ö| |**Redirect message to email address**: Sends the message to other recipients instead of the intended recipients. <p> You specify the recipients later in the **Redirect to this email address** box.|Γ£ö|Γ£ö|Γ£ö|Γ£ö|Γ£ö| Creating a custom anti-spam policy in the Microsoft 365 Defender portal creates > > <sup>3</sup> A blank **Select a policy** value means the default quarantine policy for that particular verdict is used. When you later edit the anti-spam policy or view the settings, the default quarantine policy name is shown. For more information about default quarantine policies that are used for the spam filter verdicts, see [this table](quarantine-policies.md#step-2-assign-a-quarantine-policy-to-supported-features). >+ > <sup>4</sup> For **High confidence phishing**, the action **Move message to Junk Email folder** has effectively been deprecated. Although you might be able to select *Move message to Junk Email folder**, high confidence phishing messages are always quarantined (equivalent to selecting **Quarantine message**). + > > Users can't release their own messages that were quarantined as high confidence phishing. At best, admins can configure the quarantine policy so users can request the release of their quarantined high confidence phishing messages. - **Retain spam in quarantine for this many days**: Specifies how long to keep the message in quarantine if you selected **Quarantine message** as the action for a spam filtering verdict. After the time period expires, the message is deleted, and is not recoverable. A valid value is from 1 to 30 days. |
| security | User Submission | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/office-365-security/user-submission.md | When you're finished on the **User submissions** page, click **Save**. To restor You can turn off the Microsoft integrated reporting experience to use third-party message reporting tools to send reported messages to the user submissions mailbox. -The only requirement is that the original messages are included as uncompressed .EML or .MSG attachments in messages that are sent to user submissions mailbox. In other words, don't just forward the original messages to the user submissions mailbox. +When **Microsoft Outlook Report Message button** is **Off**  the following settings are available on the **User reported settings** page: -> [!NOTE] -> If multiple email attachments exist in the message, then the submission will be discarded. We only support message with one email attachment. --The message formatting requirements are described in the next section. The formatting is optional, but reported messages don't follow the prescribed format, the reported messages are always identified as phishing. +- **Use Microsoft's integrated Outlook reporting experience** section: -When **Microsoft Outlook Report Message button** is **Off**  the following settings are available on the **User submissions** page: + **Use this custom mailbox to receive user reported messages**: Select this option and enter the email address of an existing Exchange Online mailbox to hold user-reported messages from third-party message reporting tools. These messages are not submitted to Microsoft. They appear on the **User reported** tab of the **Submissions** page at <https://security.microsoft.com/reportsubmission?viewid=user>. The **Result** value for these entries is **Not Submitted to Microsoft**. + + A reported message that's sent to the user submissions mailbox must include the original message as an uncompressed .EML or .MSG attachment. Don't forward the original message to the user submissions mailbox. -- **Use Microsoft's integrated Outlook reporting experience** section:+ > [!NOTE] + > Messages that contain multiple attached messages will be discarded. We support only one attached original message in a reported message. - **Use this custom mailbox to receive user reported messages**: Select this option and enter the email address of an existing Exchange Online mailbox to use as the user submissions mailbox. Distribution groups are not allowed. + The message formatting requirements are described in the next section. The formatting is optional, but if reported messages don't follow the prescribed format, they're always identified as phishing. - **Customize your organization's experience when reporting potential threats in quarantine** section: - **Quarantine report message button**: Verify this setting is **On**  to let users report messages from quarantine. Otherwise, turn this setting **Off** . + **Quarantine report message button**: Verify this setting is **On**  to let users report messages from quarantine. Otherwise, turn this setting **Off** . When you're finished on the **User submissions** page, click **Save**. To restore the settings to their immediately previous values, click **Restore**. |
| solutions | Groups Teams Access Governance | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/solutions/groups-teams-access-governance.md | The following table provides a quick reference for the access controls available |Category|Description|Reference| |:-|:-|:--| |Membership|||-||Discovery of private teams|[Manage discovery of private teams in Microsoft Teams](/microsoftteams/manage-discovery-of-private-teams)| ||Dynamic group membership based on rules|[Create or update a dynamic group in Azure Active Directory](/azure/active-directory/users-groups-roles/groups-create-rule)| ||Control who can share files, folders, and sites.|[Set up and manage access requests](https://support.microsoft.com/office/94b26e0b-2822-49d4-929a-8455698654b3)| |Conditional access||| Additional resources: [Create and manage an external network in Yammer](/yammer/work-with-external-users/create-and-manage-an-external-network) -[Configure Teams with three tiers of protection](./configure-teams-three-tiers-protection.md) +[Configure Teams with three tiers of protection](./configure-teams-three-tiers-protection.md) |