| Category | Microsoft Docs article | Related commit history on GitHub | Change details |
|---|---|---|---|
| README | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/README.md | ## Learn how to contribute -Anyone who is interested can contribute to the topics. When you contribute, your work will go directly into the content set after being merged. It will then show up on Microsoft Learn and you will be listed as a contributor at: <https://github.com/MicrosoftDocs/microsoft-365-docs/graphs/contributors>. +Anyone who is interested can contribute to the topics. When you contribute, your work will go directly into the content set after being merged. It will then be published to [Microsoft Learn](https://learn.microsoft.com/) and you will be listed as a contributor at: <https://github.com/MicrosoftDocs/microsoft-365-docs/graphs/contributors>. ### Quickly update an article using GitHub.com Contributors who only make infrequent or small updates can edit the file directly on GitHub.com without having to install any additional software. This article shows you how. [This two-minute video](https://www.microsoft.com/videoplayer/embed/RE1XQTG) also covers how to contribute. 1. Make sure you're signed in to GitHub.com with your GitHub account.-2. Go to the page you want to edit on Microsoft Learn. +2. Browse to the page you want to edit on Microsoft Learn. 3. On the right-hand side of the page, click **Edit** (pencil icon). -  + 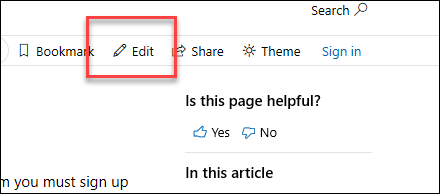 4. The corresponding topic file on GitHub opens, where you need to click the **Edit this file** pencil icon. -  + 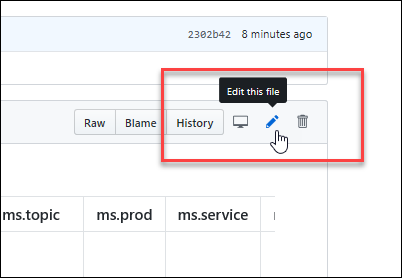 5. The topic opens in a line-numbered editing page where you can make changes to the file. Files in GitHub are written and edited using Markdown language. For help on using Markdown, see [Mastering Markdown](https://guides.github.com/features/mastering-markdown/). Select the **Preview changes** tab to view your changes as you go. Contributors who only make infrequent or small updates can edit the file directl When you're ready, click the green **Propose file change** button. -  + 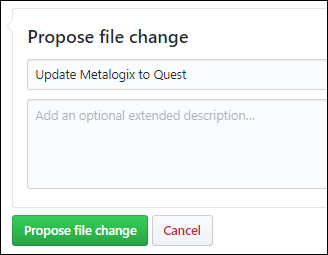 7. On the **Comparing changes** page that appears, click the green **Create pull request** button. -  + 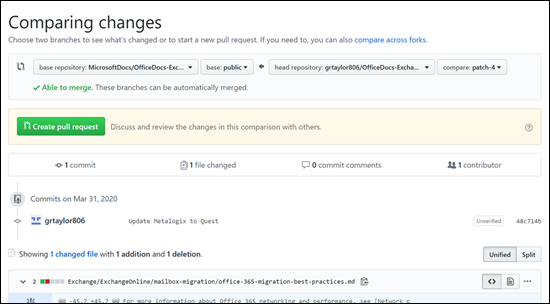 8. On the **Open a pull request** page that appears, click the green **Create pull request** button. -  +  > [!NOTE] > Your permissions in the repo determine what you see in the last several steps. People with no special privileges will see the **Propose file change** section and subsequent confirmation pages as described. People with permissions to create and approve their own pull requests will see a similar **Commit changes** section with extra options for creating a new branch and fewer confirmation pages.<br/><br/>The point is: click any green buttons that are presented to you until there are no more. |
|
| admin | About Admin Roles | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/admin/add-users/about-admin-roles.md | You'll probably only need to assign the following roles in your organization. By |User admin | Assign the User admin role to users who need to do the following for all users: <br> - Add users and groups <br> - Assign licenses <br> - Manage most users properties <br> - Create and manage user views <br> - Update password expiration policies <br> - Manage service requests <br> - Monitor service health <br><br> The user admin can also do the following actions for users who aren't admins and for users assigned the following roles: Directory reader, Guest inviter, Helpdesk admin, Message center reader, Reports reader: <br> - Manage usernames<br> - Delete and restore users<br> - Reset passwords <br> - Force users to sign out <br> - Update (FIDO) device keys | |User Experience Success Manager | Assign the User Experience Success Manager role to users who need to access Experience Insights, Adoption Score, and the Message Center in the Microsoft 365 admin center. This role includes the permissions of the Usage Summary Reports Reader role. | +## Permissions based on Admin role and Group type in M365 Admin page ++|Admin Role | M365 Groups | Security Groups | Distribution Groups | Mail Enabled Security Groups | +| | | | | | +| Global admin | Create, Read, Update, Delete | Create, Read, Update, Delete | Create, Read, Update, Delete | Create, Read, Update, Delete | +| Global reader | Read | Read | Read | Read | +| User admin | Create, Read, Update, Delete, ***Can't update EXO properties*** | Create, Read, Update, Delete | Read | Read | +| Exchange admin | Create, Read, Update, Delete | Create, Read, Update, Delete - *only groups they own* | Create, Read, Update, Delete | Create, Read, Update, Delete | +| Teams admin | Create, Read, Update, Delete, ***Can't update EXO properties*** | Create, Read, Update, Delete - _only groups they own_ | Read | Read | +| SharePoint admin | Create, Read, Update, Delete, ***Can't update EXO properties*** | Create, Read, Update, Delete -_only groups they own_ | Read | Read | +| Billing admin | Read | Read | Read | Read | +| Skype admin | Read | Read | Read | Read | +| Service admin | Read | Read | Read | Read | +| Group admin | Create, Read, Update, Delete, ***Can't update EXO properties*** | Create, Read, Update, Delete | Read | Read | + ## Delegated administration for Microsoft Partners If you're working with a Microsoft partner, you can assign them admin roles. They, in turn, can assign users in your company, or their company, admin roles. You might want them to do this, for example, if they're setting up and managing your online organization for you. |
| admin | Support Contact Info | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/admin/support-contact-info.md | English: 24 hours a day, 7 days a week Select "Business", then select "Microsoft 365"\ Local call charges apply. +Alternative Phone Number:\ +00 800101716\ +Local toll-free + :::column-end::: + :::column::: **Billing support hours:**\ Arabic: Sunday through Thursday, 10 AM-6 PM\ English: Monday through Friday, 10 AM-6 PM- :::column-end::: - :::column::: + **Technical support hours:**\ Arabic: Sunday through Thursday, 10 AM-6 PM\ English: 24 hours a day, 7 days a week |
| commerce | Tax Information | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/commerce/billing-and-payments/tax-information.md | Last updated 03/17/2021 When you buy Microsoft 365 products and services, the taxes that you pay are determined by one of two things: your business address, or your shipping address, if it's different. If your organization is in the United States, you must provide a Federal Employer Identification Number (FEIN). -Businesses in the following countries can provide their VAT number or local equivalent: +Businesses in the following countries or regions can provide their VAT number or local equivalent: :::row::: :::column::: Businesses in the following countries can provide their VAT number or local equi :::column-end::: :::row-end::: -*For most of the countries listed, providing a VAT number or local equivalent is optional. For Brazil and India, the tax identifier number is required. +*For most of the countries or regions listed, providing a VAT number or local equivalent is optional. For Brazil and India, the tax identifier number is required. > [!Note] > If you need to contact support, have your FEIN, VAT number, or local equivalent ready to give to the support agent. |
| compliance | Audit Log Activities | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/audit-log-activities.md | The following table lists events that result from using [sensitivity labels](sen |**Friendly name**|**Operation**|**Description**| |:--|:--|:--|-|Applied sensitivity label to site|SensitivityLabelApplied|A sensitivity label was applied to a SharePoint or Teams site.| -|Removed sensitivity label from site|SensitivityLabelRemoved|A sensitivity label was removed from a SharePoint or Teams site.| +|Applied sensitivity label to site|SiteSensitivityLabelApplied|A sensitivity label was applied to a SharePoint or Teams site.| +|Removed sensitivity label from site|SiteSensitivityLabelRemoved|A sensitivity label was removed from a SharePoint or Teams site.| |Applied sensitivity label to file|FileSensitivityLabelApplied|A sensitivity label was applied to a document by using Microsoft 365 apps, Office on the web. or an auto-labeling policy.| |Changed sensitivity label applied to file|FileSensitivityLabelChanged<br /><br>SensitivityLabelUpdated|A different sensitivity label was applied to a document. <br /><br>The operations for this activity are different depending on how the label was changed:<br /> - Office on the web or an auto-labeling policy (FileSensitivityLabelChanged) <br /> - Microsoft 365 apps (SensitivityLabelUpdated)|-|Changed sensitivity label on a site|SensitivityLabelChanged|A different sensitivity label was applied to a SharePoint or Teams site.| +|Changed sensitivity label on a site|SiteSensitivityLabelChanged|A different sensitivity label was applied to a SharePoint or Teams site.| |Removed sensitivity label from file|FileSensitivityLabelRemoved|A sensitivity label was removed from a document by using Microsoft 365 apps, Office on the web, an auto-labeling policy, or the [Unlock-SPOSensitivityLabelEncryptedFile](/powershell/module/sharepoint-online/unlock-sposensitivitylabelencryptedFile) cmdlet.| ## Retention policy and retention label activities |
| compliance | Autoexpanding Archiving | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/autoexpanding-archiving.md | description: "Learn about auto-expanding archiving, which provides additional ar >*[Microsoft 365 licensing guidance for security & compliance](/office365/servicedescriptions/microsoft-365-service-descriptions/microsoft-365-tenantlevel-services-licensing-guidance/microsoft-365-security-compliance-licensing-guidance).* -Archive mailboxes in Microsoft Purview provide users with additional mailbox storage space. After a user's archive mailbox is enabled, up to 100 GB of additional storage becomes available. +Archive mailboxes in Microsoft Purview provide user mailboxes and shared mailboxes with additional mailbox storage space. After an archive mailbox is enabled, up to 100 GB of additional storage becomes available. This archiving feature in Microsoft Purview (called *auto-expanding archiving*) provides up to 1.5 TB of additional storage in archive mailboxes. When the storage quota in the archive mailbox is reached, Microsoft Purview automatically (and incrementally) increases the size of the archive until the archive mailbox reaches 1.5 TB. For step-by-step instructions for turning on auto-expanding archiving, see [Enable auto-expanding archiving](enable-autoexpanding-archiving.md). -> [!NOTE] -> Auto-expanding archiving also supports shared mailboxes. - [!INCLUDE [purview-preview](../includes/purview-preview.md)] ## How auto-expanding archiving works -As explained in the introduction, additional mailbox storage space is created when a user's archive mailbox is enabled. When auto-expanding archiving is enabled, Microsoft Purview periodically checks the size of the archive mailbox. When an archive mailbox gets close to its storage limit, additional storage space is automatically created for the archive. If the user runs out of this additional storage space, more storage space is automatically added to the user's archive. This process continues until the user's archive reaches a size 1.5 TB. This process happens automatically, which means administrators don't have to request additional archive storage or manage auto-expanding archiving. +When auto-expanding archiving is enabled for a user's mailbox archive or a shared mailbox archive, Microsoft Purview periodically checks the size of the archive mailbox. When the archive mailbox gets close to its storage limit, additional storage space is automatically created and this process continues until the mailbox archive reaches 1.5 TB. The additional storage creation happens automatically, which means administrators don't have to request additional archive storage or manage auto-expanding archiving. Here's a quick overview of the process. Here's a quick overview of the process. 3. Microsoft Purview automatically adds more storage space when necessary. -> [!IMPORTANT] -> Auto-expanding archiving is supported only for mailboxes used for individual users (or shared mailboxes) with a growth rate that doesn't exceed 1 GB per day. A user's archive mailbox is intended for just that user. Using journaling, transport rules, or auto-forwarding rules to copy messages to an archive mailbox is not permitted. Microsoft reserves the right to deny additional archiving in instances where a user's archive mailbox is used to store archive data for other users or in other cases of the inappropriate use. +For information what happens when the maximum 1.5 TB is reached, and other size-related limitations for email storage, see [Important considerations and limitations for auto-expanding archiving](#important-considerations-and-limitations-for-auto-expanding-archiving) on this page. ## What gets moved to the additional archive storage space? The following screenshots show a folder list before and after messages are moved > [!NOTE] > As previously described, Microsoft Purview moves items to subfolders (and names them using the naming convention described above) to help distribute content to an auxiliary archive. But moving items to subfolders may not always be the case. Sometimes an entire folder may be moved to an auxiliary archive. In this case, the folder will retain its original name. It won't be apparent in the folder list in Outlook that the folder was moved to an auxiliary archive. +## Important considerations and limitations for auto-expanding archiving ++If a mailbox with an auto-expanding archive reaches a total of 1.5 TB of data stored in the auto-expanding archive, no more data will be stored in the auto-expanding archive or moved from the main archive to the auto-expanding archive. ++Should the main archive also reaches its quota, no more data will be stored there, which can result in the primary mailbox also reaching its quota. Then, processing can stop for sending or receiving email and other items. To reduce this risk and minimize liability for your organization, we recommend using Microsoft 365 retention policies to delete content that no longer has business value. Configure these policies to [delete items after a specified period](retention-settings.md#settings-for-retaining-and-deleting-content). If you're not yet familiar with retention policies that can automatically delete email and other Microsoft 365 items, see [Learn about retention policies and retention labels](retention.md). ++Auto-expanding archiving is supported only for mailboxes used for individual users (or shared mailboxes) with a growth rate that doesn't exceed 1 GB per day. A user's archive mailbox is intended for just that user. Using journaling, transport rules, or auto-forwarding rules to copy messages to an archive mailbox is not permitted. Microsoft reserves the right to deny additional archiving in instances where a user's archive mailbox is used to store archive data for other users or in other cases of the inappropriate use. + ## Outlook requirements for accessing items in an auto-expanded archive To access messages that are stored in an auto-expanded archive, users have to use one of the following Outlook clients: |
| compliance | Dlp Learn About Dlp | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/dlp-learn-about-dlp.md | Start by defining your control objectives, and how they apply across each respec #### Implement policy in test mode -Evaluate the impact of the controls by implementing them with a DLP policy in test mode. It's ok to apply the policy to all workloads in test mode, so that you can get the full breadth of results, but you can start with one workload if you need to. +Evaluate the impact of the controls by implementing them with a DLP policy in test mode. Actions defined in a policy are not applied while the policy is in test mode. It's ok to apply the policy to all workloads in test mode, so that you can get the full breadth of results, but you can start with one workload if you need to. #### Monitor outcomes and fine-tune the policy While in test mode, monitor the outcomes of the policy and fine-tune it so that - adjusting the locations and people/places that are in or out of scope - tune the conditions that are used to determine if an item and what is being done with it matches the policy - the sensitive information definition/s-- the actions-- the level of restrictions - add new controls - add new people - add new restricted apps |
| compliance | Retention Regulatory Requirements | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/retention-regulatory-requirements.md | This report helps you understand how the system aspects of the New Zealand Publi ## SEC 17a-4(f), FINRA 4511(c), and CFTC 1.31(c)-(d) -**Cohasset Assessment - Microsoft 365 - SEC Rule 17a-4(f) - Immutable Storage for SharePoint, OneDrive, Exchange, Teams, and Yammer** - [Download assessment](https://servicetrust.microsoft.com/ViewPage/TrustDocuments?command=Download&downloadType=Document&downloadId=9fa8349d-a0c9-47d9-93ad-472aa0fa44ec&docTab=6d000410-c9e9-11e7-9a91-892aae8839ad_FAQ_and_White_Papers) +**Cohasset Assessment - Microsoft 365 - SEC Rule 17a-4(f) - Immutable Storage for SharePoint, OneDrive, Exchange, Teams, and Yammer** - [Download assessment](https://servicetrust.microsoft.com/DocumentPage/f028b699-8e39-451e-8af4-e8a66426068b) Applicable workloads: SharePoint, OneDrive, Teams, Exchange, and Yammer |
| compliance | Sensitivity Labels Meetings | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/sensitivity-labels-meetings.md | description: "Configure sensitivity labels to protect calendar items, and Teams >*[Microsoft 365 licensing guidance for security & compliance](/office365/servicedescriptions/microsoft-365-service-descriptions/microsoft-365-tenantlevel-services-licensing-guidance/microsoft-365-security-compliance-licensing-guidance).* > [!NOTE]-> This feature is currently rolling out in preview and subject to change. If you don't see all the options referenced on this page, try again in a few days. +> This feature is currently rolling out in preview and subject to change. > -> Also, the Teams options require a [Teams Premium license](/MicrosoftTeams/enhanced-teams-experience). For more information about this new premium add-on for Teams, see the [blog post announcement](https://www.microsoft.com/microsoft-365/blog/2022/10/12/introducing-microsoft-teams-premium-the-better-way-to-meet) and the official [Teams Premium site](https://www.microsoft.com/microsoft-teams/premium). +> You won't be able to configure all the options referenced on this page if a [Teams Premium license](/MicrosoftTeams/enhanced-teams-experience) isn't found for your tenant. For those settings, you'll see an information bar in the Microsoft Purview compliance portal that your organization doesn't have this license. In addition to using [sensitivity labels](sensitivity-labels.md) to protect documents and emails, you can extend sensitivity labels to protect meeting invites and responses that use Outlook and Teams, and to protect Teams meetings and chat: |
| compliance | Sensitivity Labels Sharepoint Default Label | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/sensitivity-labels-sharepoint-default-label.md | description: "Configure a default sensitivity label for a SharePoint document li >*[Microsoft 365 licensing guidance for security & compliance](/office365/servicedescriptions/microsoft-365-service-descriptions/microsoft-365-tenantlevel-services-licensing-guidance/microsoft-365-security-compliance-licensing-guidance).* > [!NOTE]-> This feature is in preview and subject to change. Licensing options will be provided when the feature becomes generally available (GA). -> -> To read the preview announcement, see the [blog post](https://techcommunity.microsoft.com/t5/security-compliance-and-identity/public-preview-default-label-for-a-document-library-in/ba-p/3585136). +> This feature is in preview and subject to change. When SharePoint is [enabled for sensitivity labels](sensitivity-labels-sharepoint-onedrive-files.md), you can configure a default label for document libraries. Then, any new files uploaded to that library, or existing files edited in the library will have that label applied if they don't already have a sensitivity label, or they have a sensitivity label but with [lower priority](sensitivity-labels.md#label-priority-order-matters). When you use Office on the web to create or edit a file, the default sensitivity - File upload: it can take a few minutes for the label to be applied. - Microsoft 365 Apps: the label is applied after the app is closed. +To read the preview announcement for this feature, see the [blog post](https://techcommunity.microsoft.com/t5/security-compliance-and-identity/public-preview-default-label-for-a-document-library-in/ba-p/3585136). + [!INCLUDE [purview-preview](../includes/purview-preview.md)] ## Will an existing label be overridden? Summary of outcomes: - [SharePoint Information Rights Management (IRM) is not enabled for the library](set-up-irm-in-sp-admin-center.md#irm-enable-sharepoint-document-libraries-and-lists). This older technology isn't compatible with using a default sensitivity label for a SharePoint document library. If a library is enabled for IRM, you won't be able to select a default sensitivity label. +If you need to review a list of file types that are supported by sensitivity labels in SharePoint, see [Supported file types](sensitivity-labels-sharepoint-onedrive-files.md#supported-file-types). + ## Limitations - Doesn't apply to existing files at rest in SharePoint. |
| compliance | Whats New | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/compliance/whats-new.md | Whether it be adding new solutions to the [Microsoft Purview compliance portal]( ### Communication compliance - New [transparency note](/microsoft-365/compliance/communication-compliance-solution-overview) to convey the purpose and intended uses of machine learning in policy templates that use classifiers for business conduct and regulatory compliance. - Changed the [time zone from local time zone to Coordinated Universal Time (UTC)](/microsoft-365/compliance/communication-compliance-policies) for policy activity detection, user-reported messages, and filters for reports.-- Updated table for [built-in trainable and global classifiers](/microsoft-365/compliance/communication-compliance-policies) to increase visibility for details specific to pre-trained classifiers. Includes updated word count requirements for messages in English and non-English languages. +- Updated table for [built-in trainable and global classifiers](/microsoft-365/compliance/communication-compliance-policies) to increase visibility for details specific to pre-trained classifiers. Includes updated word count requirements for messages in English and non-English languages. ++### Compliance Manager +- Assessment templates that belong to the same regulation family now count as one template. The [definition of **included templates**](compliance-manager-templates-list.md#included-templates) has been updated to align with [template licensing changes starting December 2022](compliance-manager-faq.yml#what-changed-with-template-licensing-in-december-2022-). +- Improvement actions now provide greater visibility into related controls and assessments. Improvement action details pages have a new [**Related controls** tab](compliance-manager-improvement-actions.md#related-controls), and the **Summary** section has a clickable **Assessments** number that, when selected, lists all the assessments related to that action. ### Data lifecycle management and records management - Disposition review no longer has a maximum of 1,000,000 items per label pending or reviewed. This limitation is removed from [Limits for retention policies and retention label policies](retention-limits.md). Whether it be adding new solutions to the [Microsoft Purview compliance portal]( ### Insider risk management - [Examples of file paths](/microsoft-365/compliance/insider-risk-management-settings) to denote specific and wildcard folders and sub-folders to be excluded. +### Microsoft Priva +- [Tags for reviewing data in a subject rights request](/privacy/priva/subject-rights-requests-data-review#apply-tags) provide greater flexibility. There are now two default tags and 21 custom tags that can be named and defined by an organization. Tags can now be applied to, or removed from, mutlipe content items at once. +- The maximum file size for [file import during data review](/privacy/priva/subject-rights-requests-data-review#import-additional-files) for a subject rights request has increased to 500 MB. +- Instructions for working with the [action execution log report](/privacy/priva/subject-rights-requests-delete#action-execution-log-report) for a delete request have been updated; including a clarification that its retention period is the same as all other subject rights request reports. + ### Sensitivity labels - **General availability (GA)**: S/MIME support for Windows is now available in the Office Current Channel, providing parity with the AIP add-in. For more information, see [Apply S/MIME protection](sensitivity-labels-office-apps.md#configure-a-label-to-apply-smime-protection-in-outlook). - **Rolling out in preview**: Protected meetings by [labeling calendar invites and responses, Teams meetings, and chat](sensitivity-labels-meetings.md). |
| enterprise | Microsoft 365 Exo Archive Advisory | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/enterprise/microsoft-365-exo-archive-advisory.md | + + Title: "Service advisories for auto-expanding archive utilization in Exchange Online monitoring" ++++audience: Admin +++ms.localizationpriority: medium +search.appverid: +- MET150 ++- scotvorg +- Ent_O365 +- Strat_O365_Enterprise ++- admindeeplinkMAC +- admindeeplinkEXCHANGE +f1.keywords: +- NOCSH +description: "Use service advisories to monitor mailboxes that are at risk of reaching or exceeding the auto-expanding archive size limits." ++++# Service advisories for auto-expanding archive utilization in Exchange Online monitoring ++We've released a new Exchange Online service advisory that informs you of auto-expanding archives attached to mailboxes that are at risk of reaching or exceeding the 1.5TB cumulative limit on auto-expanding archive size. These service advisories provide visibility to the mailboxes in your organization that may require admin intervention. ++These service advisories are displayed in the Microsoft 365 admin center. To view these service advisories, go to **Health** \> **Service health** \> **Exchange Online** and then click the **Active issues** tab. ++## What do these service advisories indicate? ++This service advisory informs you of potential data storage limits being reached in your organization. Mailboxes with archive mailboxes that have the auto-expanding archive feature enabled may store a maximum of 1.5TB of data in the auto-expanding archive. The service advisory contains a table with information about the mailboxes nearing this limit in your organization. Here's an example of the table: ++| mailboxGuid | Status | SizeInGB | +| | | | +| b47c25fd-3d78-481c-970b-6799bc454275 | Warning | 1312 | +| faf1c53e-9214-48aa-b91e-f908f3c1c762 | Warning | 1316 | +| c874b925-989a-4119-aa39-b6280a456b9e | Critical | 1499 | ++The following list describes each column in the previous example. ++- **mailboxGuid** : The GUID of the main archive for the mailbox or one of the additional storage units in the auxiliary archive ("AuxArchive"). +- **Status** : _Warning_ if the auto-expanding archive total size is over 1.2TB but less than 1.4TB; _Critical_ if the auto-expanding archive total size is over 1.4TB. +- **SizeInGB** : The total size of the auto-expanding archive associated with the mailbox. ++## More information ++For more information about auto-expanding archive limits and considerations, see the following articles: ++- [Learn about auto-expanding archiving](/microsoft-365/compliance/autoexpanding-archiving) ++- [Customize an archive and deletion policy for mailboxes in your organization](/microsoft-365/compliance/set-up-an-archive-and-deletion-policy-for-mailboxes) |
| enterprise | Multi Tenant People Search | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/enterprise/multi-tenant-people-search.md | f1.keywords: description: Learn about People Search in multi-tenant Microsoft 365 organizations. -# Microsoft 365 Multi-Tenant Organization People Search Private Preview +# Microsoft 365 Multi-Tenant Organization People Search (private preview) -## Overview +The Multi-Tenant Organization (MTO) People Search is a collaboration feature that enables search and discovery of people across multiple tenants. A tenant admin can enable cross-tenant synchronization that will allow users to be synced to another tenant and be discoverable in its global address list. Once enabled, users will be able to search and discover synced user profiles from the other tenant and view their corresponding people cards. -The Private Preview program is designed to offer select customers the opportunity to try out the multi-tenant people search feature. You can then validate the scenario and provide feedback to the product development team. The purpose of this article is to: --- Give an overview of the feature.-- Define use cases that we currently support as part of the preview.-- Provide instructions on how you can configure this feature and test it.--## Feature Overview --The MTO People Search is a collaboration feature that enables search and discovery of people across multiple tenants. A tenant admin can enable a Cross-Tenant synchronization will allow users to be synced into another tenant and be discoverable in the global address list. Once enabled, users will be able to search and discover synced user profiles from the other tenant and view their corresponding people card. +>[!NOTE] +>This Private Preview program is designed to offer select customers the opportunity to try out the multi-tenant people search feature. You can then validate the scenario and provide feedback to the product development team. The purpose of this article is to: +> +>- Give an overview of the feature +>- Define use cases that we currently support as part of the preview +>- Provide instructions on how you can configure and test the feature  -> *Fig 1. AAD sync illustration* +> _Fig 1: Azure AD sync illustration_ -### Example +## Example scenario -Cameron from Fabrikam has been synced to the target tenant, Woodgrove. Megan from Woodgrove would like to search and view Cameron's people card in Teams. After Cameron has been synced, Megan can search and discover Cameron's people card in any of the Microsoft 365 apps. +Megan's user account has been synced from the _Fabrikam_ tenant to the target tenant, _Contoso_. Nestor from Contoso would like to search and view Megan's people card in Teams. After Megan's account has been synced, Nestor can search and discover Megan's people card in any of the Microsoft 365 apps.  -> *Fig 2 User is able to view a limited people card* +> _Fig 2: User can view a limited people card_ ++### In-tenant view of people card -### In Tenant view of People Card +The people card shows all the user's attributes including the profile picture when viewing a user's people card within the same tenant. - + -### Known Limitations +> _Fig 3: User can view extended people card within the same tenant_ -- The teams audio and video call buttons will direct the call to the users Home tenant instance (Fabrikam) and not the Target tenant teams instance (Woodgrove).+## Known limitations +- The Microsoft Teams audio and video call buttons will direct the call to the user's home tenant Teams instance (Fabrikam) and not the Teams instance target tenant (Contoso). - The current experience provides limited information on the people card (basic contact information, job title and office location). -### Prerequisites +## Prerequisites -To test the MTO people search scenario, it is assumed that you already have the following settings: +To test the MTO People Search feature, it is assumed that you already have the following settings: - Two Azure AD/Microsoft 365 tenants+- Both tenants have the **Azure AD Cross-tenant Synchronization** feature enabled (currently in private preview - make sure you sign up for both preview features) +- Provisioned users from home to target tenants as described in [Instructions to enable Tenant-to-Tenant Sync](https://github.com/ArvindHarinder1/CrossTenantSynchronization/blob/main/CrossTenantSynchronization.md) -- The tenants are enabled for Private Preview of Cross Tenant Synchronization--- Provisioned users from Home to target tenants. [Instructions to enable Tenant-to-Tenant sync](https://github.com/ArvindHarinder1/CrossTenantSynchronization/blob/main/CrossTenantSynchronization.md)--### Use Cases +## Use Cases Multi-tenant organization people search is supported across a range of scenarios and Microsoft 365 applications. Some of the scenarios you can test and validate are described below: -1. **Microsoft Outlook (OWA, Desktop and Mobile)** +1. **Microsoft Outlook (OWA, desktop and mobile app)** - - <alice@fabrikam.com> searches for "Bob" on the centralized search bar in OWA and gets the results and can view Bobs people card with limited profile information. - - <alice@fabrikam.com> types in "Bob" in the To line of the email and can send an email to Bob after getting the results for <bob@woodgrove.ms>. - - <alice@fabrikam.com> \@mentions "Bob" in the body of the email and can get the result for <bob@woodgrove.ms>. - - <alice@fabrikam.com> types in "Bob" in the cc line of the email and can get the result for <bob@woodgrove.ms>. - - Alice can hover and/or click on Bob's facepile to view Bob's limited people card. + - Nestor (<nestor@contoso.com>) searches for "Megan" on the centralized search bar in OWA and gets the results and can view Megan's people card with limited profile information. + - Nestor types in "Megan" in the _To_ line of the email and can send an email to Megan after getting the results for <megan@fabrikam.com>. + - Nestor \@mentions "Megan" in the body of the email and can get the result for <megan@fabrikam.com>. + - Nestor types in "Megan" in the _cc_ line of the email and can get the result for <megan@fabrikam.com>. + - Nestor can hover and/or click on Megan's profile picture/initials to view Megan's limited people card. 2. **Microsoft OneDrive/Sharepoint** - - <alice@fabrikam.com> searches for "Bob" in the centralized search bar on SharePoint and can get the result for <bob@woodgrove.ms>. - - Alice can hover and/or click on Bob's facepile to view Bob's limited people card. - - Alice can share and collaborate on Office documents with Bob. + - Nestor (<nestor@contoso.com>) searches for "Megan" in the centralized search bar on SharePoint and can get the result for <megan@fabrikam.com>. + - Nestor can hover and/or click on Megan's profile picture/initials to view Megan's limited people card. + - Nestor can share and collaborate on Office documents with Megan. -3. **Microsoft Teams (Web, Desktop or Mobile App)** +3. **Microsoft Teams (Web, desktop and mobile app)** - - <alice@fabrikam.com> searches for "Bob" on the Teams people picker and can view Bob's limited people card. - - <alice@fabrikam.com> searches for "Bob" on the Teams power bar and can view Bob's limited people card Team membership. + - Nestor (<nestor@contoso.com>) searches for "Megan" on the Teams people picker and can view Megan's limited people card. + - Nestor searches for "Megan" on the Teams power bar and can view Megan's limited people card Team membership. 4. **Bing for Business** - - <alice@fabrikam.com> searches for "Bob" on the search bar and can view Bob's limited people card (<bob@woodgrove.ms>). --### Key Terminology + - Nestor (<nestor@contoso.com>) searches for "Megan" on the search bar and can view Megan's limited people card (<megan@fabrikam.com>). -- Home tenant: The tenant you want to search from. The direction of the search is *outbound*.+## Key terminology -- Resource tenant: The tenant you want to search in. The direction of the search is *inbound*.+- _Home tenant_: The tenant you want to search from. The direction of the search is _outbound_. -- A tenant can be both home and resource tenant simultaneously.+- _Resource tenant_: The tenant you want to search in. The direction of the search is _inbound_. -- Home tenant admin: The IT admin in the home tenant.+ A tenant can be both home and resource tenant simultaneously. -- Cross-Tenant synchronization is a feature enables multi-tenant organizations to grant users access to applications in other tenants within the organization. It achieves this result by synchronizing internal member users from a home tenant into a resource tenant as external B2B users.+- _Cross-Tenant synchronization_ is a feature that enables multi-tenant organizations to grant users access to applications in other tenants within the organization. It achieves this by synchronizing internal member users from a home tenant into a resource tenant as external B2B users. -## Contact Us +## Contact us You can contact the Cross Tenant People Search team via email at [MTOPeopleSearchPreview@service.microsoft.com](mailto:MTOPeopleSearchPreview@service.microsoft.com). |
| enterprise | View Service Health | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/enterprise/view-service-health.md | Title: "How to check Microsoft 365 service health" + Title: How to check Microsoft 365 service health search.appverid: - BCS160 - IWA160 ms.assetid: 932ad3ad-533c-418a-b938-6e44e8bc33b0-description: "View the health status of Microsoft 365 services before you call support to see if there is an active service interruption." +description: View the health status of Microsoft 365 services before you call support to see if there is an active service interruption. # How to check Microsoft 365 service health |
| security | Android Configure | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/android-configure.md | Following privacy controls are available for configuring the data that is sent b |--|-| |Malware report |Admins can set up privacy control for malware report - If privacy is enabled, then Defender for Endpoint will not send the malware app name and other app details as part of the malware alert report | |Phish report |Admins can set up privacy control for phish report - If privacy is enabled, then Defender for Endpoint will not send the domain name and details of the unsafe website as part of the phish alert report |-|Vulnerability assessment of apps (Android-only) |By default only information about apps installed in the work profile is sent for vulnerability assessment. Admins can disable privacy to include personal apps| +|Vulnerability assessment of apps |By default only information about apps installed in the work profile is sent for vulnerability assessment. Admins can disable privacy to include personal apps| |Network Protection (preview)| Admins can enable or disable privacy in network protection - If enabled, then Defender will not send network details.| ### Configure privacy alert report |
| security | Collect Diagnostic Data Update Compliance | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/collect-diagnostic-data-update-compliance.md | search.appverid: met150 This article describes how to collect diagnostic data that can be used by Microsoft support and engineering teams to help troubleshoot issues you may encounter when using the Microsoft Defender Antivirus Assessment section in the Update Compliance add-in. +> [!NOTE] +> For performance-specific issues related to Microsoft Defender Antivirus, see: [Performance analyzer for Microsoft Defender Antivirus](tune-performance-defender-antivirus.md). + Before attempting this process, ensure you have read [Troubleshoot Microsoft Defender Antivirus reporting](troubleshoot-reporting.md), met all require prerequisites, and taken any other suggested troubleshooting steps. On at least two devices that are not reporting or showing up in Update Compliance, obtain the .cab diagnostic file by taking the following steps: On at least two devices that are not reporting or showing up in Update Complianc ## See also - [Troubleshoot Microsoft Defender Antivirus reporting](troubleshoot-reporting.md)+- [Performance analyzer for Microsoft Defender Antivirus](tune-performance-defender-antivirus.md) |
| security | Collect Diagnostic Data | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/collect-diagnostic-data.md | This article describes how to collect diagnostic data that can be used by Micros > [!NOTE] > As part of the investigation or response process, you can collect an investigation package from a device. Here's how: [Collect investigation package from devices](/windows/security/threat-protection/microsoft-defender-atp/respond-machine-alerts#collect-investigation-package-from-devices).+> +> For performance-specific issues related to Microsoft Defender Antivirus, see: [Performance analyzer for Microsoft Defender Antivirus](tune-performance-defender-antivirus.md). On at least two devices that are experiencing the same issue, obtain the .cab diagnostic file by taking the following steps: You can also specify where the diagnostic .cab file will be created using a Grou ## See also - [Troubleshoot Microsoft Defender Antivirus reporting](troubleshoot-reporting.md)+- [Performance analyzer for Microsoft Defender Antivirus](tune-performance-defender-antivirus.md) |
| security | Mac Install With Intune | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/mac-install-with-intune.md | Follow the instructions for [Onboarding blob](#onboarding-blob) from above, usin Download [**background_services.mobileconfig**](https://raw.githubusercontent.com/microsoft/mdatp-xplat/master/macos/mobileconfig/profiles/background_services.mobileconfig) from [our GitHub repository](https://github.com/microsoft/mdatp-xplat/tree/master/macos/mobileconfig/profiles). -Follow the instructions for [Onboarding blob](#onboarding-blob) from above, using "Defender for Endpoint Notifications" as profile name, and downloaded **notif.mobileconfig** as Configuration profile name. +Follow the instructions for [Onboarding blob](#onboarding-blob) from above, using "Defender for Background Services" as profile name, and downloaded **background_services.mobileconfig** as Configuration profile name. ### View Status |
| security | Manage Indicators | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/manage-indicators.md | search.appverid: met150 > > Want to experience Microsoft Defender for Endpoint? [Sign up for a free trial.](https://www.microsoft.com/WindowsForBusiness/windows-atp?ocid=docs-wdatp-automationexclusionlist-abovefoldlink) -Indicator of compromise (IoCs) matching is an essential feature in every endpoint protection solution. This capability gives SecOps the ability to set a list of indicators for detection and for blocking (prevention and response). +## Indicator of compromise (IoC) overview -Create indicators that define the detection, prevention, and exclusion of entities. You can define the action to be taken as well as the duration for when to apply the action as well as the scope of the device group to apply it to. +An Indicator of compromise (IoC) is a forensic artifact, observed on the network or host. An IoC indicates - with high confidence - a computer or network intrusion has occurred. IoCs are observable, which link them directly to measurable events. Some IoC examples include: -Currently supported sources are the cloud detection engine of Defender for Endpoint, the automated investigation and remediation engine, and the endpoint prevention engine (Microsoft Defender Antivirus). +- hashes of known malware +- signatures of malicious network traffic +- URLs or domains that are known malware distributors ++To halt additional compromise or prevent breaches of known IoCs, successful IoC tools should be able to detect all malicious data that is enumerated by the tool's rule set. +IoC matching is an essential feature in every endpoint protection solution. This capability gives SecOps the ability to set a list of indicators for detection and for blocking (prevention and response). ++Organizations can create indicators that define the detection, prevention, and exclusion of IoC entities. You can define the action to be taken as well as the duration for when to apply the action, and the scope of the device group to apply it to. ++### About Microsoft indicators ++As a general rule, you should only create indicators for known bad IoCs, or for any files / websites that should be explicitly allowed in your organization. For more information on the types of sites that MDE may block by default, see [Microsoft Defender SmartScreen overview](/windows/security/threat-protection/microsoft-defender-smartscreen/microsoft-defender-smartscreen-overview). ++False Positive (FP) refers to a SmartScreen false positive, Microsoft says it is malware / phish but it is actually a safe site, so customer wants to create an allow policy for this. ++You can also help drive improvements to Microsoft's security intelligence by submitting false positives, and suspicious or known-bad IoCs for analysis. If you believe a warning or block was incorrectly shown for a file or application, or if you believe an undetected file is malware, you can submit a file to Microsoft for review. For more information, see [Submit files for analysis](https://www.microsoft.com/en-us/wdsi/filesubmission/). ++#### IP/URL indicators ++There several reasons for using IP/URL indicators, such as unblocking users from a SmartScreen false positive (FP) or overriding a Web Content Filtering (WFC) block. ++You can use URL and IP indicators to manage site access. You can create interim IP and URL indicators to temporarily unblock users from a SmartScreen block. You may also have indicators that you keep for a long period of time to selectively bypass web content filtering blocks. ++Consider the case where you have a web content filtering categorization for a particular site that is correct. In this example, you have web content filtering set to block all social media, which is correct for your overall organizational goals. However, the marketing team has a real need to use a specific social media site for advertising and announcements. In that case, you can unblock the specific social media site using IP or URL indicators for the specific group (or groups) to use. ++See [Web protection](web-protection-overview.md) and [Web content filtering](web-content-filtering.md) ++#### File hash indicators ++In some cases, creating a new indicator for a newly identified file IoC - as an immediate stop-gap measure - might be appropriate to block files or even applications. However, using indicators to attempt to block an application may not provide the expected results as applications are typically composed of many different files. The preferred methods of blocking applications are to use [Windows Defender Application Control (WDAC)](/windows/security/threat-protection/windows-defender-application-control/wdac-and-applocker-overview) or AppLocker. ++Because each version of an application has a different file hash, using indicators to block hashes is not recommended. ++[Windows Defender Application Control (WDAC)](/windows/security/threat-protection/windows-defender-application-control/select-types-of-rules-to-create) ++#### Certificate indicators ++In some cases, there may be a specific certificate that has been used to sign a file or application that your organization would like to allow / block. Certificate indicators are supported in MDE, provided they are of the .CER or .PEM file format. See [Create indicators based on certificates](indicator-certificates.md) for more details. ++## IoC detection engines ++Currently, the supported Microsoft sources for IoCs are: ++- [Cloud detection engine](#cloud-detection-engine) of Defender for Endpoint +- [Automated investigation and remediation (AIR) engine](#automated-investigation-and-remediation-engine) in Microsoft Defender for Endpoint +- [Endpoint prevention engine](#endpoint-prevention-engine) (Microsoft Defender Antivirus) ## Cloud detection engine The same list of indicators is honored by the prevention agent. Meaning, if Micr The automated investigation and remediation behave the same. If an indicator is set to "Allow", Automated investigation and remediation will ignore a "bad" verdict for it. If set to "Block", Automated investigation and remediation will treat it as "bad". -The EnableFileHashComputation setting computes the file hash for the cert and file IoC during file scans. It supports IoC enforcement of hashes and certs belong to trusted applications. It will be concurrently enabled and disabled with the allow or block file setting. EnableFileHashComputation is enabled manually through Group Policy, and is disabled by default. +The `EnableFileHashComputation` setting computes the file hash for the cert and file IoC during file scans. It supports IoC enforcement of hashes and certs belong to trusted applications. It will be concurrently enabled and disabled with the allow or block file setting. `EnableFileHashComputation` is enabled manually through Group Policy, and is disabled by default. ++## Enforcement types for Indicators When creating a new indicator (IoC), one or more of the following actions are available: -- Allow ΓÇô the IoC will be allowed to run on your devices.-- Audit ΓÇô an alert will be triggered when the IoC runs.-- Warn ΓÇô the IoC will prompt a warning that the user can bypass -- Block execution - the IoC will not be allowed to run.-- Block and remediate - the IoC will not be allowed to run and a remediation action will be applied to the IoC.+- **Allow** ΓÇô the IoC will be allowed to run on your devices. +- **Audit** ΓÇô an alert will be triggered when the IoC runs. +- **Warn** ΓÇô the IoC will prompt a warning that the user can bypass +- **Block execution** - the IoC will not be allowed to run. +- **Block and remediate** - the IoC will not be allowed to run and a remediation action will be applied to the IoC. >[!NOTE]-> Using Warn mode will prompt your users with a warning if they open a risky app. The prompt won't block them from using the app, but you can provide a custom message and links to a company page that describes appropriate usage of the app. Users can still bypass the warning and continue to use the app if they need. For more information, see [Govern apps discovered by Microsoft Defender for Endpoint](/cloud-app-security/mde-govern). +> Using Warn mode will prompt your users with a warning if they open a risky app or website. The prompt won't block them from allowing the application or website to run, but you can provide a custom message and links to a company page that describes appropriate usage of the app. Users can still bypass the warning and continue to use the app if they need. For more information, see Govern apps discovered by Microsoft Defender for Endpoint. You can create an indicator for: - [Files](indicator-file.md)-- [IP addresses, URLs/domains](indicator-ip-domain.md)+- [IP addresses](indicator-ip-domain.md) +- [URLs/domains](indicator-ip-domain.md) - [Certificates](indicator-certificates.md) The table below shows exactly which actions are available per indicator (IoC) type: | IoC type | Available actions | |:|:|-| [Files](indicator-file.md) | Allow <br> Audit <br> Block and remediate | -| [IP addresses](indicator-ip-domain.md) | Allow <br> Audit <br> Block execution <br> Warn | -| [URLs and domains](indicator-ip-domain.md) | Allow <br> Audit <br> Block execution<br> Warn | +| [Files](indicator-file.md) | Allow <br> Audit <br> Warn <br> Block execution <br> Block and remediate | +| [IP addresses](indicator-ip-domain.md) | Allow <br> Audit <br> Warn <br> Block execution | +| [URLs and domains](indicator-ip-domain.md) | Allow <br> Audit <br> Warn <br> Block execution | | [Certificates](indicator-certificates.md) | Allow <br> Block and remediate | The functionality of pre-existing IoCs will not change. However, the indicators were renamed to match the current supported response actions: The functionality of pre-existing IoCs will not change. However, the indicators The IoC API schema and the threat ids in advance hunting have been updated to align with the renaming of the IoC response actions. The API scheme changes apply to all IoC Types. -> [!Note] +> [!NOTE] +> > There is a limit of 15,000 indicators per tenant. File and certificate indicators do not block [exclusions defined for Microsoft Defender Antivirus](/windows/security/threat-protection/microsoft-defender-antivirus/configure-exclusions-microsoft-defender-antivirus). Indicators are not supported in Microsoft Defender Antivirus when it is in passive mode. > > The format for importing new indicators (IoCs) has changed according to the new updated actions and alerts settings. We recommend downloading the new CSV format that can be found at the bottom of the import panel. |
| security | Troubleshoot Performance Issues | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/troubleshoot-performance-issues.md | You can also provide additional logs to your submission to Microsoft support by - [Capture process logs using Process Monitor](#capture-process-logs-using-process-monitor) - [Capture performance logs using Windows Performance Recorder](#capture-performance-logs-using-windows-performance-recorder) +For performance-specific issues related to Microsoft Defender Antivirus, see: [Performance analyzer for Microsoft Defender Antivirus](tune-performance-defender-antivirus.md) + ## Check with vendor for antivirus exclusions If you can readily identify the software affecting system performance, go to the software vendor's knowledge base or support center. Search if they have recommendations about antivirus exclusions. If the vendor's website does not have them, you can open a support ticket with them and ask them to publish one. The command-line tool *wpr.exe* is part of the operating system starting with Wi - [Collect Microsoft Defender Antivirus diagnostic data](collect-diagnostic-data.md) - [Configure and validate exclusions for Microsoft Defender Antivirus scans](configure-exclusions-microsoft-defender-antivirus.md)+- [Performance analyzer for Microsoft Defender Antivirus](tune-performance-defender-antivirus.md) |
| security | Troubleshooting Mode Scenarios | https://github.com/MicrosoftDocs/microsoft-365-docs/commits/public/microsoft-365/security/defender-endpoint/troubleshooting-mode-scenarios.md | +For troubleshooting performance-specific issues related to Microsoft Defender Antivirus, see: [Performance analyzer for Microsoft Defender Antivirus](tune-performance-defender-antivirus.md). + ## Scenario 1: Unable to install application If you want to install an application but receive an error message that Microsoft Defender Antivirus and tamper protection is on, follow the steps below to troubleshoot the issue. |